Instructor Planning Guide
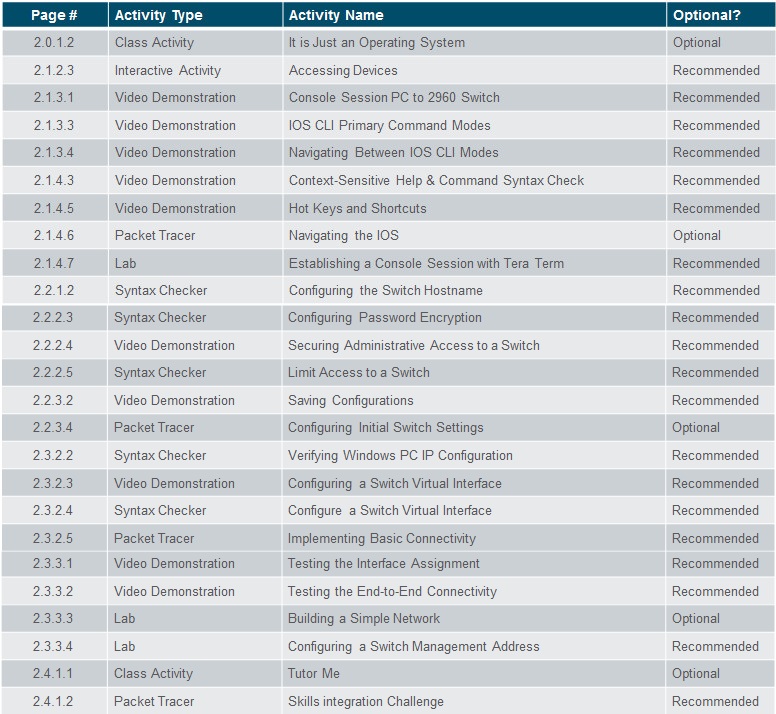
Activities
What activities are associated with this chapter?
Assessment
Students should complete Chapter 2, “Assessment” after completing Chapter 2.
Quizzes, labs, Packet Tracers and other activities can be used to informally assess student progress.
Sections & Objectives
2.1 IOS Bootcamp
♦ Explain the features and functions of the Cisco IOS Software.
♦ Explain the purpose of Cisco IOS.
♦ Explain how to access a Cisco IOS device for configuration purposes.
♦ Explain how to navigate Cisco IOS to configure network devices.
♦ Describe the command structure of Cisco IOS software.
2.2 Basic Device Configuration
♦ Configure initial settings on a network device using the Cisco IOS Software.
♦ Configure hostnames on a Cisco IOS device using the CLI.
♦ Use Cisco IOS commands to limit access to device configurations.
♦ Use IOS commands to save the running configuration.
2.3 Address Schemes
♦ Given an IP addressing scheme, configure IP address parameters on devices to provide end-to-end connectivity in a small to medium-sized business network.
♦ Explain how devices communicate across network media.
♦ Configure a host device with an IP address.
♦ Verify connectivity between two end devices.
Chapter 2: Configure a Network Operating System
2.1 – IOS Bootcamp
2.1.1 – Cisco IOS
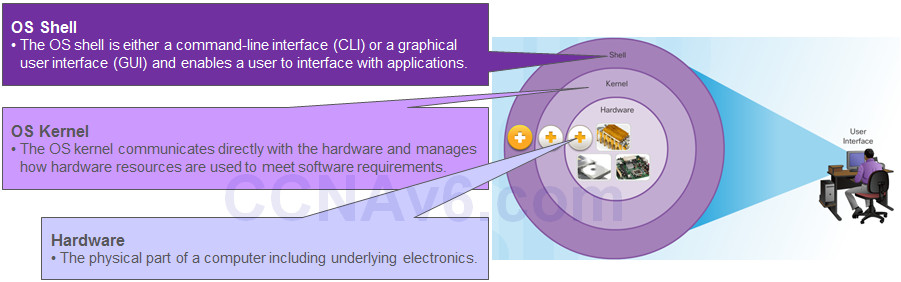
2.1.1.1 – Operating System
All electronic devices require an operating system.
♦ Windows, Mac, and Linux for PCs and laptops
♦ Apple iOS and Android for smart phones and tablets
♦ Cisco IOS for network devices (e.g., switches, routers, wireless AP, firewall, …).
2.1.1.2 – Purpose of OS
Using a GUI enables a user to:
♦ Use a mouse to make selections and run programs
♦ Enter text and text-based commands
Using a CLI on a Cisco IOS switch or router enables a network technician to:
♦ Use a keyboard to run CLI-based network programs
♦ Use a keyboard to enter text and text-based commands
There are many distinct variations of Cisco IOS:
♦ IOS for switches, routers, and other Cisco networking devices
♦ IOS numbered versions for a given Cisco networking devices
All devices come with a default IOS and feature set. It is possible to upgrade the IOS version or feature set.
An IOS can be downloaded from cisco.com. However, a Cisco Connection Online (CCO) account is required.
Note: The focus of this course will be on Cisco IOS Release 15.x.
2.1.2 – Cisco IOS Access
2.1.2.1 – Access Methods
The three most common ways to access the IOS are:
♦ Console port – Out-of-band serial port used primarily for management purposes such as the initial configuration of the router.
♦ Secure Shell (SSH) – Inband method for remotely and securely establishing a CLI session over a network. User authentication, passwords, and commands sent over the network are encrypted. As a best practice, use SSH instead of Telnet whenever possible.
♦ Telnet – Inband interfaces remotely establishing a CLI session through a virtual interface, over a network. User authentication, passwords, and commands are sent over the network in plaintext.
Note: The AUX port is an on older method of establishing a CLI session remotely via a telephone dialup connection using a modem.
2.1.2.2 – Terminal Emulation Programs
Regardless of access method, a terminal emulation program will be required. Popular terminal emulation programs include PuTTY, Tera Term, SecureCRT, and OS X Terminal.
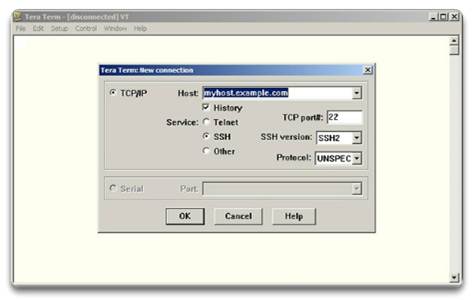
2.1.3 – Navigate the IOS
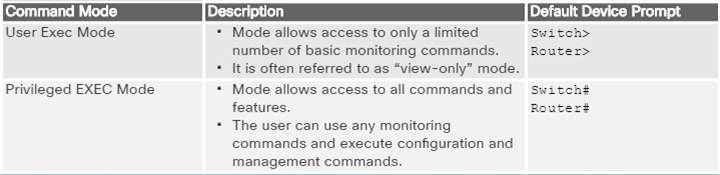
2.1.3.1 – Cisco IOS Modes of Operation
The Cisco IOS modes use a hierarchical command structure.
Each mode has a distinctive prompt and is used to accomplish particular tasks with a specific set of commands that are available only to that mode.
2.1.3.2 – Primary Command Modes
The user EXEC mode allows only a limited number of basic monitoring commands.
♦ Often referred to as “view-only” mode.
♦ By default, there is no authentication required to access the user EXEC mode but it should be secured.
The privileged EXEC mode allows the execution of configuration and management commands.
♦ Often referred to as “enable mode” because it requires the enable user EXEC command.
♦ By default, there is no authentication required to access the user EXEC mode but it should be secured.
2.1.3.3 – Configuration Command Modes
The primary configuration mode is called global configuration or simply, global config.
♦ Use the configure terminal command to access.
♦ Changes made affect the operation of the device.
Specific sub configuration modes can be accessed from global configuration mode. Each of these modes allows the configuration of a particular part or function of the IOS device.
♦ Interface mode – to configure one of the network interfaces.
♦ Line mode – to configure the console, AUX, Telnet, or SSH access.
2.1.3.4 – Navigate Between IOS Modes
Various commands are used to move in and out of command prompts:
♦ To move from user EXEC mode to privileged EXEC mode, use the enable command.
♦ Use return to user EXEC mode, use the disable command.
Various methods can be used to exit / quit configuration modes:
♦ exit – Used to move from a specific mode to the previous more general mode, such as from interface mode to global config.
♦ end – Can be used to exit out of global configuration mode regardless of which configuration mode you are in.
♦ ^z – Works the same as end.
The following provides an example of navigating between IOS modes:
♦ Enter privileged EXEC mode using the enable command.
♦ Enter global config mode using the configure terminal command.
♦ Enter interface sub-config mode using the interface fa0/1 command.
♦ Exit out of each mode using the exit command.
♦ The remainder of the configuration illustrates how you can exit a sub-config mode and return to privileged EXEC mode using either the end or ^Z key combination.
2.1.4 – The Command Structure
2.1.4.1 – Basic IOS Command Structure
A Cisco IOS device supports many commands. Each IOS command has a specific format or syntax and can only be executed at the appropriate mode.
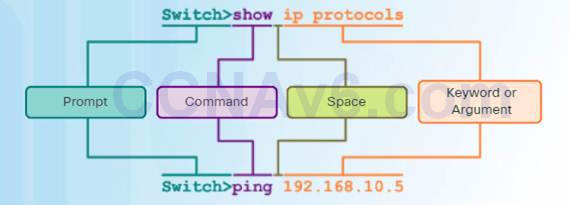
The syntax for a command is the command followed by any appropriate keywords and arguments.
♦ Keyword – a specific parameter defined in the operating system (in the figure, ip protocols)
♦ Argument – not predefined; a value or variable defined by the user (in the figure, 192.168.10.5)
After entering each complete command, including any keywords and arguments, press the Enter key to submit the command to the command interpreter.
2.1.4.2 – IOS Command Syntax
To determine the keywords and arguments required for a command, refer to the command syntax
♦ Refer to the following table when looking at command syntax.

Examples:
♦ description string – The command is used to add a description to an interface. The string argument is text entered by the administrator such as description Connects to the main headquarter office switch.
♦ ping ip-address – The command is ping and the user-defined argument is the ip-address of the destination device such as in ping 10.10.10.5
2.1.4.3 – IOS Help Features
IOS Context-Sensitive Help:
♦ Context-sensitive help provides a list of commands and the arguments associated with those commands
within the context of the current mode.
♦ To access context-sensitive help, enter a question mark ?, at any prompt.
IOS Command Syntax Check:
♦ The command line interpreter checks an entered command from left to right to determine what action is being requested.
♦ If the interpreter understands the command, the requested action is executed and the CLI returns to the appropriate prompt.
♦ If the interpreter discovers an error, the IOS generally provides feedback such as “Ambiguous command”, “Incomplete command”, or “Incorrect command”.
2.1.4.4 – Hot Keys and Shortcuts
Commands and keywords can be shortened to the minimum number of characters that identify a unique selection.
For example, the configure command can be shortened to conf because configure is the only command that begins with conf.
♦ An even shorter version of con will not work because more than one command begins with con.
♦ Keywords can also be shortened.
2.1.4.5 – Video Demonstration – Hot Keys and Shortcuts
The IOS CLI support the following hotkeys:
♦ Down Arrow – Allows the user to scroll through command history.
♦ Up Arrow – Allows the user to scroll backward through commands.
♦ Tab – Completes the remainder of a partially entered command.
♦ Ctrl-A – Moves to the beginning of the line.
♦ Ctrl-E – Moves to the end of the line.
♦ Ctrl-R – Redisplays a line.
♦ Ctrl-Z – Exits the configuration mode and returns to user EXEC.
♦ Ctrl-C – Exits the configuration mode or aborts the current command.
♦ Ctrl-Shift-6 – Allows the user to interrupt an IOS process (e.g., ping).
2.1.4.6 – Packet Tracer – Navigating the IOS
2.1.4.6 Packet Tracer – Navigating the IOS
2.1.4.7 – Lab – Establishing a Console Session with Tera Term
2.1.4.7 Lab – Establishing a Console Session with Tera Term
2.2 – Basic Device Configuration
2.2.1 – Hostnames
2.2.1.1 – Device Names
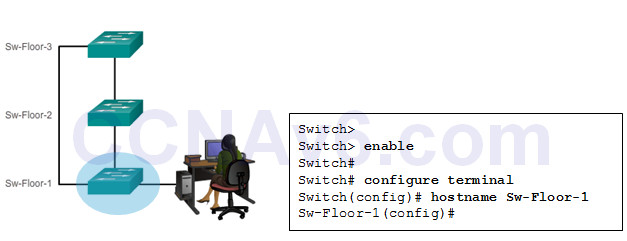
The first step when configuring a switch is to assign it a unique device name, or hostname.
♦ Hostnames appear in CLI prompts, can be used in various authentication processes between devices, and should be used on topology diagrams.
♦ Without a hostname, network devices are difficult to identify for configuration purposes.
2.2.1.2 – Configure Hostnames
Once the naming convention has been identified, the next step is to apply the names to the devices using the CLI.
The hostname name global configuration command is used to assign a name.
2.2.2 – Limit Access to Device Configurations
2.2.2.1 – Secure Device Access
Step 1 – Secure network devices to physically limit access by placing them in wiring closets and locked racks.
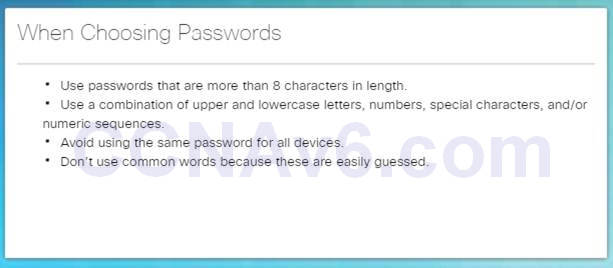
Step 2 – Enforce secure passwords as passwords are the primary defense against unauthorized access to network devices.
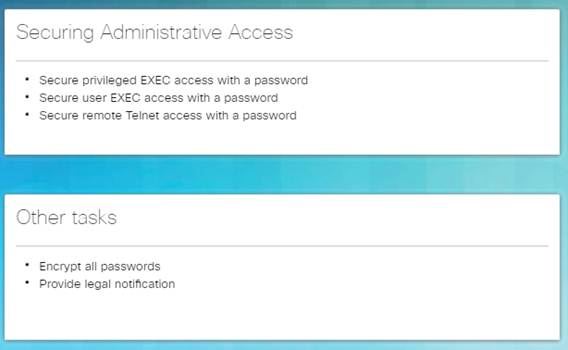
Limit administrative access as follows.
Use strong password as suggested.
2.2.2.2 – Configure Passwords
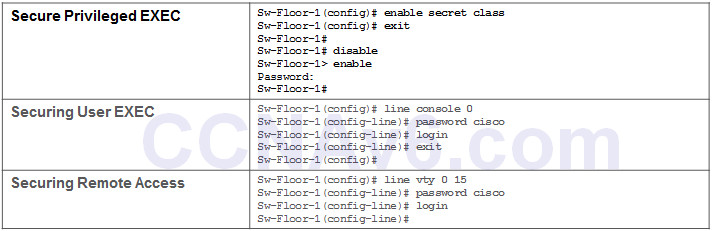
Secure privileged EXEC access using the enable secret password global config command.
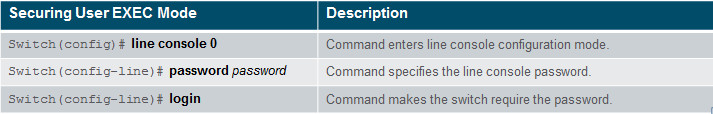
Secure user EXEC access by configuring the line console as follows:
Secure remote Telnet or SSH access by configuring the Virtual terminal (VTY) lines as follows:
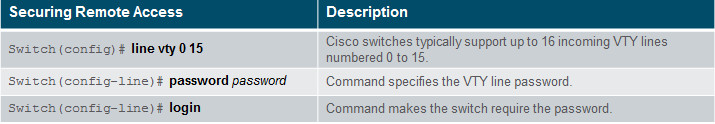
2.2.2.3 – Encrypt Passwords
The startup-config and running-config files display most passwords in plaintext. This is a security threat because anyone can see the passwords if they have access to these files.
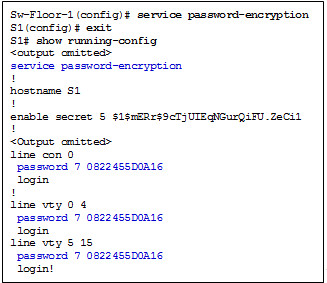
Use the service password-encryption global config command to encrypt all passwords.
♦ The command applies weak encryption to all unencrypted passwords.
♦ However, it does stop “shoulder surfing”.
2.2.2.4 – Banner Messages
Banners are messages that are displayed when someone attempts to gain access to a device. Banners are an important part of the legal process in the event that someone is prosecuted for breaking into a device.
Configured using the banner motd delimiter message delimiter command from global configuration mode. The delimiting character can be any character as long as it isunique and does not occur in the message (e.g., #$%^&*)
2.2.2.5– Syntax Checker – Limiting Access to a Switch
Encrypt all passwords.
Sw-Floor-1(config)# service password-encryption Sw-Floor-1(config)#
Secure the privileged EXEC access with the password Cla55.
Sw-Floor-1(config)# enable secret Cla55 Sw-Floor-1(config)#
Secure the console line. Use the password Cisc0 and allow login.
Sw-Floor-1(config)# line console 0 Sw-Floor-1(config-line)# password Cisc0 Sw-Floor-1(config-line)# login SW-Floor-1(config-line)# exit Sw-Floor-1(config)#
Secure the first 16 VTY lines. Use the password Cisc0 and allow login.
Sw-Floor-1(config)# line vty 0 15 Sw-Floor-1(config-line)# password Cisc0 Sw-Floor-1(config-line)# login Sw-Floor-1(config-line)# end Sw-Floor-1#
2.2.3 – Save Configurations
2.2.3.1 – Save the Running Configuration File
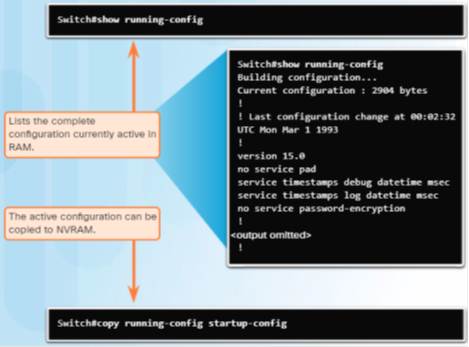
Cisco devices use a running configuration file and a startup configuration file.
The running configuration file is stored in RAM and contains the current configuration on a Cisco IOS device.
♦ Configuration changes are stored in this file.
♦ If power is interrupted, the running config is lost.
♦ Use the show startup-config command to display contents.
The startup config file is stored in NVRAM and contains the configuration that will be used by the device upon reboot.
♦ Typically the running config is saved as the startup config.
♦ If power is interrupted, it is not lost or erased.
♦ Use the show running-config command to display contents.
Use the copy running-config startup-config command to save the running configuration.
2.2.3.2 – Alter the Running Configuration
If configuration changes do not have the desired effect, they can be removed individually or the device can be rebooted to the last saved configuration using the reload privileged EXEC mode command.
♦ The command restores the startup-config.
♦ A prompt will appear to ask whether to save the changes. To discard the changes, enter n or no.
Alternatively, if undesired changes were saved to the startup configuration, it may be necessary to clear all the configurations using the erase startup-config privileged EXEC mode command.
2.2.3.3 – Capture Configuration to a Text File
Configuration files can also be saved and archived to a text document for editing or reuse later. For example, assume a switch has been configured and the running config has been saved.
♦ Connect to the switch using PuTTY or Tera Term.
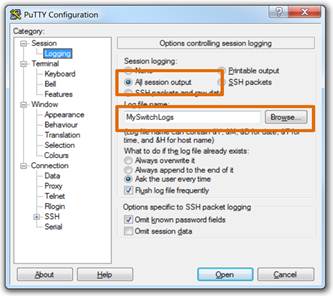
♦ Enable logging and assign a name and file location to save the log file.
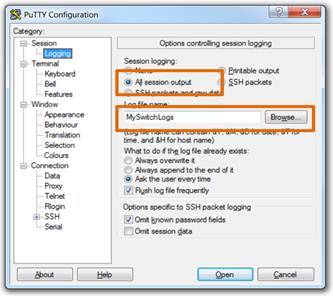
♦ Generate text to be captured as text displayed in the terminal window will also be placed into the chosen file.

♦ Disable logging in the terminal software by choosing None in the Session logging option.
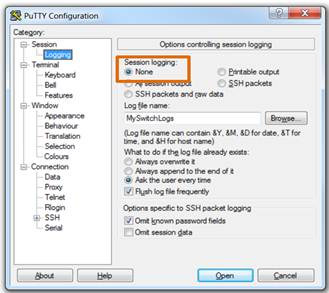
The text file created can be used as a record of how the device is currently implemented and be used to restore a configuration. The file would require editing before being used to restore a saved configuration to a device.
To restore a configuration file to a device:
♦ Enter global configuration mode on the device.
♦ Copy and paste the text file into the terminal window connected to the switch.
The text in the file will be applied as commands in the CLI and become the running configuration on the device.
2.2.3.4 – Packet Tracer – Configuring Initial Switch Settings
2.2.3.4 Packet Tracer – Configuring Initial Switch Settings
2.3 – Address Schemes
2.3.1 – Ports and Addresses
2.3.1.1 – IP Addresses
Each end device on a network (e.g., PCs, laptops, servers, printers, VoIP phones, security cameras, …) require an IP configuration consisting of:
♦ IP address
♦ Subnet mask
♦ Default gateway (optional for some devices)
IPv4 addresses are displayed in dotted decimal format consisting of:
♦ 4 decimal numbers 0 and 255
♦ Separated by decimal points (dots)
♦ E.g., 192.168.1.10, 255.255.255.0, 192.168.1.1
2.3.1.2 – Interfaces and Ports
Cisco IOS Layer 2 switches have physical ports for devices to connect. However, these ports do not support Layer 3 IP addresses.
To remotely connect to and manage a Layer 2 switch, it must be configured with one or more switch virtual interfaces (SVIs).
Each switch has a default VLAN 1 SVI.
Note: A Layer 2 switch does not need an IP address to operate. The SVI IP address is only used to remotely manage a switch.
2.3.2. – Configure IP Addressing
2.3.2.1 – Manual IP Address Configuration for End Devices
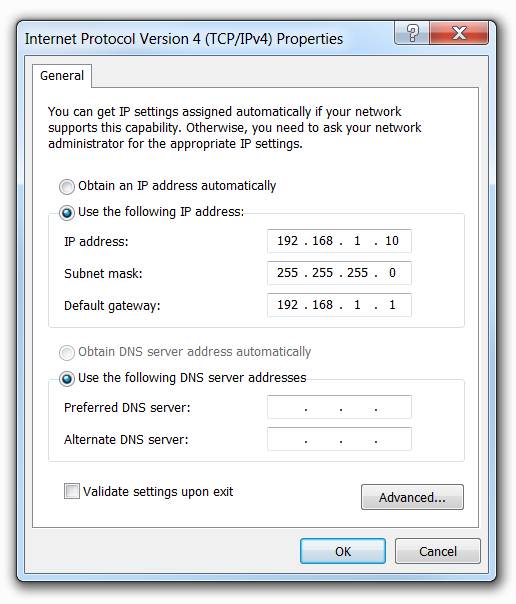
To manually configure an IP address on a Windows host:
Open the Control Panel > Network Sharing Center > Change adapter settings and click on the adapter.
♦ Right-click on the adapter and select Properties to display the Local Area Connection Properties window.
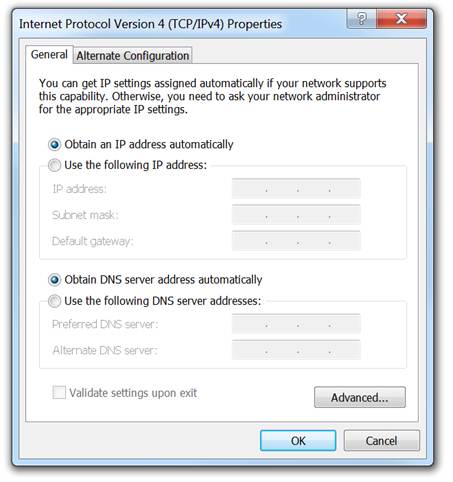
♦ Highlight Internet Protocol Version 4 (TCP/IPv4) and click Properties to open the Internet Protocol Version 4 (TCP/IPv4) Properties window
♦ Click Use the following IP address to manually configure the IPv4 address configuration.
Configure the IPv4 address and subnet mask information, and default gateway and then click OK.
2.3.2.2 – Automatic IP Address Configuration for End Devices
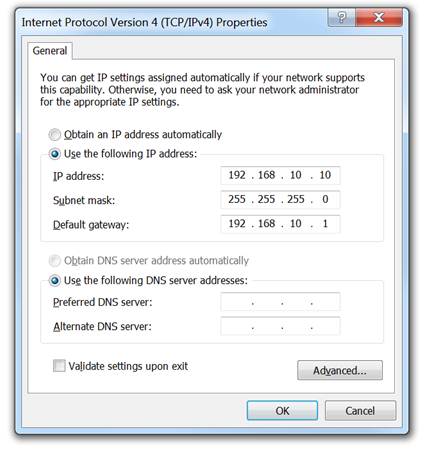
To assign the IP configuration using a Dynamic Host Configuration Protocol (DHCP) server:
Open the Control Panel > Network Sharing Center > Change adapter settings and click on the adapter.
♦ Right-click on the adapter and select Properties to display the Local Area Connection Properties window.
♦ Highlight Internet Protocol Version 4 (TCP/IPv4) and click Properties to open the Internet Protocol Version 4 (TCP/IPv4) Properties window
Click Obtain an IP address automatically and click on OK.
2.3.2.3 – Switch Virtual Interface Configuration (page 2.3.2.4 has no content, only a Syntax Checker)
To remotely manage a switch, it must also be configured with an IP configuration:
♦ However, a switch does not have a physical Ethernet interface that can be configured.
♦ Instead, you must configure the VLAN 1 switch virtual interface (SVI).
The VLAN 1 SVI must be configured with:
♦ IP address – Uniquely identifies the switch on the network
♦ Subnet mask – Identifies the network and host portion in the IP address
♦ Enabled – Using the no shutdown command.

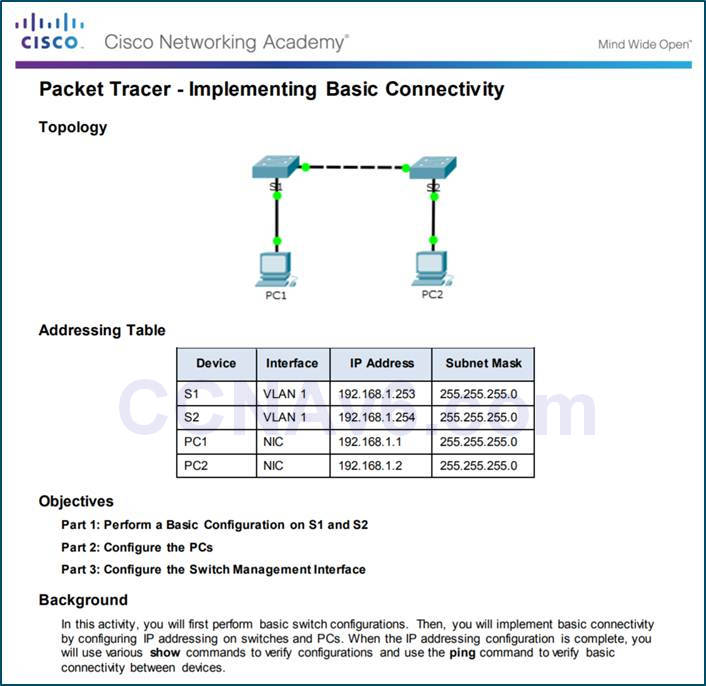
2.3.2.5 – Packet Tracer – Implementing Basic Connectivity
2.3.2.5 Packet Tracer – Implementing Basic Connectivity
2.3.3. – Verifying Connectivity
2.3.3.1 – Interface Addressing Verification
The IP configuration on a Windows host is verified using the ipconfig command.
To verify the interfaces and address settings of intermediary devices like switches and routers, use the show ip interface brief privileged EXEC command.

2.3.3.2 – End-to-End Connectivity Test
The ping command can be used to test connectivity to another device on the network or a website on the Internet.
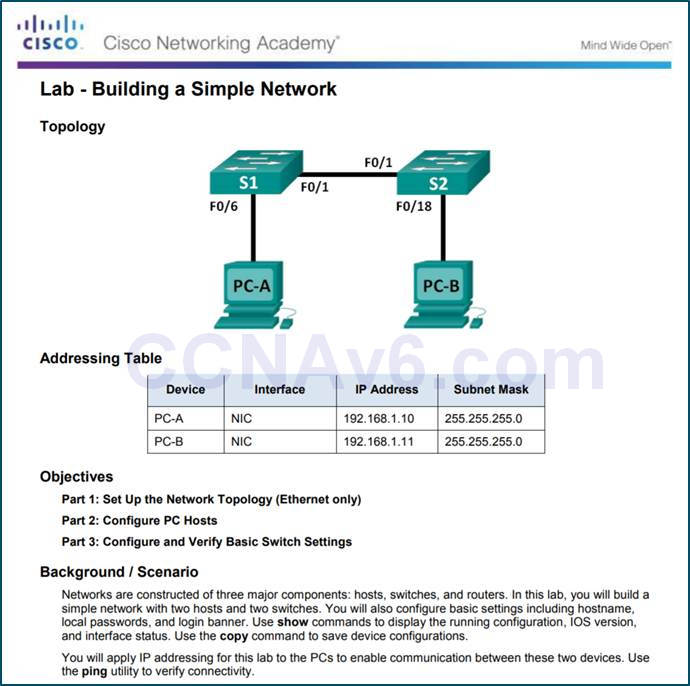
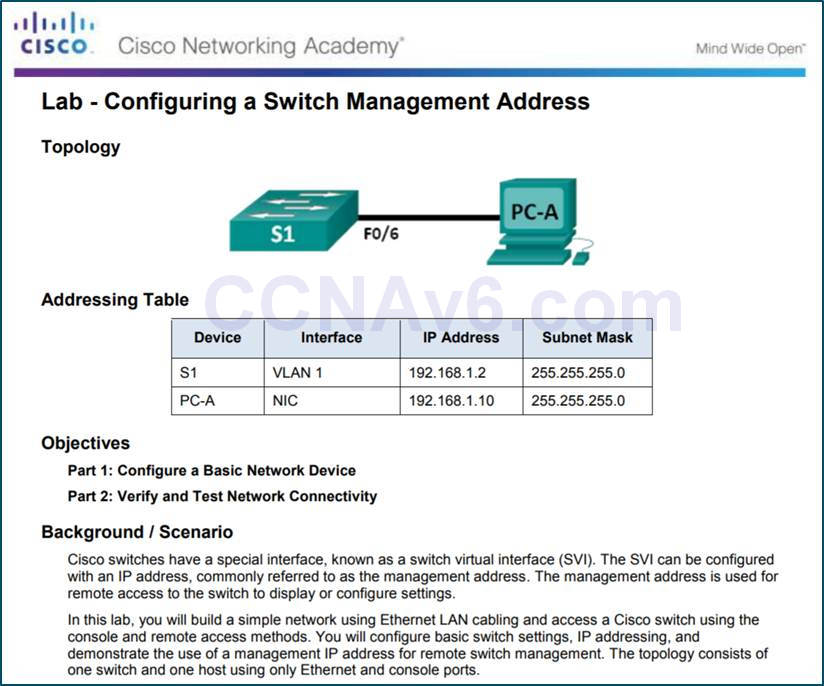
2.3.3.3 – Lab – Build a Simple Network
2.3.3.3 Lab – Building a Simple Network
2.3.3.4 – Lab – Configuring a Switch Management Address
2.3.3.4 Lab – Configuring a Switch Management Address
2.4 – Summary
2.4.1 – Conclusion
2.4.1.1 – Class Activity – Tutor Me
2.4.1.1 Class Activity – Tutor me!

2.4.1.2 – Packet Tracer – Skills Integration Challenge
2.4.1.2 Packet Tracer – Skills Integration Challenge
2.4.1.3 – Chapter 2: Configure a Network Operating System
Explain the features and functions of Cisco IOS Software.
Configure initial settings on a network device using the Cisco IOS software.
Given an IP addressing scheme, configure IP address parameters on end devices to provide end-to-end connectivity in a small to medium-sized business network.
New Terms and Commands
Section 2.1
| kernel
shell Command-line interface (CLI) Graphical user interface (GUI) Cisco IOS Firmware Console Out-of-band SSH Telnet Auxiliary port (AUX) PuTTY Tera Term SecureCRT |
OS X Terminal
Cisco IOS modes User EXEC mode Privileged EXEC mode Global Configuration Mode Line configuration mode Interface configuration mode enable command disable command exit command end command Key combination – Ctrl+Z Context-Sensitive Help Command Syntax Check |
CLI Hot Keys and Shortcuts
Hostnames |
Section 2.2
| hostname name
Strong passwords enable secret class line console 0 password cisco login line vty 0 15 service password-encryption banner motd # the message of the day # Startup configuration Random Access Memory (NVRAM) Running configuration Random Access Memory (RAM) |
show running-config
copy running-config startup-config reload |
Section 2.3
| IPv4 address
Subnet mask Default gateway Physical ports Virtual interface Copper Fiber Optics Wireless Ethernet Local Area Network (LAN) Layer 2 switch Layer 3 addresses Switch virtual interface (SVI) |
Dynamic Host Configuration (DHCP) Domain Name System (DNS) ipconfig command prompt interface vlan 1
|
