CCNA Security Chapter 6 Exam Answers (CCNAS v1.2 and v1.1)
1. Which two measures are recommended to mitigate VLAN hopping attacks? (Choose two.)
- Use a dedicated native VLAN for all trunk ports.
- Place all unused ports in a separate guest VLAN.
- Disable trunk negotiation on all ports connecting to workstations.
- Enable DTP on all trunk ports.
- Ensure that the native VLAN is used for management traffic.
2. As a recommended practice for Layer 2 security, how should VLAN 1 be treated?
- All access ports should be assigned to VLAN 1.
- All trunk ports should be assigned to VLAN 1.
- VLAN 1 should be used for management traffic.
- VLAN 1 should not be used.
3. How is a reflector port used in an RSPAN configuration?
- It provides a dedicated connection for the IDS device.
- It allows an RSPAN session to be backward compatible with a SPAN session.
- It acts like a loopback interface in that it reflects the captured traffic to the RSPAN VLAN.
- It allows an IDS device to direct malicious traffic to it, isolating that traffic from other areas of the network.
4. Which attack is mitigated by using port security?
- LAN storm
- VLAN hopping
- STP manipulation
- MAC address table overflow
5. Which technology is used to protect the switched infrastructure from problems caused by receiving BPDUs on ports that should not be receiving them?
- RSPAN
- PortFast
- Root guard
- Loop guard
- BPDU guard
6. Which three switch security commands are required to enable port security on a port so that it will dynamically learn a single MAC address and disable the port if a host with any other MAC address is connected? (Choose three.)
- switchport mode access
- switchport mode trunk
- switchport port-security
- switchport port-security maximum 2
- switchport port-security mac-address sticky
- switchport port-security mac-address mac-address
7. When configuring a switch port for port security, what is the default violation mode?
- protect
- reset
- restrict
- shutdown
8. Which three statements are true regarding SPAN and RSPAN? (Choose three.)
- SPAN can send a copy of traffic to a port on another switch.
- RSPAN is required for syslog and SNMP implementation.
- SPAN can be configured to send a copy of traffic to a destination port on the same switch.
- SPAN can copy traffic on a source port or source VLAN to a destination port on the same switch.
- RSPAN is required to copy traffic on a source VLAN to a destination port on the same switch.
- RSPAN can be used to forward traffic to reach an IDS that is analyzing traffic for malicious behavior.
9. Which Cisco endpoint security product helps maintain network stability by providing posture assessment, quarantining of noncompliant systems, and remediation of noncompliant systems?
- Cisco Access Control Server
- Cisco Security Agent workstation
- Cisco Intrusion Prevention System router
- Cisco Network Admission Control appliance
10. Which attack relies on the default automatic trunking configuration on most Cisco switches?
- LAN storm attack
- VLAN hopping attack
- STP manipulation attack
- MAC address spoofing attack
11. With IP voice systems on data networks, which two types of attacks target VoIP specifically? (Choose two.)
- CoWPAtty
- Kismet
- SPIT
- virus
- vishing
12. Which two elements are part of the Cisco strategy for addressing endpoint security? (Choose two.)
- policy compliance using products such as Cisco NAC
- network infection monitoring using products such as Cisco Secure ACS
- threat protection using products such as Cisco Security Agent
- attack detection using products such as Cisco NAC
- risk assessment compliance using products such as Cisco Security Agent
13. Which frames are spoofed in STP manipulation attacks?
- BPDU
- DTP
- ISL
- 802.1q
14. Which option best describes a MAC address spoofing attack?
- An attacker gains access to another host and masquerades as the rightful user of that device.
- An attacker alters the MAC address of his host to match another known MAC address of a target host.
- An attacker alters the MAC address of the switch to gain access to the network device from a rogue host device.
- An attacker floods the MAC address table of a switch so that the switch can no longer filter network access based on MAC addresses.
15. What happens when the MAC address notification feature is enabled on a switch?
- An SDEE alert is generated, and the switch resets the interface when an invalid MAC address is detected.
- An STP multicast notification packet is forwarded to all switches any time a change in the network topology is detected.
- A port violation occurs when a MAC address outside of the range of allowed addresses transmits traffic over a secure port.
- An SNMP trap is sent to the network management system whenever a new MAC address is added to or an old address is deleted from the forwarding tables.
16. Which device supports the use of SPAN to enable monitoring of malicious activity?
- Cisco NAC
- Cisco IronPort
- Cisco Security Agent
- Cisco Catalyst switch
17. An administrator wants to prevent a rogue Layer 2 device from intercepting traffic from multiple VLANs on a network. Which two actions help mitigate this type of activity? (Choose two.)
- Disable DTP on ports that require trunking.
- Place unused active ports in an unused VLAN.
- Secure the native VLAN, VLAN 1, with encryption.
- Set the native VLAN on the trunk ports to an unused VLAN.
- Turn off trunking on all trunk ports and manually configure each VLAN as required on each port.
18. Refer to the exhibit. Based on the output generated by the show monitor session 1 command, how will SPAN operate on the switch?
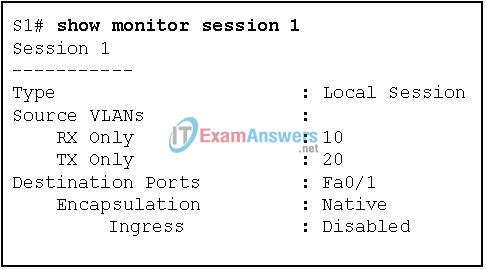
- All traffic transmitted from VLAN 10 or received on VLAN 20 is forwarded to FastEthernet 0/1.
- All traffic received on VLAN 10 or transmitted from VLAN 20 is forwarded to FastEthernet 0/1.
- Native VLAN traffic received on VLAN 10 or transmitted from VLAN 20 is forwarded to FastEthernet 0/1.
- Native VLAN traffic transmitted from VLAN 10 or received on VLAN 20 is forwarded to FastEthernet 0/1.
19. How many Cisco Security Agent clients can one Management Center for CSA console support?
- 1,000
- 10,000
- 100,000
- 1,000,000
20. Which three are SAN transport technologies? (Choose three.)
- Fibre Channel
- SATA
- iSCSI
- IP PBX
- FCIP
- IDE
21. If a switch is configured with the storm-control command and the action shutdown and action trap parameters, which two actions does the switch take when a storm occurs on a port? (Choose two.)
- The port is disabled.
- The switch is rebooted.
- An SNMP log message is sent.
- The port is placed in a blocking state.
- The switch forwards control traffic only.
22. Refer to the exhibit. What action will the switch take when the maximum number of secure MAC addresses has reached the allowed limit on the Fa0/2 port?
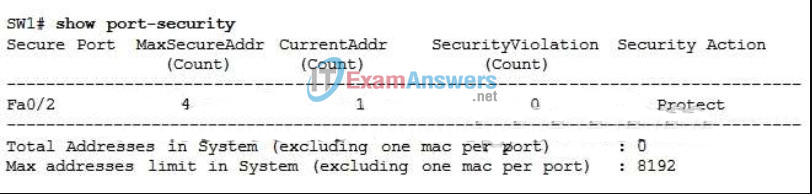
- Packets with unknown source addresses are dropped, but notification of the dropped packets is sent.
- The VLAN that Fa0/2 is on is set to error-disabled and all traffic on the VLAN is stopped.
- The interface immediately becomes error-disabled and the port LED is turned off.
- Packets with unknown source addresses are dropped without notification.
23. Which software tool can a hacker use to flood the MAC address table of a switch?
- macof
- Cisco CCP
- kiwi syslog server
- protocol analyzer
24. Which two methods are used to mitigate VLAN attacks? (Choose two.)
- enabling port security on all trunk ports
- using a dummy VLAN for the native VLAN
- implementing BPDU guard on all access ports
- disabling DTP autonegotiation on all trunk ports
- using ISL instead of 802.1q encapsulation on all trunk interfaces
25. What is an example of a trusted path in an operating system?
- digital certificate
- digital signature
- hash message authentication
- Ctrl-Alt-Delete key sequence
26. Why are traditional network security perimeters not suitable for the latest consumer-based network endpoint devices?
- These devices are not managed by the corporate IT department.
- These devices are more varied in type and are portable.
- These devices connect to the corporate network through public wireless networks.
- These devices pose no risk to security as they are not directly connected to the corporate network.
27. Which Cisco IronPort appliance would an organization install to manage and monitor security policy settings and audit information?
- C-Series
- M-Series
- S-Series
- SenderBase-Series
28. Which Cisco IronPort appliance would an organization install to protect against malware?
- C-Series
- M-Series
- S-Series
- SenderBase-Series
29. What is the goal of the Cisco NAC framework and the Cisco NAC appliance?
- to ensure that only hosts that are authenticated and have had their security posture examined and approved are permitted onto the network
- to monitor data from the company to the ISP in order to build a real-time database of current spam threats from both internal and external sources
- to provide anti-malware scanning at the network perimeter for both authenticated and non-authenticated devices
- to provide protection against a wide variety of web-based threats, including adware, phishing attacks, Trojan horses, and worms
30. When the Cisco NAC appliance evaluates an incoming connection from a remote device against the defined network policies, what feature is being used?
- authentication and authorization
- posture assessment
- quarantining of noncompliant systems
- remediation of noncompliant systems
31. Which command is used to configure the PVLAN Edge feature?
- switchport block
- switchport nonnegotiate
- switchport protected
- switchport port-security violation protect
32. Which statement is true about a characteristic of the PVLAN Edge feature on a Cisco switch?
- All data traffic that passes between protected ports must be forwarded through a Layer 2 device.
- All data traffic that passes between protected ports must be forwarded through a Layer 3 device.
- Only broadcast traffic is forwarded between protected ports.
- Only unicast traffic is forwarded between protected ports.
33. What is the default configuration of the PVLAN Edge feature on a Cisco switch?
- All active ports are defined as protected.
- All ports are defined as protected.
- No ports are defined as protected.
- EtherChannel groups are defined as protected ports.
34. Under which circumstance is it safe to connect to an open wireless network?
- The connection utilizes the 802.11n standard.
- The device has been updated with the latest virus protection software.
- The connection is followed by a VPN connection to a trusted network.
- The user does not plan on accessing the corporate network when attached to the open wireless network.
35. How does a switch interface that uses sticky port security handle MAC addresses?
- They are configured dynamically and are saved in the running configuration.
- They are configured dynamically and are not saved in the running configuration.
- They are configured manually and are not saved in the running configuration.
- The addresses are configured manually and are saved in the running configuration.
36. Refer to the exhibit. The Fa0/2 interface on switch S1 has been configured with the switchport port-security mac-address 0023.189d.6456 command and a workstation has been connected. What could be the reason that the Fa0/2 interface is shutdown?
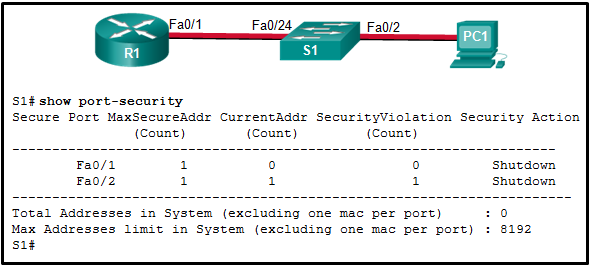
- The connection between S1 and PC1 is via a crossover cable.
- The Fa0/24 interface of S1 is configured with the same MAC address as the Fa0/2 interface.
- S1 has been configured with a switchport port-security aging command.
- The MAC address of PC1 that connects to the Fa0/2 interface is not the configured MAC address.
37. Which mitigation technique can help prevent MAC table overflow attacks?
- storm control
- switchport security
- BPDU guard
- root guard
38. Which attack allows the attacker to see all frames on a broadcast network by causing a switch to flood all incoming traffic?
- MAC table overflow
- VLAN hopping
- 802.1q double tagging
- LAN storm
- STP manipulation
39. Where is the port security configuration most effective in a multi-layer switched network environment?
- on core layer switches
- on perimeter layer switches
- on access layer switches
- on distribution layer switches
40. Which statement describes a MAC address table overflow attack?
- Frames flood the LAN, creating excessive traffic and degrading network performance.
- A software tool floods a switch with frames containing randomly generated source and destination MAC and IP addresses
- An attacker alters the MAC address in a frame to match the address of a target host.
- The attacking host broadcasts STP configuration and topology change BPDUs to force spanning-tree recalculations.
41. Refer to the exhibit. Which two statements are correct regarding the configuration on switch S1? (Choose two.)
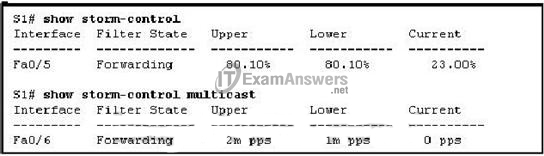
- Port Fa0/5 storm control for multicasts will be activated if traffic exceeds 80.1 percent of the total bandwidth.
- Port Fa0/6 storm control for multicasts and broadcasts will be activated if traffic exceeds 2,000,000 packets per second.
- Port Fa0/6 storm control for multicasts will be activated if traffic exceeds 2,000,000 packets per second.
- Port Fa0/5 storm control for broadcasts and multicasts will be activated if traffic exceeds 80.1 percent of 2,000,000 packets per second.
- Port Fa0/5 storm control for broadcasts will be activated if traffic exceeds 80.1 percent of the total bandwidth.
42. What functionality is provided by Cisco SPAN in a switched network?
- It protects the switched network from receiving BPDUs on ports that should not be receiving them.
- It copies traffic that passes through a switch interface and sends the data directly to a syslog or SNMP server for analysis.
- It mitigates MAC address overflow attacks.
- It prevents traffic on a LAN from being disrupted by a broadcast storm.
- It inspects voice protocols to ensure that SIP, SCCP, H.323, and MGCP requests conform to voice standards.
- It mirrors traffic that passes through a switch port or VLAN to another port for traffic analysis
