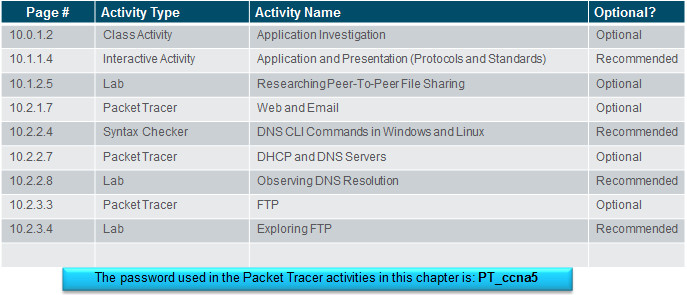
Instructor Planning Guide
Activities
What activities are associated with this chapter?

Assessment
Students should complete Chapter 10, “Assessment” after completing Chapter 10.
Quizzes, labs, Packet Tracers and other activities can be used to informally assess student progress.
Sections & Objectives
10.1 Application Layer Protocols
Explain the operation of the application layer in providing support to end-user applications.
Explain how the functions of the application layer, session layer, and presentation layer work together to provide network services to end user applications
Explain how common application layer protocols interact with end user applications.
10.2 Well-Known Application Protocols and Services
Explain how well-known TCP/IP application layer protocols operate.
Explain how web and email protocols operate.
Explain how DNS and DHCP operate.
Explain how file transfer protocols operate.
Chapter 10: Application Layer
10.1 – Application Layer Protocols
10.1.1 – Application, Presentation, and Session
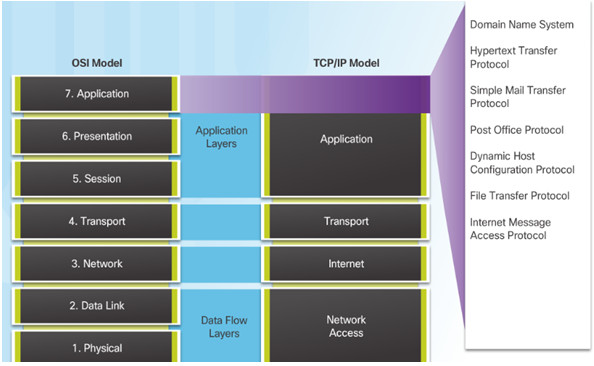
10.1.1.1– Application Layer
Application Layer:
- Closest to the end user.
- Used to exchange data between programs running on the source and destination hosts.
10.1.1.2– Presentation and Session Layer
Presentation Layer function:
- Formatting data at the source device into a compatible form for the receiving device.
- Compressing data.
- Encrypting data.
Session Layer Function
- Create and maintain dialogs between source and destination applications.
10.1.1.3– TCP/IP Application Layer Protocols
Post Office Protocol (POP) TCP 110 – Enables clients to retrieve email from a mail server.
Internet Message Access Protocol (IMAP) TCP 143 – Enables clients to retrieve email from a mail server, maintains email on server.
File Transfer Protocol (FTP) TCP 20 and 21 – Reliable, connection-oriented, and acknowledged file delivery protocol.
Trivial File Transfer Protocol (TFTP) UDP 69 – simple connectionless file transfer protocol.
Hypertext Transfer Protocol (HTTP) TCP 80, 8080 – Set of rules for exchanging text, graphic images, etc. on the World Wide Web.
Hypertext Transfer Protocol Secure (HTTPS) TCP, UDP 443 – Uses encryption and authentication to secure communication.
Domain Name Server (DNS) TCP,UDP 53 – Translates domain names, such as cisco.com, into IP addresses.
(BOOTP) – Bootstrap Protocol – BOOTP is being superseded by DHCP.
Dynamic Host Configuration Protocol (DHCP) UDP client 68, server 67 – Dynamically assigns IP addresses to client stations at start-up.
Simple Mail Transport Protocol (SMTP) TCP 25 – Enables clients to send email to a mail server.
10.1.2 – How Application Protocols Interact with End-User Applications
10.1.2.1– Client-Server Model
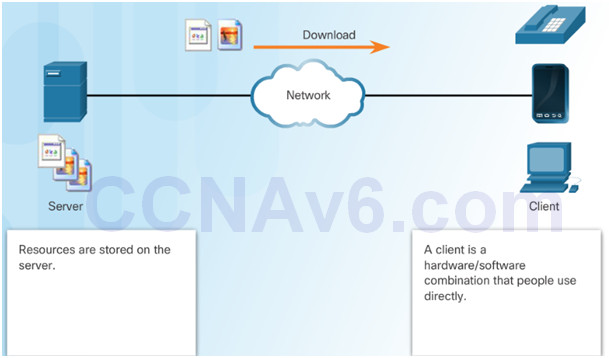
Client and server processes are considered to be in the application layer.
Application layer protocols describe the format of the requests and responses between clients and servers.
Example of a client-server network is using an ISP’s email service to send, receive and store email.
10.1.2.2– Peer-to-Peer Networks
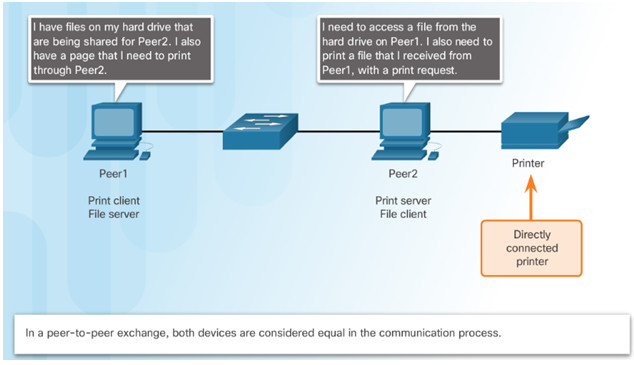
Data is accessed from a peer device without the use of a dedicated server.
Each device (known as a peer) can function as both a server and a client.
10.1.2.3 – Peer-to-Peer Applications
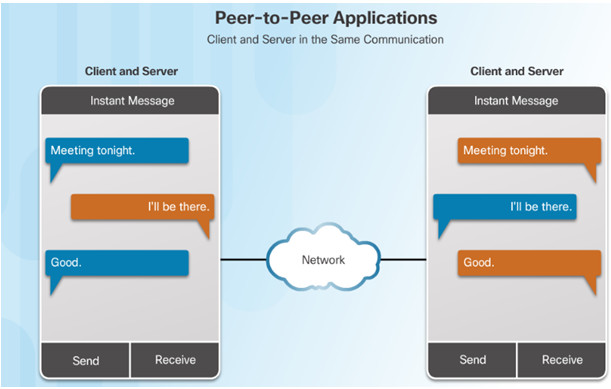
A P2P application allows a device to act as both a client and a server within the same communication.
P2P applications require that each end device provide a user interface and run a background service.
10.1.2.4 – Common P2P Applications
Common P2P networks include:
- G2
- Bitcoin
- BitTorrent
- eDonkey
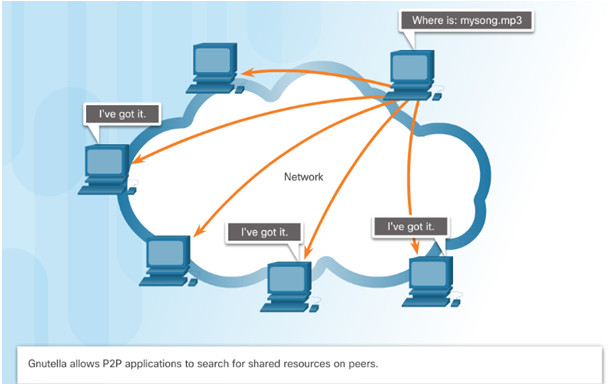
Some P2P applications are based on the Gnutella protocol, where each user shares whole files with other users.
Many P2P applications allow users to share pieces of many files with each other at the same time –this is BitTorrent technology.
10.1.2.5 – Lab – Researching Peer-to-Peer File Sharing
10.1.2.5 Lab – Researching Peer-to-Peer File Sharing

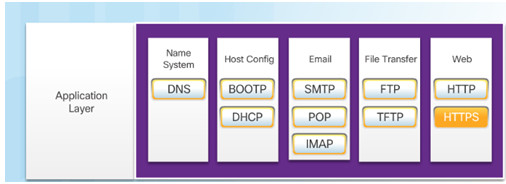
10.2 – Well-Known Application Layer Protocols and Services
10.2.1 – Web and Email Protocols
10.2.1.1 – Hypertext Transfer Protocol and Hypertext Markup Language
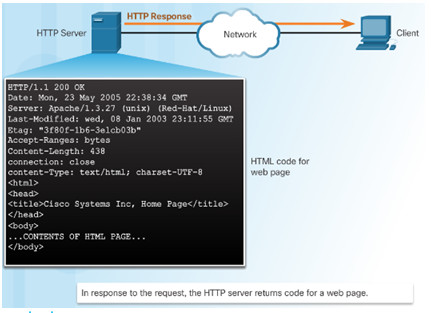
When a web address or uniform resource locator (URL) is typed into a web browser, the web browser establishes a connection to the web service running on the server, using the HTTP protocol.
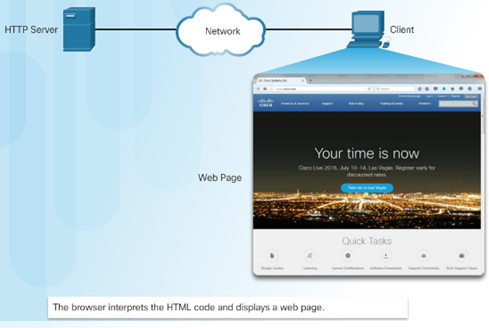
10.2.1.2 – HTTP and HTTPS
HTTP is a request/response protocol.
Three common HTTP message types are:
- GET – A client request for data.
- POST – Uploads data files to the web server.
- PUT – Uploads resources or content to the web server.
HTTP Secure (HTTPS) protocol uses encryption and authentication to secure data.
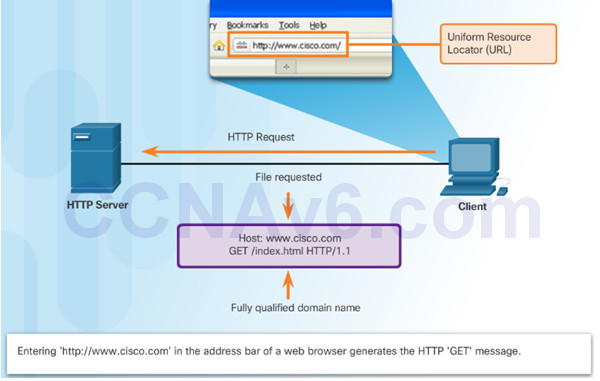
10.2.1.3 – Email Protocols
Email clients communicate with mail servers to send and receive email.
Mail servers communicate with other mail servers to transport messages from one domain to another.
Three protocols for email:
- Simple Mail Transfer Protocol (SMTP) to send email.
- Post Office Protocol (POP) to retrieve email.
- Internet Message Access Protocol (IMAP) to retrieve email.
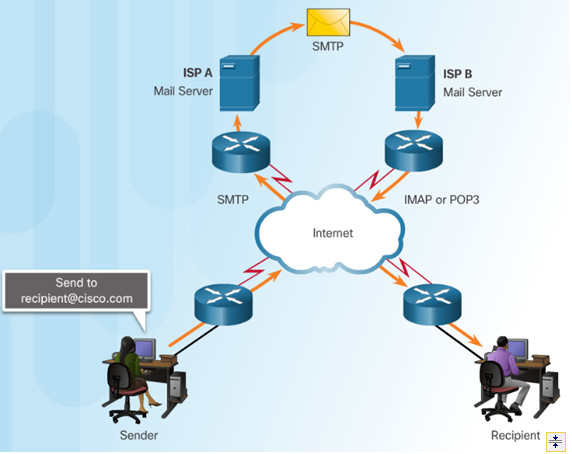
10.2.1.4 – SMTP Operation
SMTP is used to send email
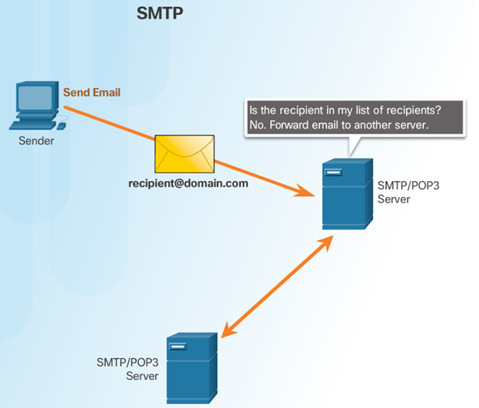
10.2.1.5– POP Operation
POP is used to retrieve email from a mail server.
Email is downloaded from the server to the client and then deleted on the server.
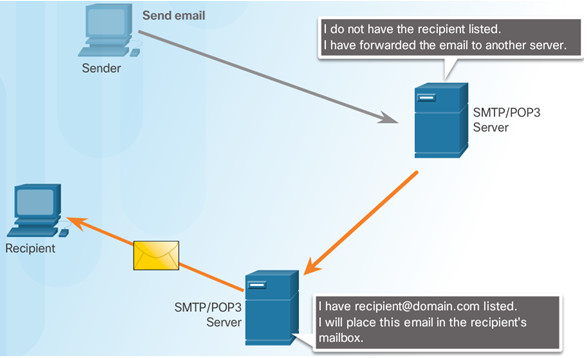
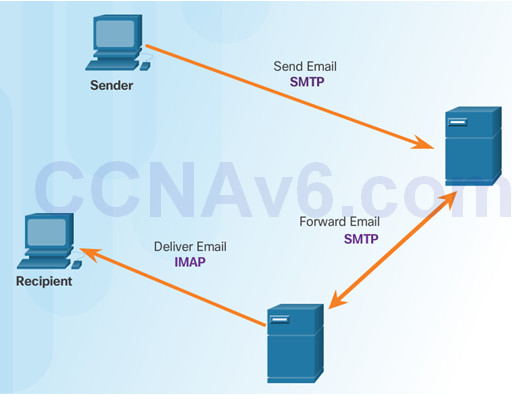
10.2.1.6 – IMAP Operation
IMAP is used to retrieve mail from a mail server.
Copies of messages are downloaded from the server to the client and the original messages are stored on the server.
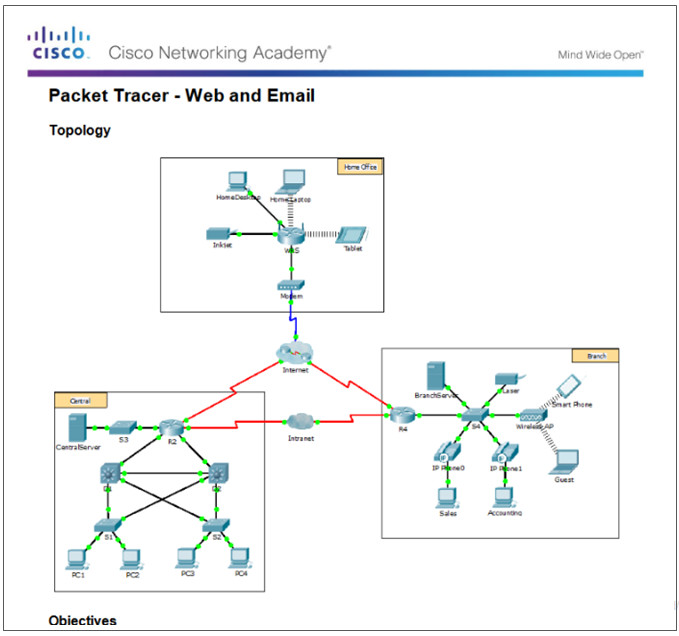
10.2.1.7 – Packet Tracer – Web and Email
10.2.1.7 Packet Tracer – Web and Email
10.2.2 – IP Addressing Services
10.2.2.1 – Domain Name Service
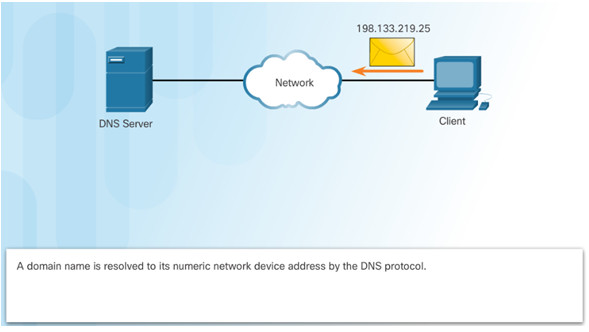
Domain names convert the numeric address into a simple, recognizable name.
The DNS protocol defines an automated service that matches resource names with the required numeric network address.
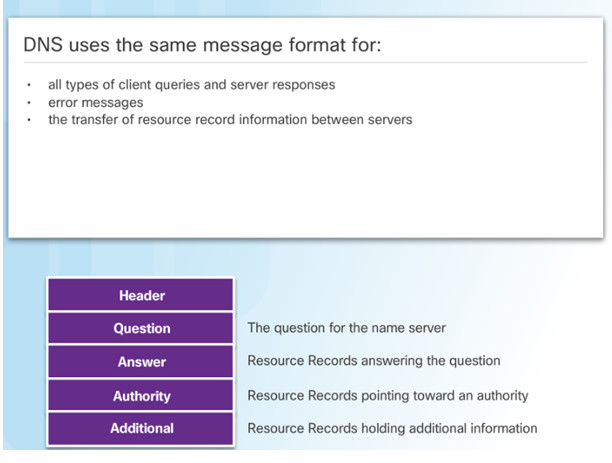
10.2.2.2 – DNS Message Format
When a client makes a query, the server’s DNS process first looks at its own records to resolve the name.
If unable to resolve, it contacts other servers to resolve the name.
The server temporarily stores the numbered address in the event that the same name is requested again.
The ipconfig /displaydns command displays all of the cached DNS entries on a Windows PC.
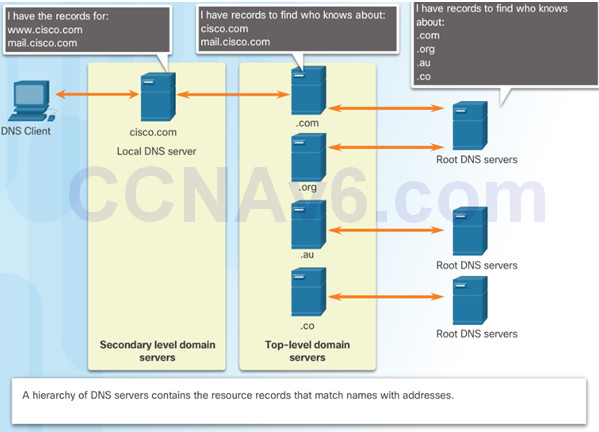
10.2.2.3 – DNS Hierarchy
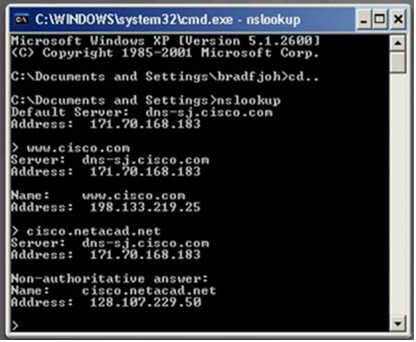
10.2.2.4 – The nslookup Command
Nslookup – a utility that allows a user to manually query the name servers to resolve a given host.
Can also be used to troubleshoot name resolution issues and to verify the current status of the name servers.
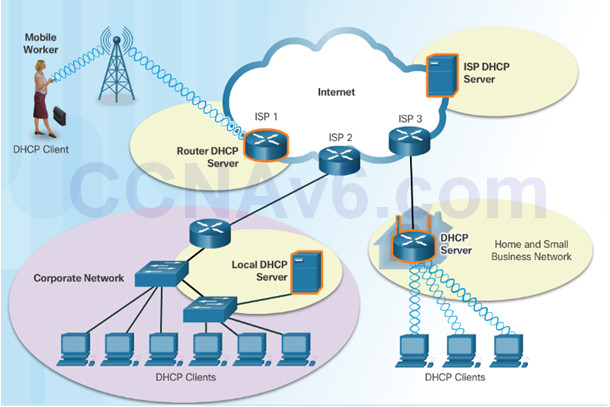
10.2.2.5 – Dynamic Host Configuration Protocol
The Dynamic Host Configuration Protocol (DHCP) for IPv4 automates the assignment of IPv4 addresses, subnet masks, gateways, and other parameters.
DHCP-distributed addresses are leased for a set period of time, then returned to pool for reuse.
DHCP is usually employed for end user devices. Static addressing is used for network devices, such as gateways, switches, servers, and printers.
DHCPv6 (DHCP for IPv6) provides similar services for IPv6 clients.
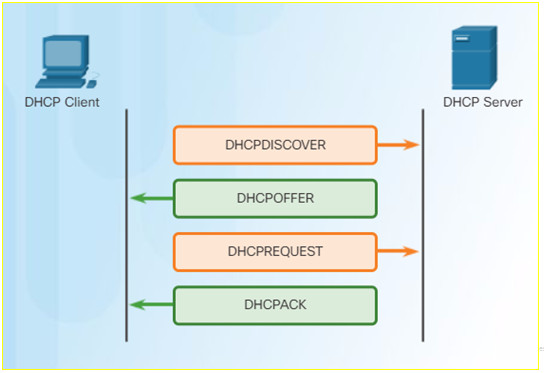
10.2.2.6 – DHCP Operation
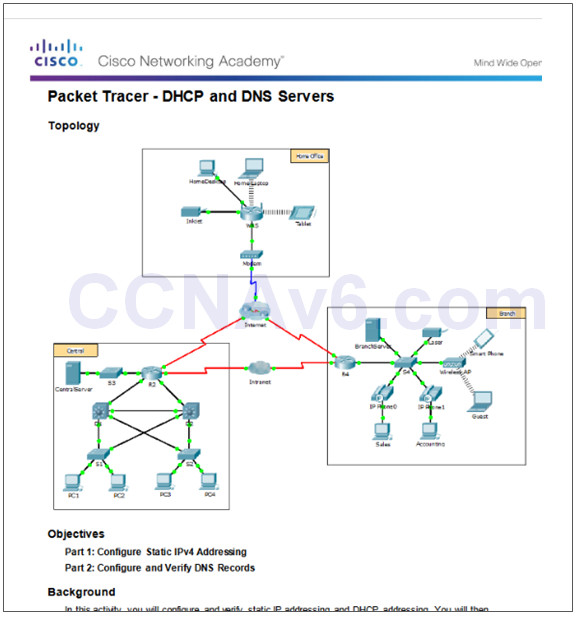
10.2.2.7 – Packet Tracer – DHCP and DNS Servers
10.2.2.7 Packet Tracer – DNS and DHCP
10.2.2.8 – Lab – Observing DNS Resolution
10.2.2.8 Lab – Observing DNS Resolution
10.2.3 – File Sharing Services
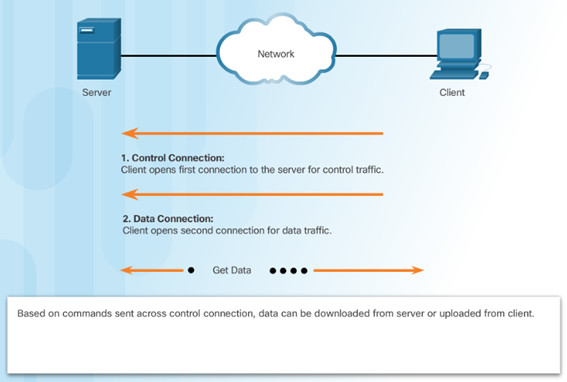
10.2.3.1 – File Transfer Protocol
FTP requires two connections between the client and the server, one for commands and replies, the other for the actual file transfer:
- The client establishes the first connection to the server for control traffic using TCP port 21.
- The client establishes the second connection to the server for the actual data transfer using TCP port 20.
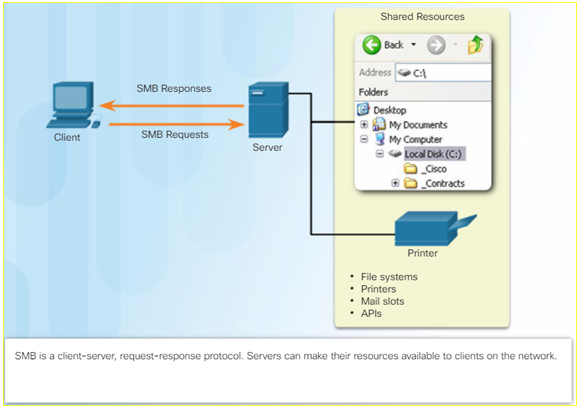
10.2.3.2 – Server Message Block
The Server Message Block (SMB) is a client/server file sharing protocol:
- SMB file-sharing and print services have become the mainstay of Microsoft networking.
- Clients establish a long-term connection to servers and can access the resources on the server as if the resource is local to the client host.
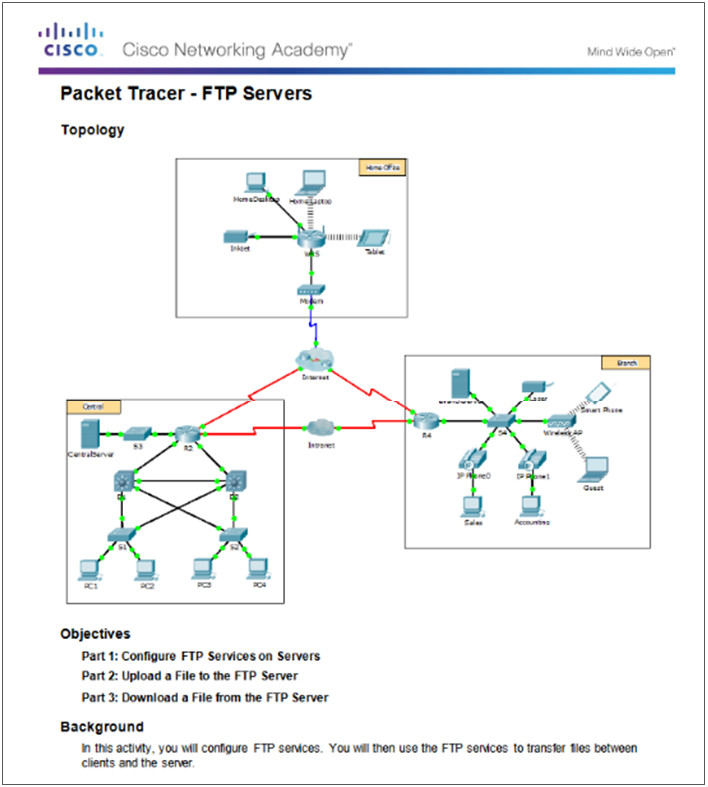
10.2.3.3 – Packet Tracer – FTP
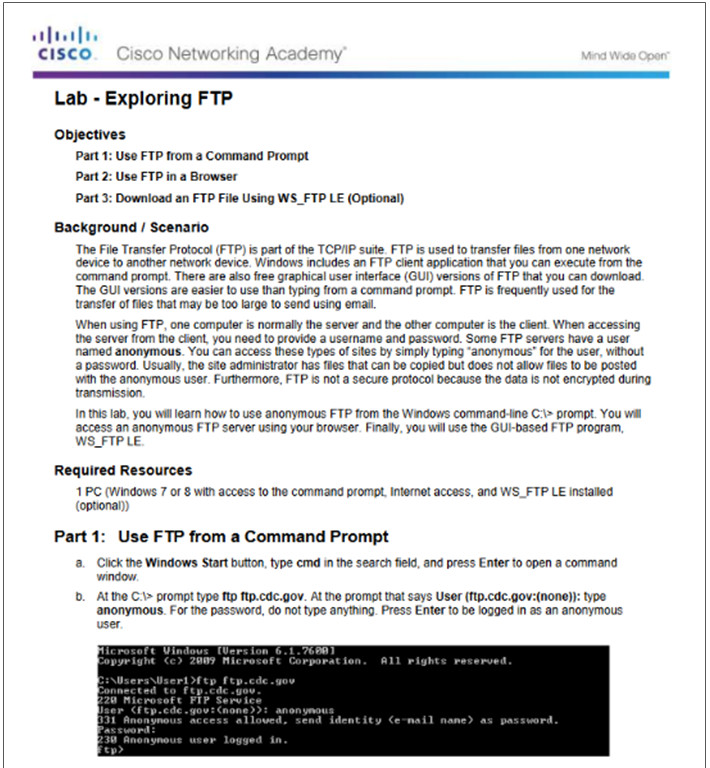
10.2.3.4 – Lab – Exploring FTP
10.3 – Summary
10.3.1 – Conclusion
10.3.1.1 Class Activity – Make It Happen!
10.3.1.1 Class Activity – Make It Happen!
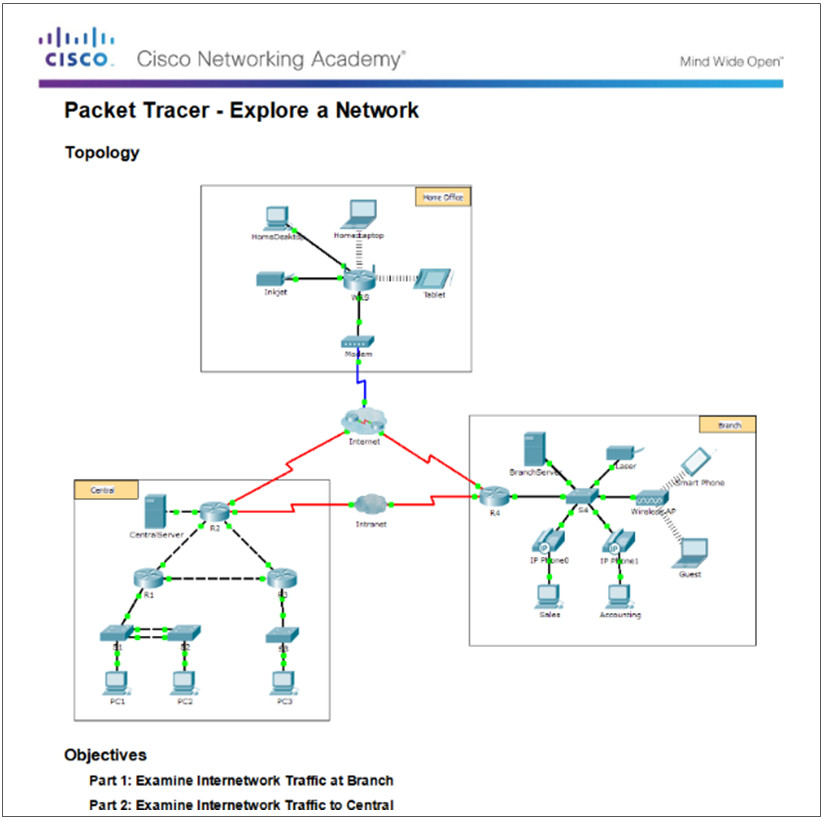
10.3.1.2 – Packet Tracer – Explore a Network
10.3.1.2 Packet Tracer – Explore a Network
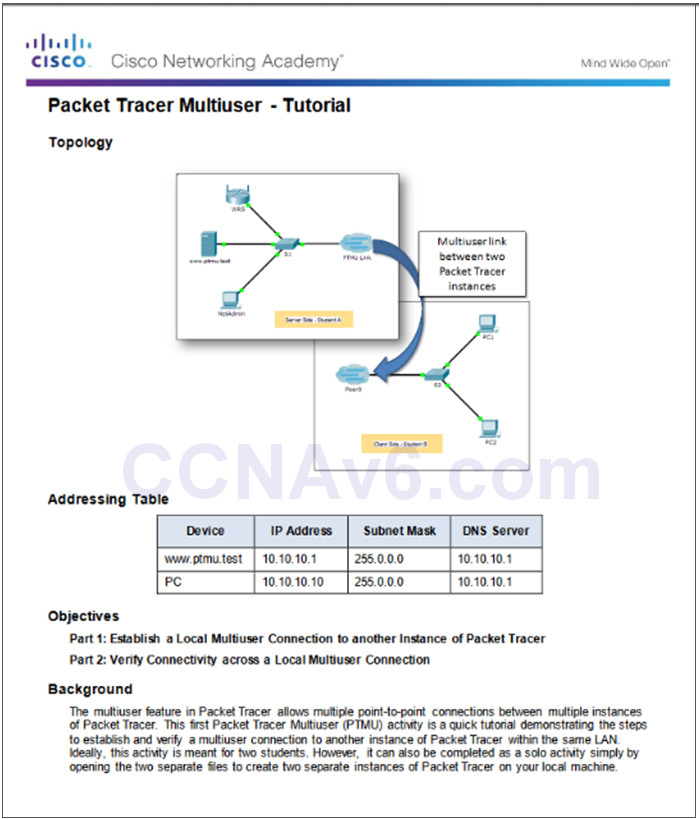
10.3.1.3 – Packet Tracer – Multiuser – Tutorial
10.3.1.3 Packet Tracer – Multiuser – Tutorial
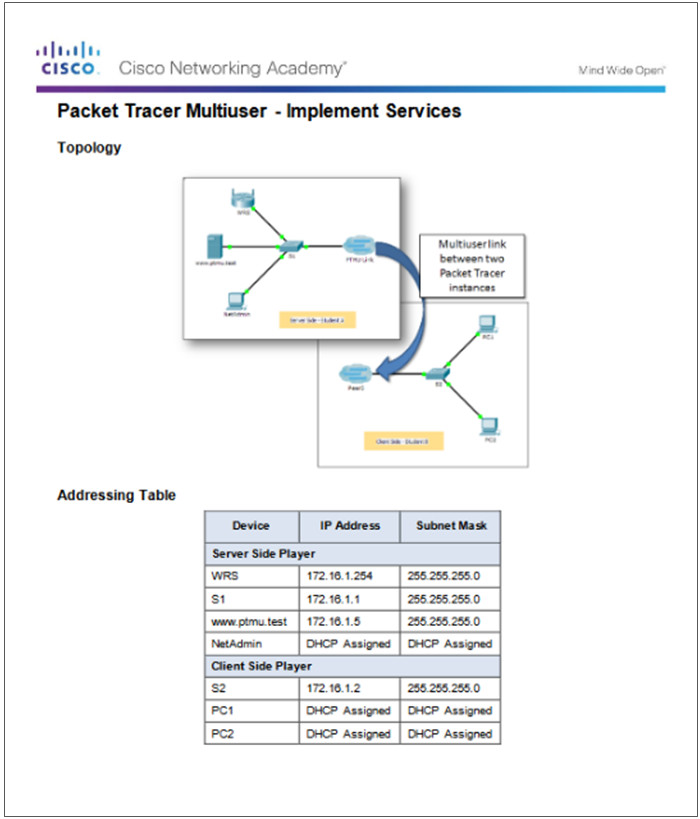
10.3.1.4 – Packet Tracer Multiuser – Implement Services
10.3.1.4 Packet Tracer Multiuser – Implement Services
10.3.1.4 – Chapter 10: Application Layer
Explain the operation of the application layer in providing support to end-user applications.
Explain how well-known TCP/IP application layer protocols operate.
New Terms and Commands
Bootstrap Protocol (BOOTP)
Simple Mail Transfer Protocol (SMTP)
Post Office Protocol (POP)
Internet Message Access Protocol (IMAP)
File Transfer Protocol (FTP)
Trivial File Transfer Protocol (TFTP)
client-server
Server Message Block (SMB)
