CCNA Security Chapter 8 Exam Answers (CCNAS v1.2 and v1.1)
1. What are two benefits of an SSL VPN? (Choose two.)
- It supports all client/server applications.
- It supports the same level of cryptographic security as an IPsec VPN.
- It has the option of only requiring an SSL-enabled web browser.
- The thin client mode functions without requiring any downloads or software.
- It is compatible with DMVPNs, Cisco IOS Firewall, IPsec, IPS, Cisco Easy VPN, and NAT.
2. When verifying IPsec configurations, which show command displays the encryption algorithm, hash algorithm, authentication method, and Diffie-Hellman group configured, as well as default settings?
- show crypto map
- show crypto ipsec sa
- show crypto isakmp policy
- show crypto ipsec transform-set
3. When configuring a site-to-site IPsec VPN using the CLI, the authentication pre-share command is configured in the ISAKMP policy. Which additional peer authentication configuration is required?
- Configure the message encryption algorithm with the encryptiontype ISAKMP policy configuration command.
- Configure the DH group identifier with the groupnumber ISAKMP policy configuration command.
- Configure a hostname with the crypto isakmp identity hostname global configuration command.
- Configure a PSK with the crypto isakmp key global configuration command.
4. Which action do IPsec peers take during the IKE Phase 2 exchange?
- exchange of DH keys
- negotiation of IPsec policy
- verification of peer identity
- negotiation of IKE policy sets
5. A network administrator is planning to implement centralized management of Cisco VPN devices to simplify VPN deployment for remote offices and teleworkers. Which Cisco IOS feature would provide this solution?
- Cisco Easy VPN
- Cisco VPN Client
- Cisco IOS SSL VPN
- Dynamic Multipoint VPN
6. Which two statements accurately describe characteristics of IPsec? (Choose two.)
- IPsec works at the application layer and protects all application data.
- IPsec works at the transport layer and protects data at the network layer.
- IPsec works at the network layer and operates over all Layer 2 protocols.
- IPsec is a framework of proprietary standards that depend on Cisco specific algorithms.
- IPsec is a framework of standards developed by Cisco that relies on OSI algorithms.
- IPsec is a framework of open standards that relies on existing algorithms.
7. Refer to the exhibit. Which two IPsec framework components are valid options when configuring an IPsec VPN on a Cisco ISR router? (Choose two.)
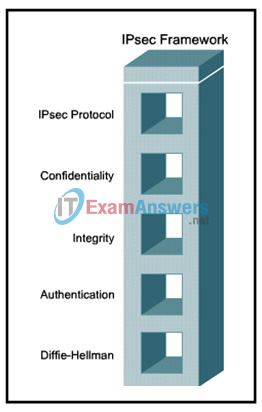
- Integrity options include MD5 and RSA.
- IPsec protocol options include GRE and AH.
- Confidentiality options include DES, 3DES, and AES.
- Authentication options include pre-shared key and SHA.
- Diffie-Hellman options include DH1, DH2, and DH5.
8. With the Cisco Easy VPN feature, which process ensures that a static route is created on the Cisco Easy VPN Server for the internal IP address of each VPN client?
- Cisco Express Forwarding
- Network Access Control
- On-Demand Routing
- Reverse Path Forwarding
- Reverse Route Injection
9. Refer to the exhibit. A site-to-site VPN is required from R1 to R3. The administrator is using the SDM Site-to-Site VPN Wizard on R1. Which IP address should the administrator enter in the highlighted field?
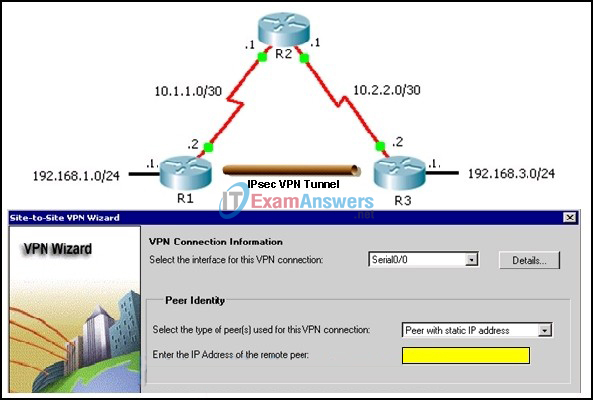
- 10.1.1.1
- 10.1.1.2
- 10.2.2.1
- 10.2.2.2
- 192.168.1.1
- 192.168.3.1
10. What is required for a host to use an SSL VPN?
- VPN client software must be installed.
- A site-to-site VPN must be preconfigured.
- The host must be in a stationary location.
- A web browser must be installed on the host.
11. What are two authentication methods that can be configured using the SDM Site-to-Site VPN Wizard? (Choose two.)
- MD5
- SHA
- pre-shared keys
- encrypted nonces
- digital certificates
12. Which UDP port must be permitted on any IP interface used to exchange IKE information between security gateways?
- 400
- 500
- 600
- 700
13. Which requirement necessitates using the Step-by-Step option of the SDM Site-to-Site VPN wizard instead of the Quick Setup option?
- AES encryption is required.
- 3DES encryption is required.
- Pre-shared keys are to be used.
- The remote peer is a Cisco router.
- The remote peer IP address is unknown.
14. Which IPsec protocol should be selected when confidentiality is required?
- tunnel mode
- transport mode
- authentication header
- encapsulating security payload
- generic routing encapsulation
15. Which statement describes an important characteristic of a site-to-site VPN?
- It must be statically set up.
- It is ideally suited for use by mobile workers.
- It requires using a VPN client on the host PC.
- It is commonly implemented over dialup and cable modem networks.
- After the initial connection is established, it can dynamically change connection information.
16. Refer to the exhibit. Based on the SDM screen, which Easy VPN Server component is being configured?
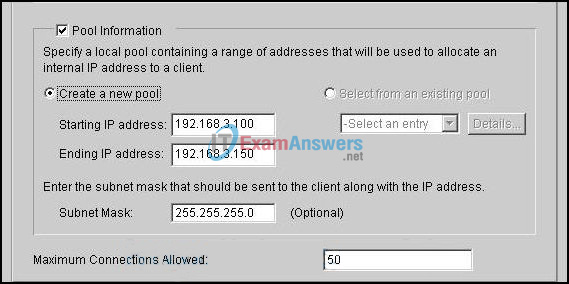
- group policy
- transform set
- IKE proposal
- user authentication
17. A user launches Cisco VPN Client software to connect remotely to a VPN service. What does the user select before entering the username and password?
- the SSL connection type
- the IKE negotiation process
- the desired preconfigured VPN server site
- the Cisco Encryption Technology to be applied
18. What is the default IKE policy value for authentication?
- MD5
- SHA
- RSA signatures
- pre-shared keys
- RSA encrypted sconces
19. When using ESP tunnel mode, which portion of the packet is not authenticated?
- ESP header
- ESP trailer
- new IP header
- original IP header
20. Refer to the exhibit. Under the ACL Editor, which option is used to specify the traffic to be encrypted on a secure connection?
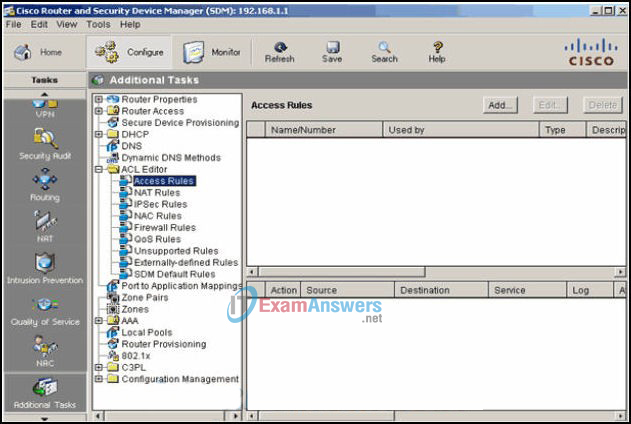
- Access Rules
- IPsec Rules
- Firewall Rules
- SDM Default Rules
21. Refer to the exhibit. A network administrator is troubleshooting a GRE VPN tunnel between R1 and R2. Assuming the R2 GRE configuration is correct and based on the running configuration of R1, what must the administrator do to fix the problem?
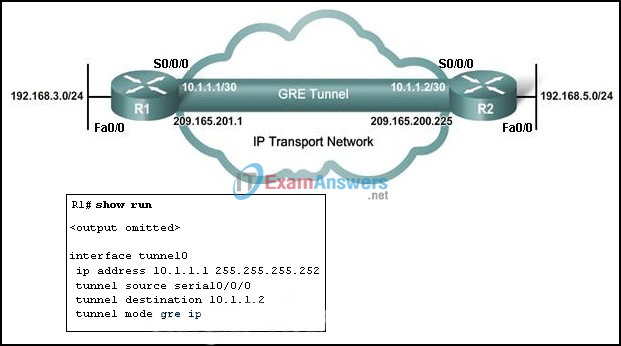
- change the tunnel source interface to Fa0/0
- change the tunnel destination to 192.168.5.1
- change the tunnel IP address to 192.168.3.1
- change the tunnel destination to 209.165.200.225
- change the tunnel IP address to 209.165.201.1
22. How many bytes of overhead are added to each IP packet while it is transported through a GRE tunnel?
- 8
- 16
- 24
- 32
23. Refer to the exhibit. Based on the CCP screen that is shown, which two conclusions can be drawn about the IKE policy that is being configured? (Choose two.)
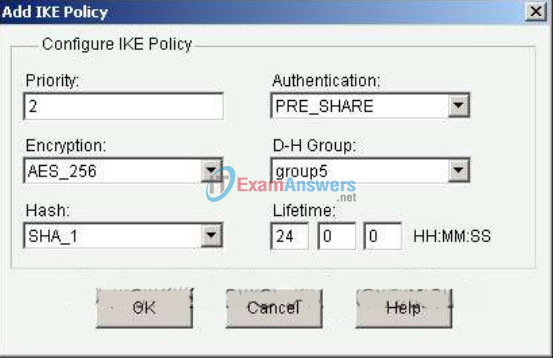
- It will use digital certificates for authentication.
- It will use a predefined key for authentication.
- It will use a very strong encryption algorithm.
- It will be the default policy with the highest priority.
- It is being created using the CCP VPN Quick Setup Wizard.
24. What is the default IKE policy value for encryption?
- 128-bit AES
- 192-bit AES
- 256-bit AES
- 3DES
- DES
25. When configuring an IPsec VPN, what is used to define the traffic that is sent through the IPsec tunnel and protected by the IPsec process?
- crypto map
- crypto ACL
- ISAKMP policy
- IPsec transform set
26. What can be used as a VPN gateway when setting up a site-to-site VPN?
- Cisco Catalyst switch
- Cisco router
- Cisco Unified Communications Manager
- Cisco AnyConnect
27. Which three statements describe the IPsec protocol framework? (Choose three.)
- AH uses IP protocol 51.
- AH provides encryption and integrity.
- AH provides integrity and authentication.
- ESP uses UDP protocol 50.
- ESP requires both authentication and encryption.
- ESP provides encryption, authentication, and integrity.
28. Which statement describes the operation of the IKE protocol?
- It uses IPsec to establish the key exchange process.
- It uses sophisticated hashing algorithms to transmit keys directly across a network.
- It calculates shared keys based on the exchange of a series of data packets.
- It uses TCP port 50 to exchange IKE information between the security gateways.
29. What is the purpose of the “Generate Mirror…” button in site-to-site VPN wizard of CCP?
- to automatically configure the router on the other side of the tunnel
- to test the VPN configuration and to verify operation
- to produce the required CLI commands to configure the router on the other side of the tunnel
- to provide the VPN wizard setting required on the router on the other side of the tunnel
30. Refer to the exhibit. Which pair of crypto isakmp key commands would correctly configure PSK on the two routers?

- R1# crypto isakmp key cisco123 hostname R1
R2# crypto isakmp key cisco123 hostname R2 - R1# crypto isakmp key cisco123 address 209.165.200.227
R2# crypto isakmp key cisco123 address 209.165.200.226 - R1# crypto isakmp key cisco123 address 209.165.200.226
R2# crypto isakmp key cisco123 address 209.165.200.227 - R1# crypto isakmp key cisco123 address 209.165.200.226
R2# crypto isakmp key secure address 209.165.200.227
31. Refer to the exhibit. How will traffic that does not match that defined by access list 101 be treated by the router?
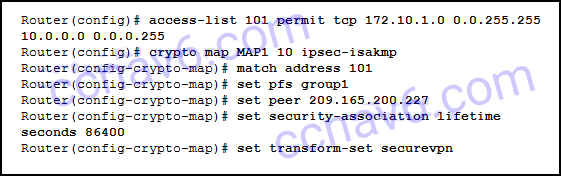
- It will be sent encrypted.
- It will be discarded.
- It will be sent unencrypted.
- It will be blocked.
32. Which factor is a drawback of providing remote connectivity and work solutions to employees?
- system security being maintained employees themselves.
- job-related stresses
- transportation-related pollution
- 24/7 time zone business availability
- Employee telecommuting provides benefits through decreasing job-related stress and pollution.
33. What are two characteristics of SSL VPNs? (Choose two.)
- They protect all IP-based applications.
- They require only a web browser on the client computer.
- They require specific client software installed on the client device.
- They can use noncompany-managed devices.
- They can use strong two-way authentication via shared secrets or digital certificates.
34. What VPN solution uses a server to push IPsec policies to mobile clients so that they can access company resources over a secure IPsec tunnel?
- Cisco VPN Wizard
- Cisco SSL VPN
- Cisco Easy VPN
- Step by Step Wizard
35. Which authentication method is available when specifying a method list for group policy lookup using the CCP Easy VPN Server wizard?
- Active Directory
- Kerberos
- Certificate Authority
- RADIUS
- TACACS+
36. A network administrator has acquired two different VPN-capable routers that will be installed in a network. Which factor must be verified between two routers prior to configuring a VPN tunnel?
- device interoperability
- firewall configuration
- intrusion prevention
- quality of service
37. The use of 3DES within the IPsec framework is an example of which of the five IPsec building blocks?
- confidentiality
- nonrepudiation
- authentication
- Diffie-Hellman
- integrity
38. What protocol is used by IPsec to calculate shared keys and to negotiate the parameters to be used by IPsec SAs?
- NTP
- IKE
- ESP
- AH
39. What is the purpose of configuring multiple crypto ACLs when building a VPN connection between remote sites?
- When multiple combinations of IPsec protection are being chosen, multiple crypto ACLs can define different traffic types.
- Multiple crypto ACLs can be configured to deny specific network traffic from crossing a VPN.
- Multiple crypto ACLs can define multiple remote peers for connecting with a VPN-enabled router across the Internet or network.
- By applying the ACL on a public interface, multiple crypto ACLs can be built to prevent public users from connecting to the VPN-enabled router.
40. When CCP Quick Setup is used to configure a VPN-capable router, what is the strongest level of encryption allowed?
- SEAL
- AES
- 3DES
- DES
41. A network administrator plans to deploy an SSL VPN on a Cisco IOS router. Which SSL VPN mode would require the user to download a Java applet to connect to POP3, SMTP, and SSH services?
- clientless access mode
- full client access mode
- thin client mode
- Easy VPN Remote
