CCNA Security Chapter 9 Exam Answers (CCNAS v1.2 and v1.1)
1. Which three statements describe ethics in network security? (Choose three.)
- principles put into action in place of laws
- foundations for current laws
- set of moral principles that govern civil behavior
- standard that is higher than the law
- set of regulations established by the judiciary system
- set of legal standards that specify enforceable actions when the law is broken
2. Which component of the security policy lists specific websites, newsgroups, or bandwidth-intensive applications that are not allowed on the company network?
- remote access policies
- acceptable use policies
- incident handling procedures
- identification and authentication policies
3. What are the two components in the Cisco Security Management Suite? (Choose two.)
- Cisco Intrusion Prevention
- Cisco Network Admission Control
- Cisco Security Agent
- Cisco Security Manager
- Cisco Security MARS
4. Which statement could be expected to be included in a Code of Ethics that is related to IT and network security?
- Employees breaching the Code of Ethics will be prosecuted to the full extent of the law.
- Application of the Code of Ethics to use of the network is at the discretion of the employee.
- Employees with greater than 5 years of service can claim exemption from provisions of the Code of Ethics.
- The network is to be used by employees to provide diligent and competent services to the organization.
5. Which two Cisco Threat Control and Containment technologies address endpoint security? (Choose two.)
- Cisco Application Control Engine
- Cisco Network Admission Control
- Cisco Security Agent
- Cisco Security Monitoring, Analysis, and Response System
- virtual private network
6. What are three key principles of a Cisco Self-Defending Network? (Choose three.)
- adaptability
- authentication
- collaboration
- confidentiality
- integration
- integrity
7. Which security services, available through the Cisco Self-Defending Network, include VPN access?
- secure communications
- threat control and containment
- operational control and policy management
- application control for infrastructure
8. What three areas should be considered when designing a network security policy? (Choose three.)
- remote access
- network maintenance
- service level agreement
- network quality of service
- network equipment provider
- identification and authentication
9. What are the two major elements of the Cisco Secure Communications solution? (Choose two.)
- secure communications for extranets
- secure communications for intranets
- secure communications for management
- secure communications for remote access
- secure communications for site-to-site connections
10. Which term describes a completely redundant backup facility, with almost identical equipment to the operational facility, that is maintained in the event of a disaster?
- backup site
- cold site
- hot site
- reserve site
11. Which three detailed documents are used by security staff for an organization to implement the security policies? (Choose three.)
- asset inventory
- best practices
- guidelines
- procedures
- risk assessment
- standards
12. What is a feature of an effective network security training program?
- Participation in the network security training is voluntary.
- Employee groups are identified and the training is customized to their needs.
- All employees become trained in the design and implementation of secure networks.
- Training for all employees covers the full scope of security issues related to the organization.
13. What is a design feature of a secure network life cycle management process?
- Security is considered once the network is fully operational.
- Security is purposefully included in every phase of the system development life cycle.
- Security requirements are assessed and fully implemented in the initiation phase of the system development life cycle.
- Security cost and reporting considerations are determined in the operations and maintenance phase of the system development life cycle.
14. What are the two major components of a security awareness program? (Choose two.)
- awareness campaign
- security policy development
- security solution development
- self-defending network implementation
- training and education
15. Which three documents comprise the hierarchical structure of a comprehensive security policy for an organization? (Choose three.)
- backup policy
- backup policy
- server policy
- incident policy
- governing policy
- end-user policy
- technical policy
16. When an organization implements the two-person control principle, how are tasks handled?
- A task requires two individuals who review and approve the work of each other.
- A task is broken down into two parts, and each part is assigned to a different individual.
- A task must be completed twice by two operators who must achieve the same results.
- A task is rotated among individuals within a team, each completing the entire task for a specific amount of time.
17. Which network security test requires a network administrator to launch an attack within the network?
- network scan
- password crack
- penetration test
- vulnerability scan
18. Which principle of the Cisco Self-Defending Network emphasizes that security should be built in?
- adapt
- collaborate
- integrate
- simplify
19. Refer to the exhibit. When implementing the Cisco Self-Defending Network, which two technologies ensure confidentiality when referring to secure communications? (Choose two.)
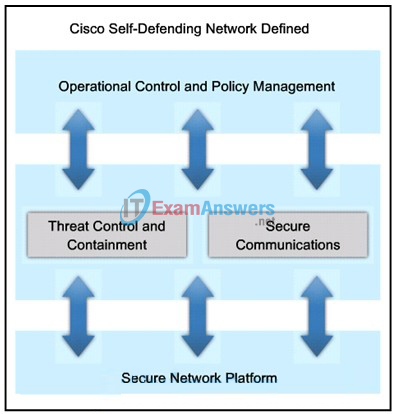
- Cisco NAC appliances and Cisco Security Agent
- Cisco Security Manager
- Cisco Security Monitoring, Analysis, and Response System
- Intrusion Prevention System
- IPsec VPN
- SSL VPN
20. Which security document includes implementation details, usually with step-by-step instructions and graphics?
- guideline document
- standard document
- procedure document
- overview document
21. What is the primary focus of network operations security?
- to design and develop secure application code
- to support deployment and periodic maintenance of secure systems
- to conduct regular employee background checks
- to reprimand personnel who do not adhere to security policies
22. Which type of analysis uses a mathematical model that assigns a monetary figure to the value of assets, the cost of threats being realized, and the cost of security implementations?
- Qualitative Risk Analysis
- Quantitative Risk Analysis
- Qualitative Asset Analysis
- Quantitative Continuity Analysis
23. In which phase of the system development life cycle should security requirements be addressed?
- Add security requirements during the initiation phase.
- Include a minimum set of security requirements at each phase.
- Apply critical security requirements during the implementation phase.
- Implement the majority of the security requirements at the acquisition phase.
24. Which option describes ethics?
- Ethics is a standard that is higher than the law.
- Ethics involves government agencies enforcing regulations.
- Ethics compliance is the basis for setting security policies.
- Ethics deals with criminal law and monetary compensation.
25. In the Cisco SecureX architecture, which component is considered the workhorse of policy enforcement?
- next-generation endpoint
- policy management console
- scanning engine
- Security Intelligence Operations
26. Which development has contributed most to the growing demand for a borderless network?
- consumer endpoints
- DMZ services
- corporate managed laptops
- personal firewall software
27. Which aspect of a scanning element is able to determine a security policy to apply based on information such as the person using the device, the location of the device, and the application being used?
- context awareness
- perimeter awareness
- centralized enforcement
- perimeter deployment
28. A company is considering implementing the Cisco SecureX security architecture. What is the purpose of Cisco TrustSec?
- It is a technology that implements packet tagging to allow security elements to share information from scanning elements.
- It is a large cloud-based security ecosystem with global correlation.
- It is a stand-alone appliance managed from a central policy console.
- It is a perimeter-based, stand-alone network scanning device.
29. Which statement about network security within the SecureX architecture is true?
- It is located closer to the end user.
- It is implemented in the network core.
- It is enforced in a highly centralized structure.
- It is managed by a single policy.
30. Which Cisco SecureX product family would be primarily responsible for detecting and blocking attacks and exploits, while preventing intruder access?
- secure e-mail and web
- secure access
- secure mobility
- secure data center
- secure network
31. Which SecureX product family would include Cisco AnyConnect?
- secure network
- secure e-mail and web
- secure access
- secure mobility
- secure data center
32. If a web browser is to be used, and not a hardware or software-based client, which Cisco solution is best for establishing a secure VPN connection?
- VPN Services for Cisco ASA Series
- Cisco Adaptive Wireless IPS Software
- Cisco AnyConnect Secure Mobility Solutions
- Cisco Virtual Security Gateway
33. Which Cisco secure access solution can be used to determine if hosts are compliant with security policies?
- Network Admission Control Appliance
- Cisco Secure Access Control System
- Cisco AnyConnect Secure Mobility Solutions
- Cisco Adaptive Wireless IPS Software
34. What protocol is used by SCP for secure transport?
- IPSec
- HTTPS
- SSH
- Telnet
- TFTP
35. A network engineer is using a Cisco ASA as a proxy device to provide remote secure access to a company web server. What technology is being used?
- Cisco AnyConnect Secure Mobility Client with SSL
- Cisco Secure Mobility Clientless SSL VPN
- Cisco VPN Client
- generic routing encapsulation tunnel using Ipsec
36. What is a characteristic of ASA security levels?
- The lower the security level on an interface, the more trusted the interface.
- An ACL needs to be configured to explicitly permit traffic from an interface with a lower security level to an interface with a higher security level.
- Each operational interface must have a name and be assigned a security level from 0 to 200.
- Inbound traffic is identified as the traffic moving from an interface with a higher security level to an interface with a lower security level.
37. Refer to the exhibit. Two types of VLAN interfaces were configured on an ASA 5505 with a Base license. The administrator wants to configure a third VLAN interface with limited functionality. Which action should be taken by the administrator to configure the third interface?
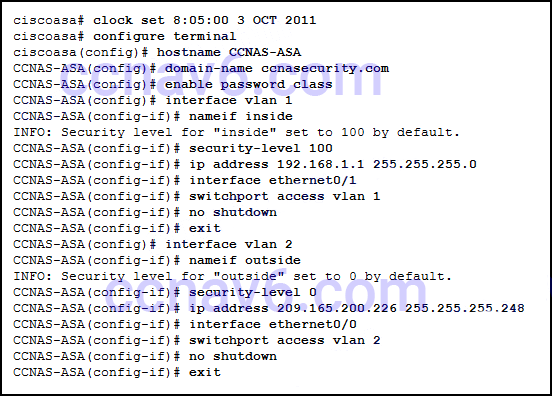
- The administrator needs to acquire the Security Plus license, because the Base license does not support the proposed action.
- The administrator configures the third VLAN interface the same way the other two were configured, because the Base license supports the proposed action.
- The administrator must enter the no forward interface vlan command before the nameif command on the third interface.
- Because the ASA 5505 does not support the configuration of a third interface, the administrator cannot configure the third VLAN.
38. What command defines a DHCP pool that uses the maximum number of DHCP client addresses available on an ASA 5505 that is using the Base license?
- CCNAS-ASA(config)# dhcpd address 192.168.1.10-192.168.1.100 inside
- CCNAS-ASA(config)# dhcpd address 192.168.1.25-192.168.1.56 inside
- CCNAS-ASA(config)# dhcpd address 192.168.1.20-192.168.1.50 inside
- CCNAS-ASA(config)# dhcpd address 192.168.1.30-192.168.1.79 inside
39. Which statement describes the function provided to a network administrator who uses the Cisco Adaptive Security Device Manager (ASDM) GUI that runs as a Java Web Start application?
- The administrator can connect to and manage multiple ASA devices, Cisco routers, and Cisco switches.
- The administrator can connect to and manage multiple ASA devices.
- The administrator can connect to and manage multiple ASA devices and Cisco routers.
- The administrator can connect to and manage a single ASA.
40. Which two statements are true about ASA standard ACLs? (Choose two.)
- They identify only the destination IP address.
- They are the most common type of ACL.
- They are typically only used for OSPF routes.
- They are applied to interfaces to control traffic.
- They specify both the source and destination MAC address.
41. What is the purpose of the webtype ACLs in an ASA?
- to inspect outbound traffic headed towards certain web sites
- to restrict traffic that is destined to an ASDM
- to filter traffic for clientless SSL VPN users
- to monitor return traffic that is in response to web server requests that are initiated from the inside interface
42. Refer to the exhibit. A network administrator is configuring PAT on an ASA device to enable internal workstations to access the Internet. Which configuration command should be used next?
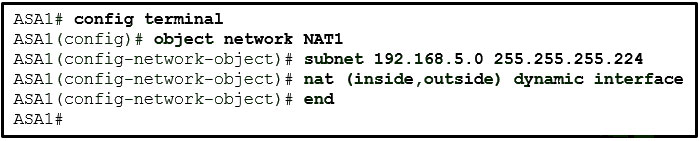
- nat (inside,outside) dynamic NET1
- nat (outside,inside) dynamic interface
- nat (inside,outside) dynamic interface
- nat (outside,inside) dynamic NET1
43. Which Cisco VPN solution provides limited access to internal network resources by utilizing a Cisco ASA and provides browser-based access only?
- SSL
- clientless SSL VPN
- IPsec
- client-based SSL VPN
44. Refer to the exhibit. A network administrator is configuring an object group on an ASA device. Which configuration keyword should be used after the object group name SERVICE1?

- ip
- tcp
- udp
- icmp
45. Refer to the exhibit. A network administrator has configured NAT on an ASA device. What type of NAT is used?
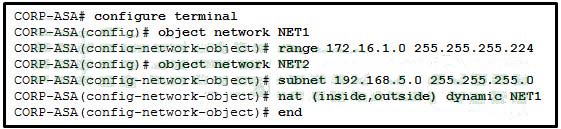
- inside NAT
- bidirectional NAT
- outside NAT
- static NAT
46. Refer to the exhibit. An administrator has entered the indicated commands on an ASA 5505. Based on the information presented, what type of remote access VPN has the administrator configured?
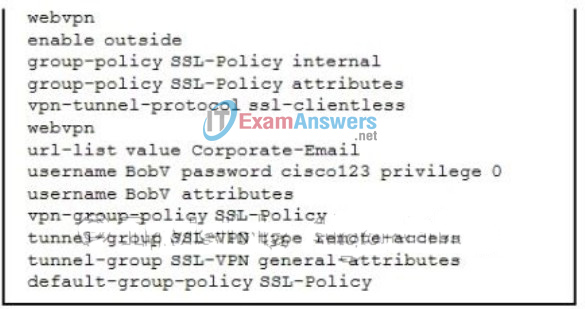
- an SSL or IPsec(IKEv2) VPN via a Cisco VPN Client
- an IPsec(IKEv1) VPN via a web browser
- a clientless SSL VPN via a web browser
- a clientless SSL VPN via the Cisco AnyConnect Client
- an IPsec(IKEv1) VPN via the Cisco VPN Client
- an SSL or IPsec(IKEv2) VPN via the Cisco AnyConnect Client
47. Which three components must be configured when implementing a clientless SSL VPN on an ASA 5505 device? (Choose three.)
- connection profile name
- bookmark lists
- group policy
48. Refer to the exhibit. Which three sets of configuration commands were entered on the ASA 5505? (Choose three.)
- interface e0/0
switchport access vlan 2
no shut
exit - interface vlan 2
nameif outside
security-level 0
ip address 209.165.200.226 255.255.255.248 - route outside 0.0.0.0 0.0.0.0 209.165.200.225
49. Which three security features do ASA models 5505 and 5510 support bydefault? (Choose three.)
- stateful firewall
- intrusion prevention system
- VPN concentrator
50. Which option lists the ASA adaptive security algorithm session management tasks in the correct order?
- 1) performing the access list checks
2) performing route lookups
3) allocating NAT translations (xlates)
4) establishing sessions in the “fast path”
51. Refer to the exhibit. According to the command output, which three statements are true about the DHCP options entered on the ASA 5505? (Choose three.)
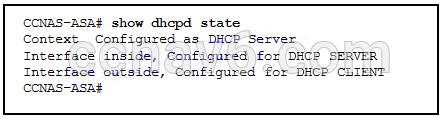
- The dhcpd auto-config outside command was issued to enable the DHCP client.
- The dhcpd enable inside command was issued to enable the DHCP server.
- The dhcpd address [start-of-pool]-[end-of-pool] inside command was issued to enable the DHCP client.
- The dhcpd address [start-of-pool]-[end-of-pool] inside command was issued to enable the DHCP server.
- The dhcpd auto-config outside command was issued to enable the DHCP server.
- The dhcpd enable inside command was issued to enable the DHCP client.
52. Refer to the exhibit. An administrator has configured an ASA 5505 as indicated but is still unable to ping the inside interface from an inside host. What is the cause of this problem?
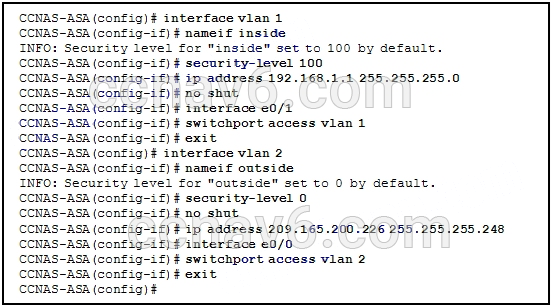
- VLAN 1 should be the outside interface and VLAN 2 should be the inside interface.
- The no shutdown command should be entered on interface Ethernet 0/1.
- The security level of the inside interface should be 0 and the outside interface should be 100.
- An IP address should be configured on the Ethernet 0/0 and 0/1 interfaces.
- VLAN 1 should be assigned to interface Ethernet 0/0 and VLAN 2 to Ethernet 0/1.
53. Refer to the exhibit. What will be displayed in the output of the show running-config object command after the exhibited configuration commands are entered on an ASA 5505?
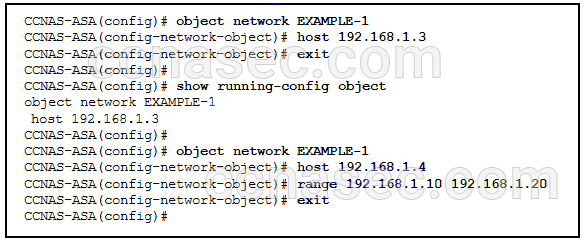
- host 192.168.1.4
- host 192.168.1.3
- range 192.168.1.10 192.168.1.20
- host 192.168.1.3, host 192.168.1.4, and range 192.168.1.10 192.168.1.20
- host 192.168.1.4 and range 192.168.1.10 192.168.1.20
- host 192.168.1.3 and host 192.168.1.4
54. Which three wizards are included in Cisco ASDM 6.4? (Choose three.)
- ADSL Connection wizard
- Advanced Firewall wizard
- High Availability and Scalability wizard
- Security Audit wizard
- Startup wizard
- VPN wizard
55. Which three types of remote access VPNs are supported on ASA devices?
- Clientless SSL VPN using the Cisco AnyConnect Client
- Clientless SSL VPN using a web browser
- IPsec (IKEv1) VPN using the Cisco VPN Client
- IPsec (IKEv1) VPN using a web browser
- SSL or IPsec (IKEv2) VPN using the Cisco AnyConnect Client
- SSL or IPsec (IKEv2) VPN using the Cisco VPN Client
56. A network administrator is configuring the security level for the ASA. What is a best practice for assigning the security level on the three interfaces?
- Outside 100, Inside 10, DMZ 40
- Outside 0, Inside 100, DMZ 50
- Outside 40, Inside 100, DMZ 0
- Outside 0, Inside 35, DMZ 90
57. When dynamic NAT on an ASA is being configured, what two parameters must be specified by network objects? (Choose two.)
- the inside NAT interface
- the outside NAT interface
- the pool of public global addresses
- a range of private addresses that will be translated
- the interface security level
