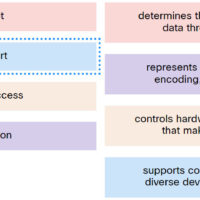
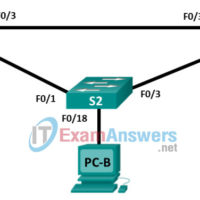
Networking Basics Checkpoint Exam: Network Access Answers 1. Which two OSI model layers have the same functionality as two layers of the TCP/IP model? (Choose two.) transport network data link session physical 2. Which three acronyms/initialisms represent standards organizations? (Choose three.) TCP/IP MAC OSI IANA IETF IEEE 3. …
Networking Basics Checkpoint Exam: Build a Small Network Answers 1. What is the order of bandwidth measurement from smallest to largest? Gbps, Tbps, Mbps, Kbps Tbps, Mbps, Kbps, Gbps Kbps, Mbps, Gbps, Tbps Kbps, Tbps, Mbps, Gbps 2. Which is a characteristic of the Internet? It is not …
3.3.2.3 Lab – Configuring Rapid PVST+, PortFast, and BPDU Guard (Instructor Version) Instructor Note: Red font color or Gray highlights indicate text that appears in the instructor copy only. Topology Addressing Table Device Interface IP Address Subnet Mask S1 VLAN 99 192.168.1.11 255.255.255.0 S2 VLAN 99 192.168.1.12 255.255.255.0 …
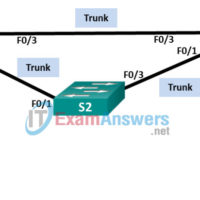
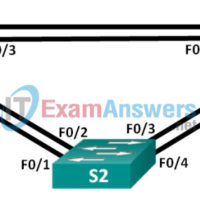
3.1.2.12 Lab – Building a Switched Network with Redundant Links (Instructor Version) Instructor Note: Red font color or Gray highlights indicate text that appears in the instructor copy only. Topology Addressing Table Device Interface IP Address Subnet Mask S1 VLAN 1 192.168.1.1 255.255.255.0 S2 VLAN 1 192.168.1.2 255.255.255.0 …
3.0.1.2 Stormy Traffic (Instructor Version) Instructor Note: Red font color or Gray highlights indicate text that appears in the instructor copy only. Objective Explain the purpose of the Spanning Tree Protocol (STP) in a switched LAN environment with redundant switch links. Instructor Notes: Spanning Tree Protocol (STP) and …
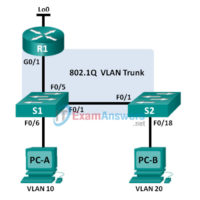
2.2.2.5 Lab – Troubleshooting Inter-VLAN Routing (Instructor Version) Instructor Note: Red font color or Gray highlights indicate text that appears in the instructor copy only. Topology Addressing Table Device Interface IP Address Subnet Mask Default Gateway R1 G0/1.1 192.168.1.1 255.255.255.0 N/A G0/1.10 192.168.10.1 255.255.255.0 N/A G0/1.20 192.168.20.1 255.255.255.0 …
2.1.4.5 Lab – Configure Extended VLANs, VTP, and DTP (Instructor Version) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Topology Addressing Table Table Heading Interface IP Address Subnet Mask S1 VLAN 99 192.168.99.1 255.255.255.0 S2 VLAN 99 192.168.99.2 255.255.255.0 …
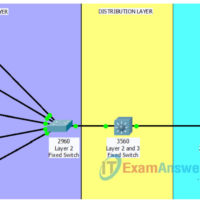
1.3.1.1 Class Activity – Layered Network Design Simulation (Instructor Version) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Objectives Explain the need to design a hierarchical network that is scalable. Instructor Note: This activity can be completed by individual …
Network Defense (NetDef) Course Final Exam Answers Modules 1 – 11 of the Network Defense (NetDef) course Final Answers 1. What is a characteristic of a layered defense-in-depth security approach? When one device fails, another one takes over. One safeguard failure does not affect the effectiveness of other …
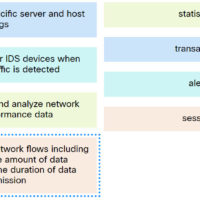
Module Group Exam 3: Network Defense (NetDef) Module 9 – 11 Group Exam – Checkpoint Exam: Evaluating Security Alerts 1. Which two technologies are primarily used on peer-to-peer networks? (Choose two.) Darknet Snort BitTorrent Bitcoin Wireshark 2. Which technique would a threat actor use to disguise traces of …