5.0 – Introduction
5.0.1 – Welcome
5.0.1.1 – Chapter 5: Networking Concepts
Computer networks allow users to share resources and to communicate. Can you imagine a world without emails, online newspapers, blogs, web sites and the other services offered by the Internet? Networks also allow users to share resources such as printers, applications, files, directories, and storage drives. This chapter provides an overview of network principles, standards, and purposes. IT professionals must be familiar with networking concepts to meet the expectations and needs of customers and network users.
You will learn the basics of network design and how devices on the network impact the flow of data. These devices include hubs, switches, access points, routers, and firewalls. Different Internet connection types such as DSL, cable, cellular and satellite are also covered. You will learn about the four layers of the TCP/IP model and the functions and protocols associated with each layer. You will also learn about many wireless networks and protocols. This includes IEEE 802.11 Wireless LAN protocols, wireless protocols for close proximity, like Frequency Identification (RFID), Near Field Communication (NFC), and smart home protocol standards like Zigbee and Z-wave. This knowledge will help you successfully design, implement, and troubleshoot networks. The chapter concludes with discussions on network cable types; twisted-pair, fiber-optic, and coaxial. You will learn how each type of cable is constructed, how they carry data signals, and appropriate use cases for each.
It is important to not only learn about computer network operation and components but also to build hands-on skills. In this chapter you will build and to test a straight-through Unshielded Twisted-Pair (UTP) Ethernet network cable.
5.1 – Network Components and Types
5.1.1 – Types of Networks
5.1.1.1 – Network Icons
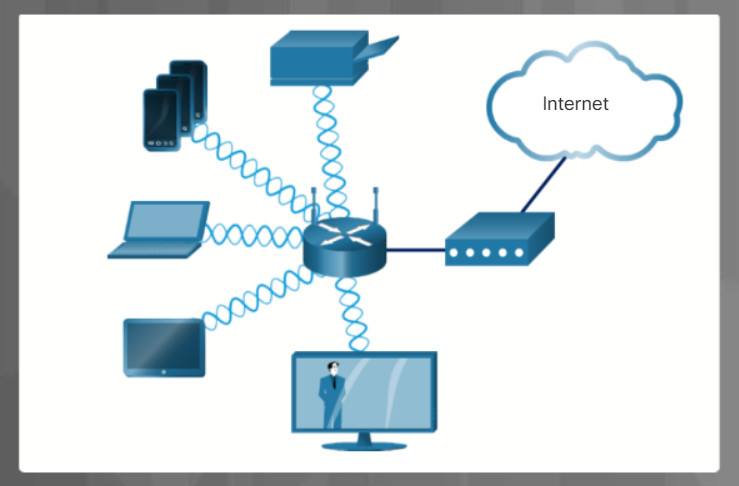
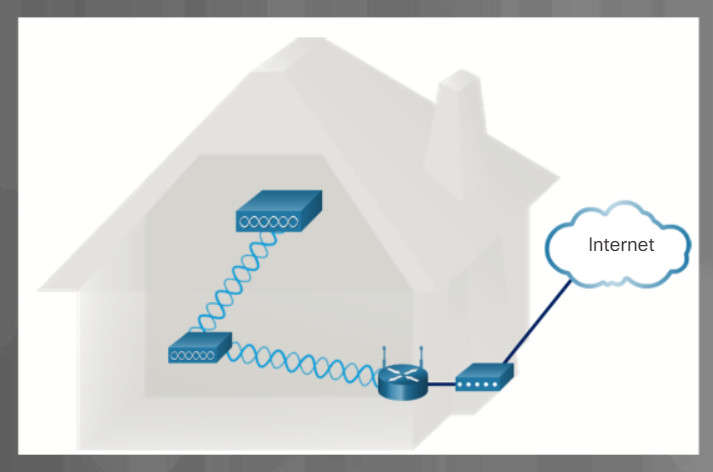
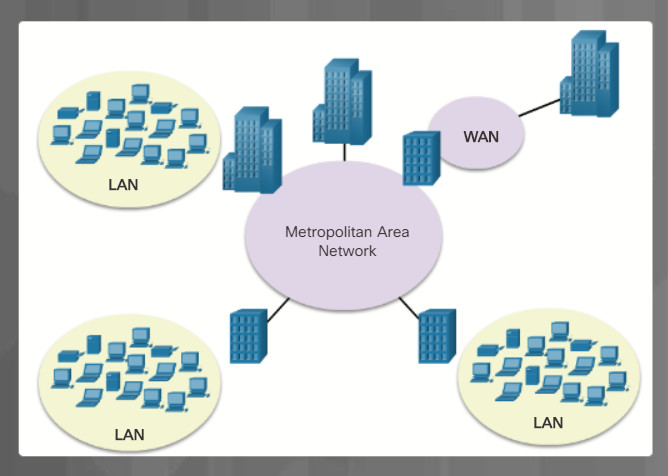
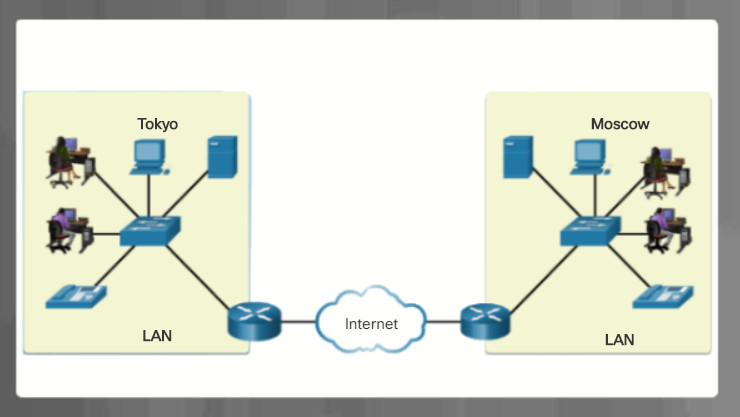
Networks are systems that are formed by links. Computer networks connect devices and users to one another. A variety of networking icons are used to represent different parts of a computer network.
Host Devices
Host Device Icons
The network devices that people are most familiar with are called end devices or host devices (Figure 1). They are called end devices because they are at the end or edge of a network. They are also called host devices because they typically host network applications, such as web browsers and email clients, that use the network to provide services to the user.
Intermediary Devices
Intermediary Devices
Computer networks contain many devices that exist in between the host devices. These intermediary devices ensure that data flows from one host device to another host device. The most common intermediary devices are shown in Figure 2:
- Switch – connects multiple devices to the network.
- Router – forwards traffic between networks.
- Wireless router – connects multiple wireless devices to the network and may include a switch to connect wired hosts.
- Access point (AP) – connects to a wireless router and is used to extend the reach of a wireless network.
- Modem – connects a home or small office to the Internet.
Network Media
Network Media Icons
Communication across a network is carried on a medium. The medium provides the channel over which the message travels from source to destination. The plural for medium is media. The icons in Figure 3 represent different types of network media. Local area network (LANs), wide area networks (WANs), and wireless networks are discussed further in this topic. The cloud is typically used in network topologies to represent connections to the internet. The internet is often the medium for communications between one network and another network.
5.1.1.2 – Network Topologies and Description
Instructions
Click each network type below for more information and an example topology.
5.1.1.3 – Check Your Understanding – Types of Networks
5.1.2 – Internet Connection Types
5.1.2.1 – Brief History of Connection Technologies
In the 1990s, internet speeds were slow compared to today, which now has the bandwidth to transmit voice and video, as well as data. A dial-up connection requires either an internal modem installed in the computer or an external modem connected by USB. The modem dial-up port is connected to a phone socket using an RJ-11 connector. Once the modem is physically installed it must be connected to one of the computer’s software COM ports. The modem must also be configured with local dialing properties such as the prefix for an outside line and the area code.
The Set Up a Connection or Network Wizard is used to configure a link to the ISP server.Connecting to the internet has evolved from analog telephone to broadband:
Analog Telephone
Analog telephone internet access can transmit data over standard voice telephone lines. This type of service uses an analog modem to place a telephone call to another modem at a remote site. This method of connection is known as dialup.
Integrated Services Digital Network
Integrated Services Digital Network (ISDN) uses multiple channels and can carry different types of services; therefore, it is considered a type of broadband. ISDN is a standard that uses multiple channels to send voice, video, and data over normal telephone wires. ISDN bandwidth is larger than traditional dialup.
Broadband
Broadband uses different frequencies to send multiple signals over the same medium. For example, the coaxial cables used to bring cable television to your home can carry computer network transmissions at the same time as hundreds of TV channels. Your cell phone can receive voice calls while also using a web browser.
Some common broadband network connections include cable, digital subscriber line (DSL), ISDN, satellite, and cellular. The figure shows equipment used to connect to or transmit broadband signals.
Broadband Technologies

Broadband Technologies
5.1.2.2 – DSL, Cable, and Fiber
Both DSL and cable use a modem to connect to the internet through an Internet Service Provider (ISP), as shown in the figure. A DSL modem connects a user’s network directly to the digital infrastructure of the phone company. A cable modem connects the user’s network to a cable service provider.
DSL
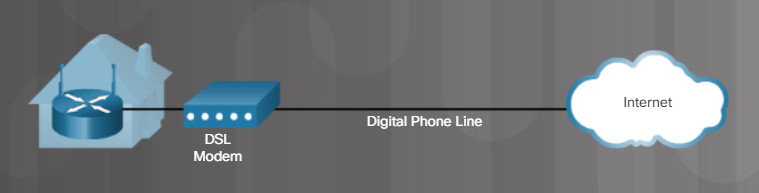
DSL Modem
DSL is an always-on service, which means that there is no need to dial up each time you want to connect to the internet. Voice and data signals are carried on different frequencies on the copper telephone wires. A filter prevents DSL signals from interfering with phone signals.
Cable
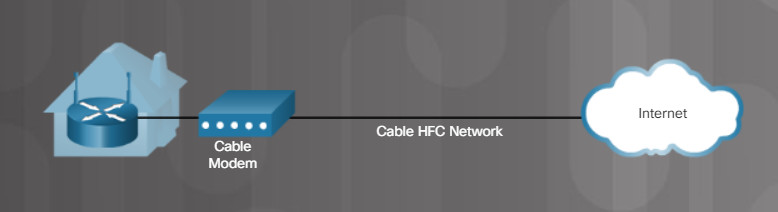
Cable Modem
A cable internet connection does not use telephone lines. Cable uses coaxial cable lines originally designed to carry cable television. A cable modem connects your computer to the cable company. You can plug your computer directly into the cable modem. However, connecting a routing device to the modem allows multiple computers to share the connection to the internet.
Fiber
Fiber optic cables are made of glass or plastic and use light to transmit data. They have a very high bandwidth, which enables them to carry large amounts of data. At some point in your connection to the internet, your data will cross a fiber network. Fiber is used in backbone networks, large enterprise environments and large data centers. Older copper cabling infrastructures closer to home and businesses are increasingly being replaced with fiber. For example, in the figure, the cable connection includes a hybrid fiber coaxial (HFC) network in which fiber is used in the last mile to the user’s home. At the user’s home, the network switches back to copper coaxial cable.
The choice of connection varies depending on geographical location and service provider availability.
5.1.2.3 – Line of Sight Wireless Internet Service
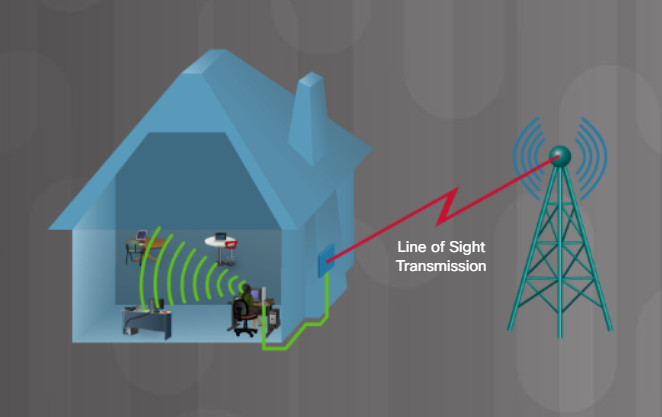
Line of sight wireless internet is an always-on service that uses radio signals for transmitting internet access, as shown in the figure. Radio signals are sent from a tower to the receiver that the customer connects to a computer or network device. A clear path between the transmission tower and customer is required. The tower may connect to other towers or directly to an internet backbone connection. The distance the radio signal can travel and still be strong enough to provide a clear signal depends on the frequency of the signal. Lower frequency of 900 MHz can travel up to 40 miles (65 km), while a higher frequency of 5.7 GHz can only travel 2 miles (3 km). Extreme weather conditions, trees, and tall buildings can affect signal strength and performance.
5.1.2.4 – Satellite
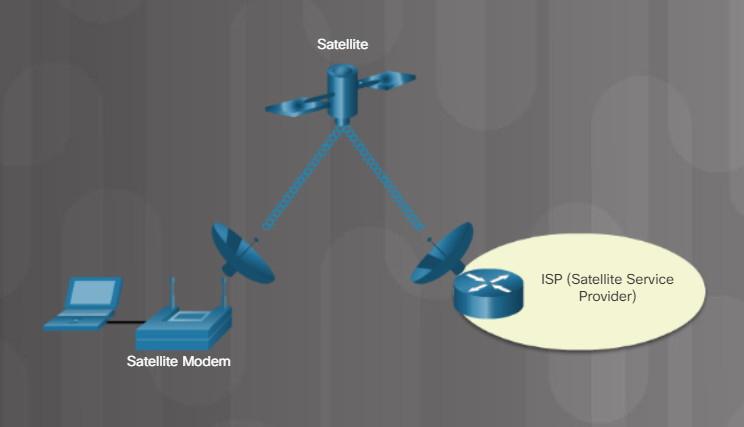
Satellite Connection
Broadband satellite is an alternative for customers who cannot get cable or DSL connections. A satellite connection does not require a phone line or cable, but uses a satellite dish for two-way communication. The satellite dish transmits and receives signals to and from a satellite that relays these signals back to a service provider, as shown in the figure. Download speeds can reach up to 10Mb/s or more, while upload speed ranges about 1/10th of download speeds. It takes time for the signal from the satellite dish to relay to your ISP through the satellite orbiting the Earth. Due to this latency, it is difficult to use time-sensitive applications, such as video gaming, Voice over Internet Protocol (VoIP), and video conferencing.
5.1.2.5 – Cellular
Cell phone technology relies on cell towers distributed throughout the user’s coverage area to provide seamless access to cell phone services and the internet. With the advent of the third-generation (3G) of cellular technology, smartphones could access the internet. Download and upload speeds continue to improve with each iteration of cell phone technology.
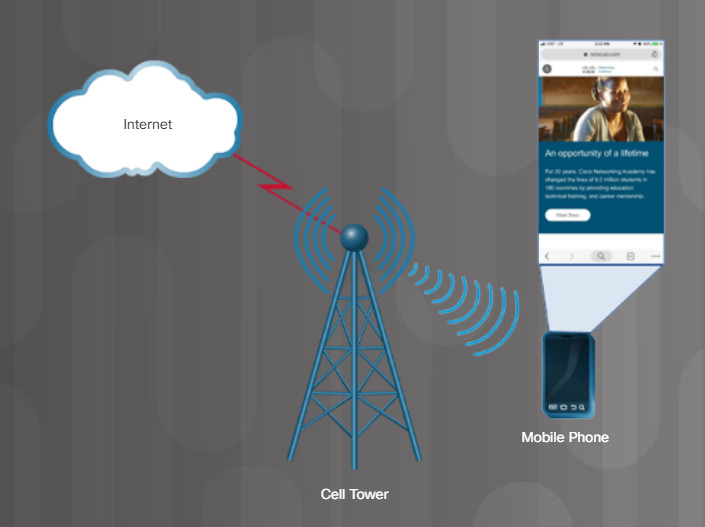
Cell Technology for Internet Access
In some regions of the world, smartphones are the only way users access the internet. In the United States, users are increasingly relying on smartphones for internet access. According to the Pew Research Center, in 2018 20% of adults in the United States do not use broadband at home (28% for adults 18-29). Instead, they use a smartphone for personal internet access. Search for “pew internet research” for more interesting statistics.
5.1.2.6 – Mobile Hotspot and Tethering
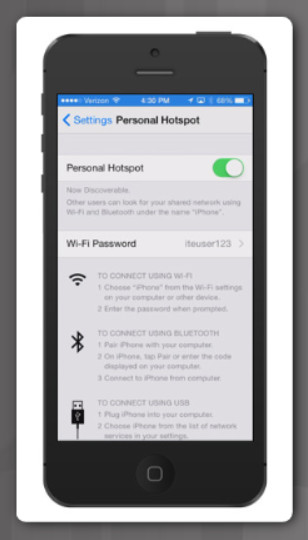
Personal Hotspot
Many cell phones provide the ability to connect other devices, as shown in the figure. This connection, known as tethering, can be made using Wi-Fi, Bluetooth, or by using a USB cable. Once a device is connected, it is able to use the phone’s cellular connection to access the Internet. When a cellular phone allows Wi-Fi devices to connect and use the mobile data network, it is called a mobile hotspot.
5.1.2.7 – Check Your Understanding – Internet Connection Types
5.2 – Networking Protocols, Standards, and Services
5.2.1 – Transport Layer Protocols
5.2.1.1 – Video Explanation – Transport Layer Protocols
Click Play in the figure to view a video about transport layer protocols.
Click here to read the transcript of this video.
5.2.1.2 – Activity – Transport Layer Protocols
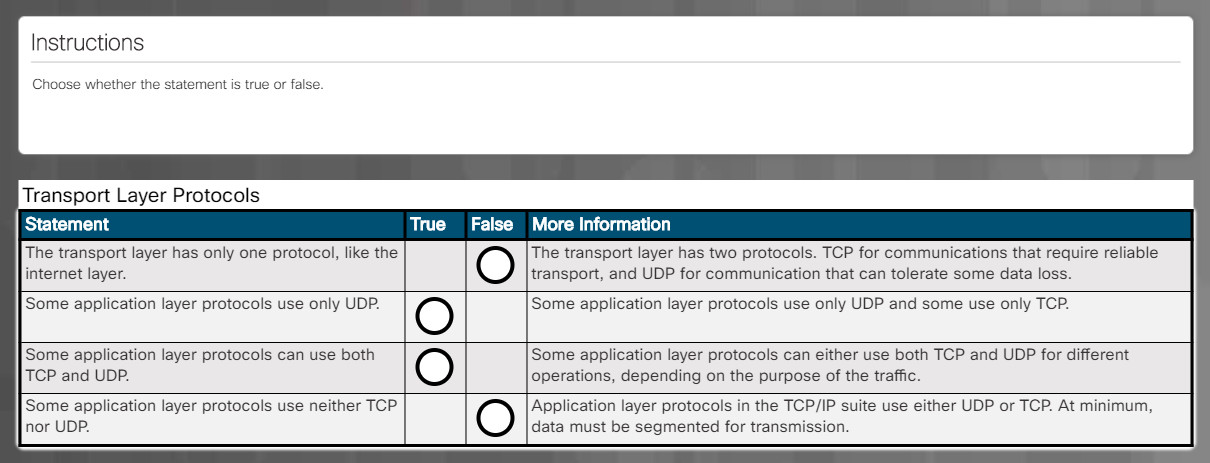
5.2.1.3 – The TCP/IP Model
The TCP/IP model consists of layers that perform functions necessary to prepare data for transmission over a network. TCP/IP stands for two important protocols in the model: Transmission Control Protocol (TCP) and Internet Protocol (IP). TCP is responsible for tracking all the network connections between a user’s device and multiple destinations. The Internet Protocol (IP) is responsible for adding addressing so that data can be routed to the intended destination.
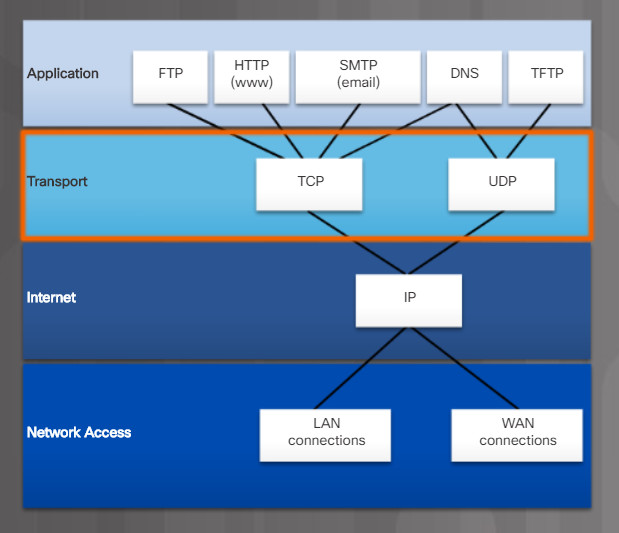
Two Transport Layer Protocols
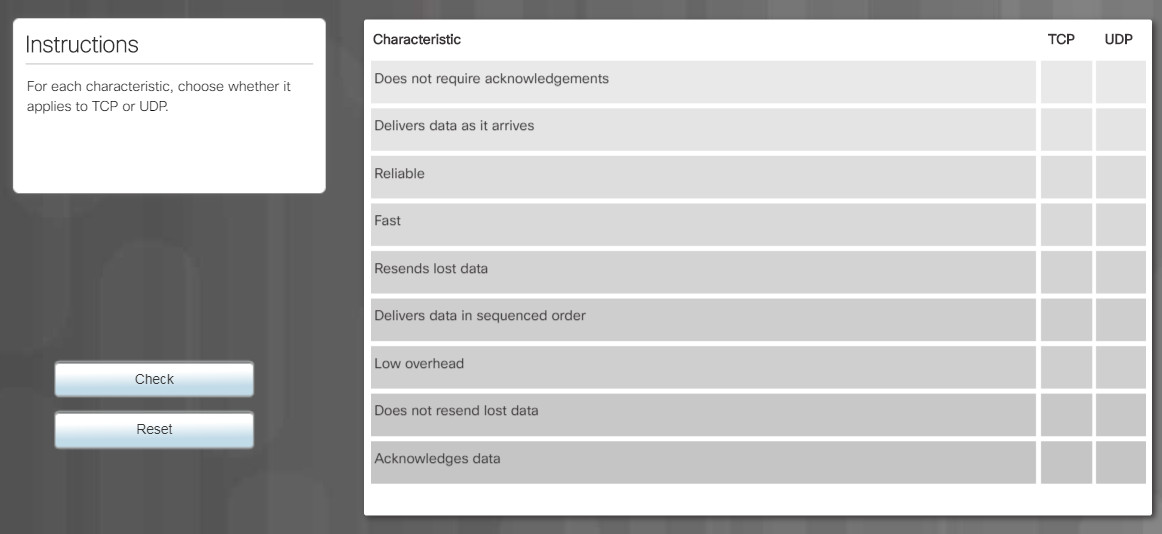
The two protocols that operate at the transport layer are TCP and User Datagram Protocol (UDP), as shown in Figure 1. TCP is considered a reliable, full-featured transport layer protocol, which ensures that all of the data arrives at the destination. In contrast, UDP is a very simple transport layer protocol that does not provide for any reliability. Figure 2 highlights the TCP and UDP properties.
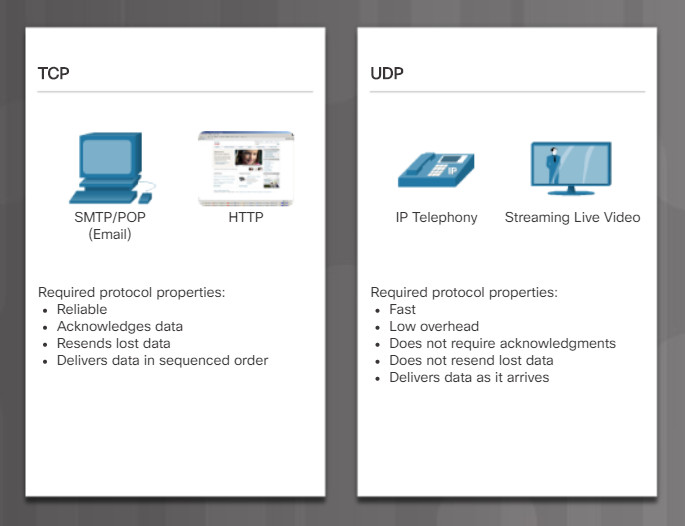
TCP and UDP Properties
5.2.1.4 – TCP
TCP transport is analogous to sending packages that are tracked from source to destination. If a shipping order is broken up into several packages, a customer can check online to see the order of the delivery.
With TCP, there are three basic operations of reliability:
- Numbering and tracking data segments transmitted to a specific device from a specific application
- Acknowledging received data
- Retransmitting any unacknowledged data after a certain period of time
Click Play in the figure to see how TCP segments and acknowledgments are transmitted between sender and receiver.
5.2.1.5 – UDP
UDP is similar to placing a regular, non-registered, letter in the mail. The sender of the letter is not aware of the availability of the receiver to receive the letter. Nor is the post office responsible for tracking the letter or informing the sender if the letter does not arrive at the final destination.
UDP provides the basic functions for delivering data segments between the appropriate applications, with very little overhead and data checking. UDP is known as a best-effort delivery protocol. In the context of networking, best-effort delivery is referred to as unreliable because there is no acknowledgment that the data is received at the destination.
Click Play in the figure to see an animation of UDP segments being transmitted from sender to receiver.
5.2.1.6 – Check Your Understanding – Transport Layer Protocols
5.2.2 – Application Port Numbers
5.2.2.1 – Video Explanation – Application Port Numbers
Click Play in the figure to view a video about application port numbers.
Click here to read the transcript of this video.
5.2.2.2 – Classify Application Port Numbers
TCP and UDP use a source and destination port number to keep track of application conversations. The source port number is associated with the originating application on the local device. The destination port number is associated with the destination application on the remote device. These are not physical ports. They are numbers that are used by TCP and UDP to identify the applications that should handle the data.
The source port number is dynamically generated by the sending device. This process allows multiple conversations to occur at the same time for the same application. For example, when you use a web browser, you can have more than one tab open at a time. The destination port number is 80 for regular web traffic or 443 for secure web traffic. These are called well-known port numbers because they are consistently used by most webservers on the Internet. Source port numbers will be different for each tab opened. This is how your computer knows which browser tab to deliver the web content to. Similarly, other network applications like email and file transfer have their own assigned port numbers.
There are a number of different types of application layer protocols that are identified by TCP or UDP port numbers at the transport layer.
-
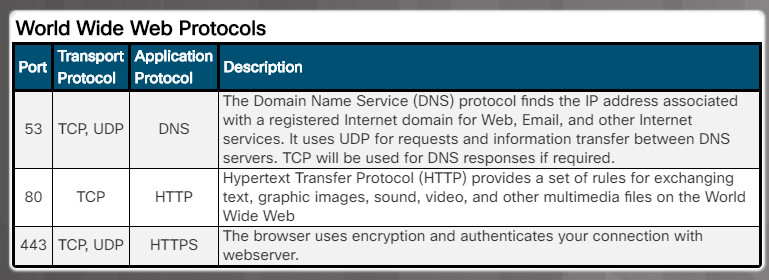
- World Wide Web related protocols (Figure 1)
-
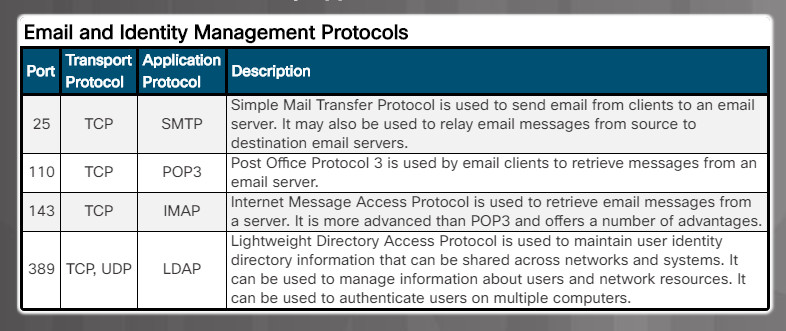
- Email and identity management protocols. (Figure 2)
-
- File transport and management protocols (Figure 3)
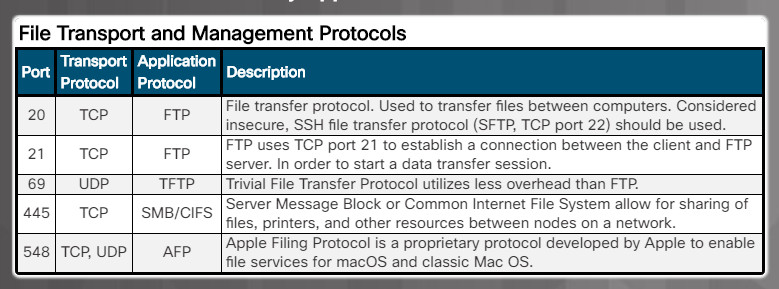
-
- Remote access protocols. (Figure 4)
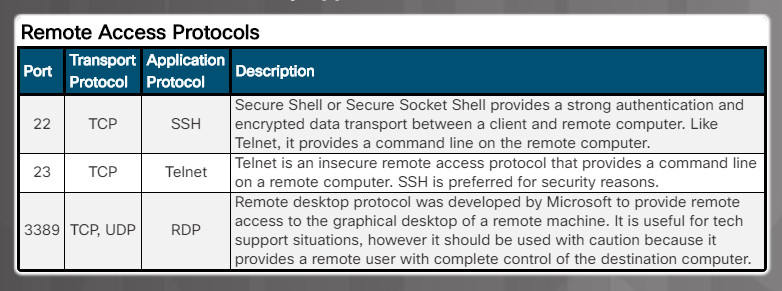
-
- Network operations protocols. (Figure 5)
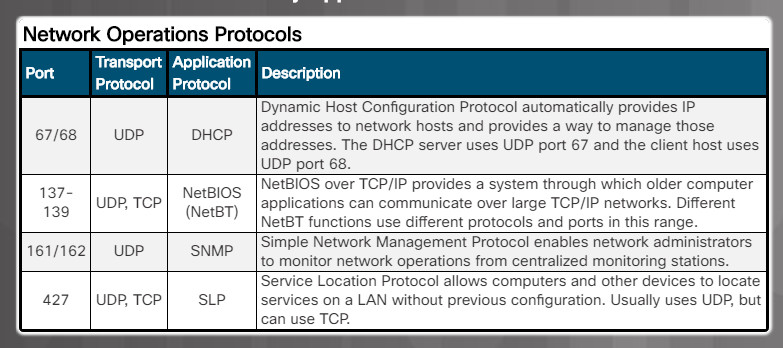
Figure 6 shows a summary table of all of these application protocols listed in protocol order.
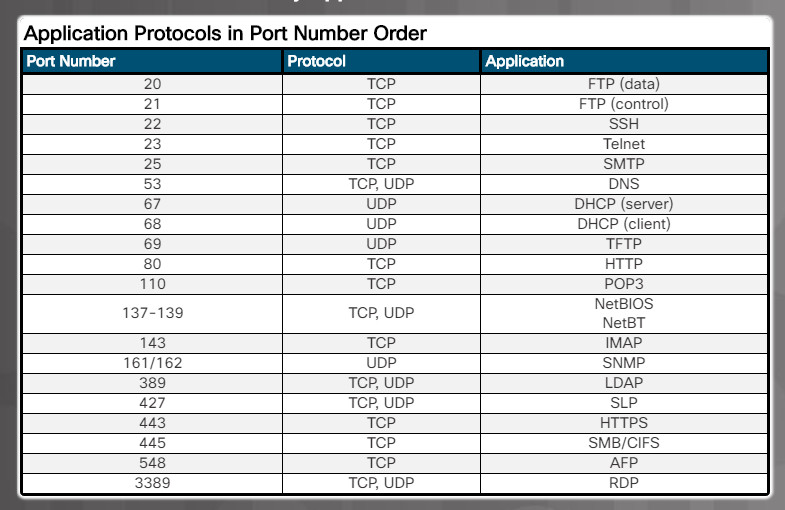
5.2.2.3 – Check Your Understanding – Application Port Numbers



5.2.3 – Wireless Protocols
5.2.3.1 – WLAN Protocols
The Institute of Electrical and Electronic Engineers’ (IEEE) standards for Wi-Fi as specified in the 802.11 collective group of standards that specify the radio frequencies, speeds, and other capabilities for WLANs. Various implementations of the IEEE 802.11 standards have been developed over the years, as shown in the figure.
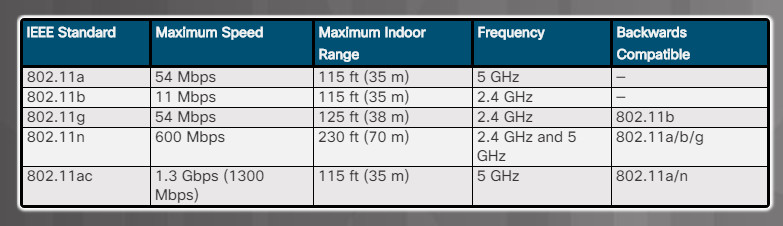
Comparing 802.11 Standards
The 802.11a, 802.11b, and 802.11g standards should be considered legacy. New WLANs should implement 802.11ac devices. Existing WLAN implementations should upgrade to 802.11ac when purchasing new devices.
5.2.3.2 – Bluetooth, NFC, and RFID
Wireless protocols for close proximity connectivity include Bluetooth, Radio Frequency Identification (RFID), and Near Field Communication (NFC).
Bluetooth
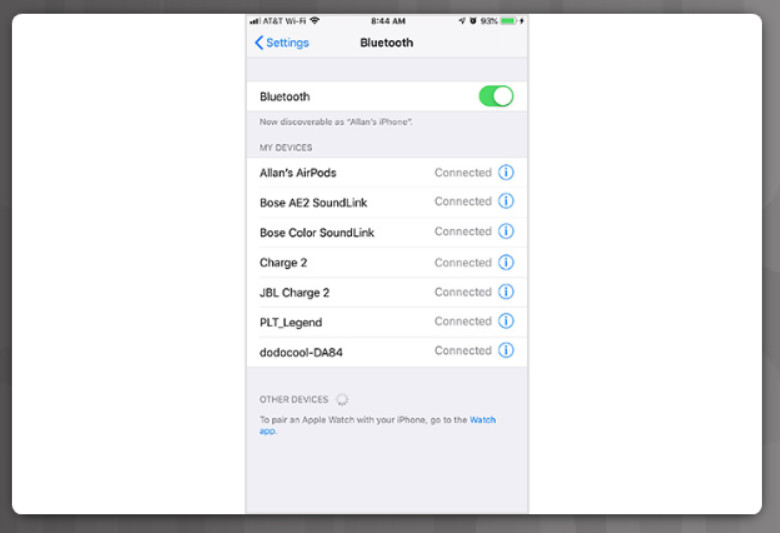
iPhone Bluetooth Settings
A Bluetooth device can connect up to seven other Bluetooth devices, as shown in Figure 1. Described in the IEEE standard 802.15.1, Bluetooth devices operate in the 2.4 to 2.485 GHz radio frequency range and is typically used for PANs. The Bluetooth standard incorporates Adaptive Frequency Hopping (AFH). AFH allows signals to “hop” around using different frequencies within the 2.4 to 2.485 GHz range, thereby reducing the chance of interference when multiple Bluetooth devices are present.
RFID

RFID Barcode Reader
RFID uses the frequencies within the 125 MHz to 960 MHz range to uniquely identify items, such as in a shipping department as shown in Figure 2. Active RFID tags that contain a battery can broadcast their ID up to 100 meters. Passive RFID tags rely on the RFID reader to use radio waves to activate and read the tag. Passive RFID tags are typically used for close scanning but have a range of up to 25 meters.
NFC

NFC Payment
NFC uses frequency 13.56 MHz and is a subset of the RFID standards. NFC is designed to be a secure method to complete transactions. For example, a consumer pays for good or services by waving the phone near the payment system, as shown in Figure 3. Based on a unique ID, the payment is charged directly against a pre-paid account or bank account. NFC is also used in mass-transportation services, the public parking sector, and many more consumer areas.
5.2.3.3 – Zigbee and Z-Wave
Zigbee and Z-Wave are two smart home standards that allow users to connect multiple devices in a wireless mesh network. Typically, the devices are then managed from a smartphone app, as shown in the figure.
Zigbee
Zigbee uses low-power digital radios based on the IEEE 802.15.4 wireless standard for low-rate wireless personal area networks (LR-WPANs) that is meant to be used by low-cost, low-speed devices. Zigbee operates within frequencies from 868 MHz to 2.4 GHz and is limited to 10 to 20 meters. Zigbee has a data rate from 40-250 kb/s and can support approximately 65,000 devices.
The ZigBee specification relies on a main device called a ZigBee Coordinator. Tasked with managing all ZigBee client devices, the ZigBee Coordinator is responsible for the creation and maintenance of the ZigBee network.
Although Zigbee is an open standard, software developers must be a paid member of the Zigbee Alliance to use and contribute to the standard.
Z-Wave
Z-Wave technology is a proprietary standard that is now owned by Silicon Labs. However, a public version of the interoperability layer of Z-Wave was open sourced in 2016. These open source Z-Wave standards include Z-Wave’s S2 security, Z/IP for transporting Z-Wave signals over IP networks, and Z-Ware middleware.
Z-Wave operates within a variety of frequencies based on the country from 865.2 MHz in India to 922 – 926 MHz in Japan. Z-Wave operates at 908.42 MHz in the North America. Z-Wave can transmit data up to 100 meters but has a slower data rate than Zigbee at 9.6-100 kb/s. Z-Wave can support up to 232 devices in one wireless mesh network.
Search the internet for “Zigbee and Z-Wave” to learn the latest information about these two smart home standards.
The Smart Home Market

Smart Home Wireless Control
The market for smart home products continues to grow. According to Statista.com, the number of smart homes was 34.8 million in 2018, which was a 28.4% increase from 2017. The smart home market will continue to provide economic opportunities for individuals and companies.
5.2.3.4 – Cellular Generations
Instructions
Cellular technology uses a cell phone network to connect to the internet. Performance will be limited by the capabilities of the phone and the cell tower to which it is connected. Cellular technology has evolved through multiple generations (the “G” in abbreviation). Click each cellular technology for a brief description.
5.2.3.5 – Check Your Understanding – Wireless Protocols

5.2.4 – Network Services
5.2.4.1 – Video Explanation – Network Services
Click Play in the figure to view a video about network services.
Click here to read the transcript of this video.
5.2.4.2 – Client – Server Roles
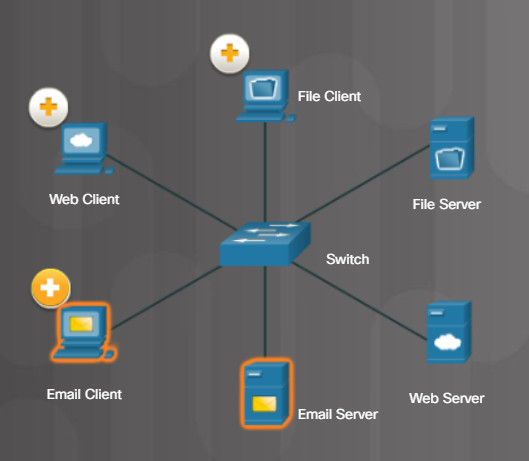
All computers connected to a network that participate directly in network communication are classified as hosts. Hosts are also called end devices. Hosts on networks perform a certain role. Some of these hosts perform security tasks, while others provide web services. There are also many legacy or embedded systems that perform specific tasks such as file or print services. Hosts that provide services are called servers. Hosts that use these services are called clients.
Each service requires separate server software. For example, a server requires web server software in order to provide web services to the network. A computer with server software can provide services simultaneously to one or many clients. Additionally, a single computer can run multiple types of server software. In a home or small business, it may be necessary for one computer to act as a file server, a web server, and an email server.
Clients need software installed in order to request and display the information obtained from the server. An example of client software is a web browser, like Chrome or FireFox. A single computer can also run multiple types of client software. For example, a user can check email and view a web page while instant messaging and listening to Internet radio.
The File Server stores corporate and user files in a central location. The client devices access these files with client software such as Windows Explorer.
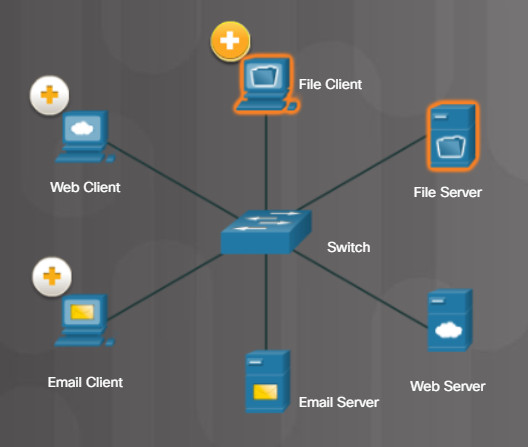
The Web Server runs web server software and clients use their browser software, such as Windows Internet Explorer, to access web pages on the server.
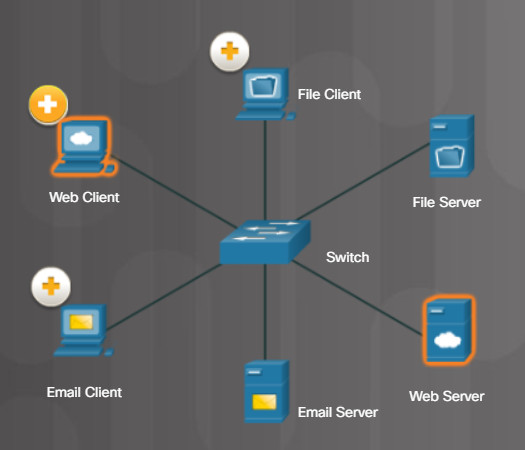
The Email Server runs email server software and clients use their mail client software, such as Microsoft Outlook, to access email on the server.
5.2.4.3 – DHCP Server
A host needs IP address information before it can send data on the network. Two important IP address services are Dynamic Host Configuration Protocol (DHCP) and Domain Name Service (DNS).
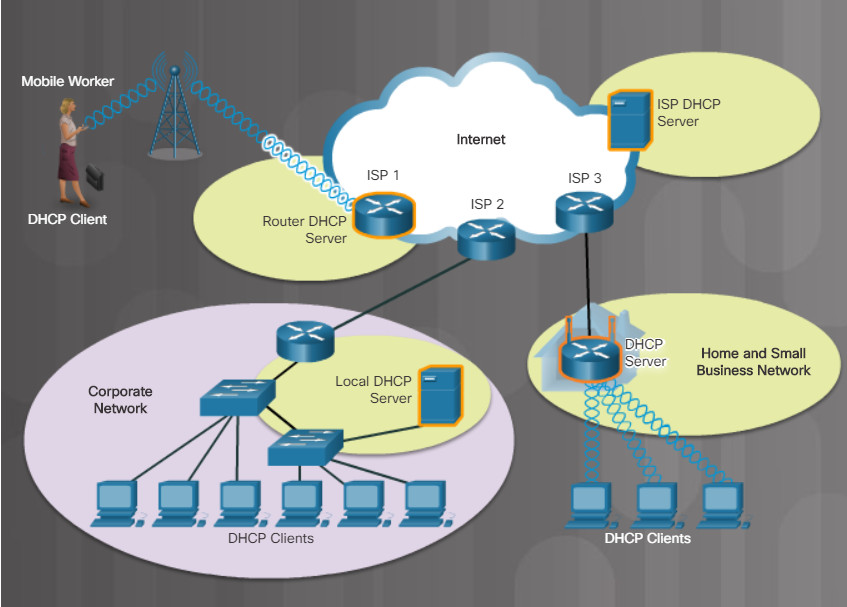
5.2.4.3 DHCP Server
DHCP is the service used by ISPs, network administrators, and wireless routers to automatically assign IP addressing information to hosts, as shown in the figure.
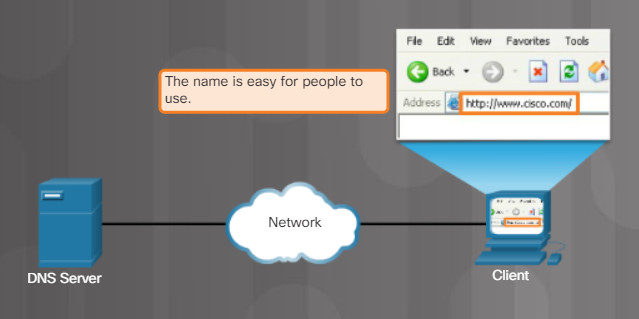
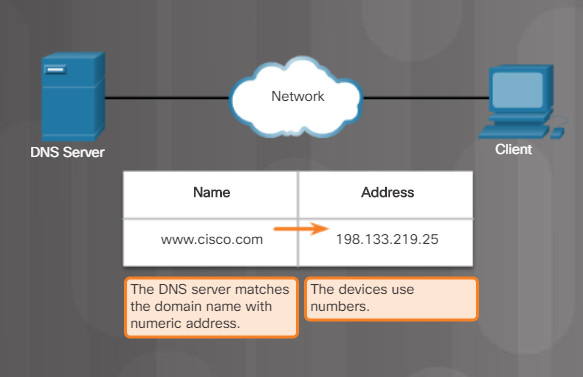
5.2.4.4 – DNS Server
DNS is the method computers use to translate domain names into IP addresses. On the internet, domain names, such as http://www.cisco.com, are much easier for people to remember than 198.133.219.25, which is the actual numeric IP address for this server. If Cisco decides to change the numeric IP address of www.cisco.com, it is transparent to the user because the domain name remains the same. The new address is simply linked to the existing domain name and connectivity is maintained.
Figures 1 through 5 display the steps involved in DNS resolution.
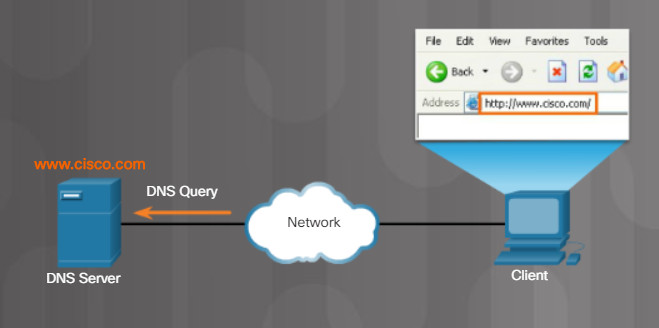
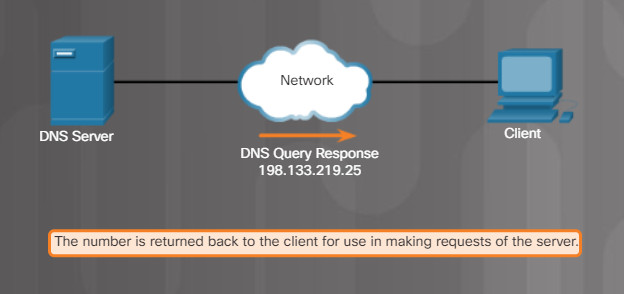
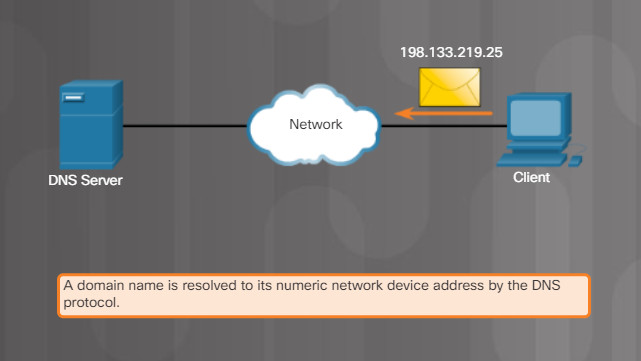
5.2.4.5 – Print Server

5.2.4.5 Print Server
Print servers enable multiple computer users to access a single printer. A print server has three functions:
-
- Provide client access to print resources.
-
- Administer print jobs by storing them in a queue until the print device is ready for them and then feeding or spooling the print information to the printer.
- Provide feedback to users.
5.2.4.6 – File Server
The File Transfer Protocol (FTP) provides the ability to transfer files between a client and a server. An FTP client is an application that runs on a computer that is used to push and pull files from a server running FTP as a service.
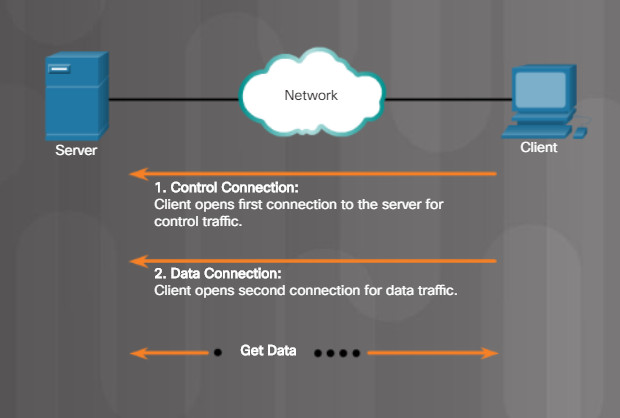
5.2.4.6 File Server
As the figure illustrates, to successfully transfer files, FTP requires two connections between the client and the server, one for commands and replies, the other for the actual file transfer.
FTP has many security weaknesses. Therefore, a more secure file transfer services should be used, such as one of the following:
-
- File Transfer Protocol Secure (FTPS) – An FTP client can request the file transfer session be encrypted. The file server can accept or deny the request.
- SSH File Transfer Protocol (SFTP) – As an extension to Secure Shell (SSH) protocol, SFTP can be used to establish a secure file transfer session.
- Secure Copy (SCP) – SCP also uses SSH to secure file transfers.
5.2.4.7 – Web Server
Web resources are provided by a web server. The host accesses the web resources using the Hypertext Transfer Protocol (HTTP) or the secure HTTP (HTTPS). HTTP is a set of rules for exchanging text, graphic images, sound, and video on the World Wide Web. HTTPS adds encryption and authentication services using Secure Sockets Layer (SSL) protocol or the newer Transport Layer Security (TLS) protocol. HTTP operates on port 80. HTTPS operates on port 443.
To better understand how the web browser and web server interact, we can examine how a web page is opened in a browser. For this example, use the http://www.cisco.com/index.html URL.
First, as shown in Figure 1, the browser interprets the three parts of the URL:
1. http (the protocol or scheme)
2. www.cisco.com (the server name)
3. index.html (the specific filename requested)

HTTP Protocol
The browser then checks with a Domain Name Server (DNS) to convert www.cisco.com into a numeric address, which it uses to connect to the server. Using HTTP requirements, the browser sends a GET request to the server and asks for the index.html file, as shown in Figure 2.
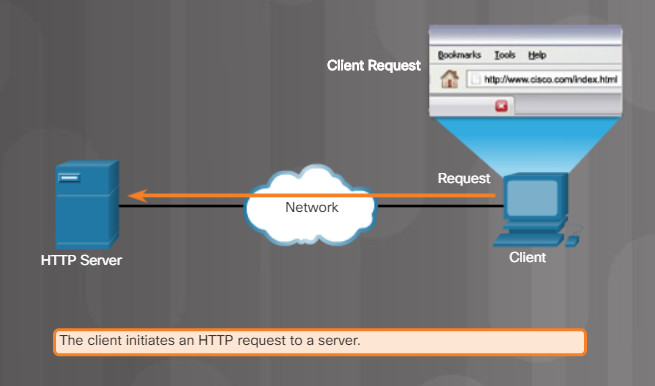
HTTP Protocol Step 1
The server sends the HTML code for this web page back to the client’s browser, as shown in Figure 3.
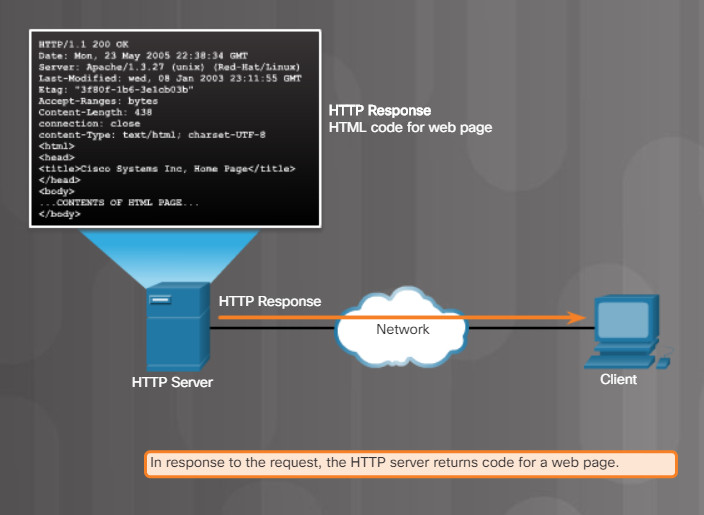
HTTP Protocol Step 2
Finally, as shown in Figure 4, the browser interprets the HTML code and formats the page for the browser window.
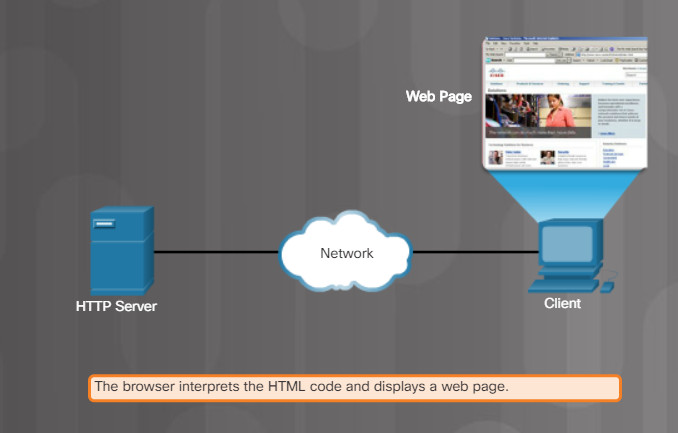
HTTP Protocol Step 3
5.2.4.8 – Mail Server
Email requires several applications and services, as shown in the figure. Email is a store-and-forward method of sending, storing, and retrieving electronic messages across a network. Email messages are stored in databases on mail servers.
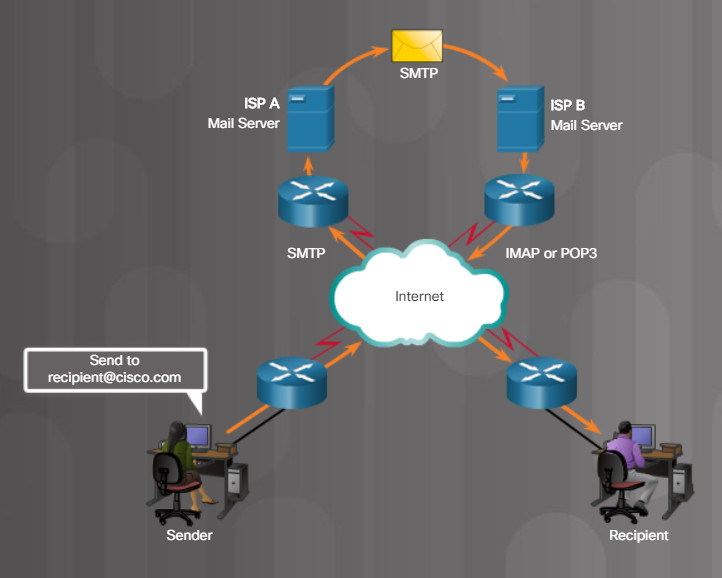
5.2.4.8 – Mail Server
Email clients communicate with mail servers to send and receive email. Mail servers communicate with other mail servers to transport messages from one domain to another. An email client does not communicate directly with another email client when sending email. Instead, both clients rely on the mail server to transport messages.
Email supports three separate protocols for operation: Simple Mail Transfer Protocol (SMTP), Post Office Protocol (POP), and Internet Message Access Protocol (IMAP). The application layer process that sends mail uses SMTP. A client retrieves email using one of the two application layer protocols: POP or IMAP.
5.2.4.9 – Proxy Server
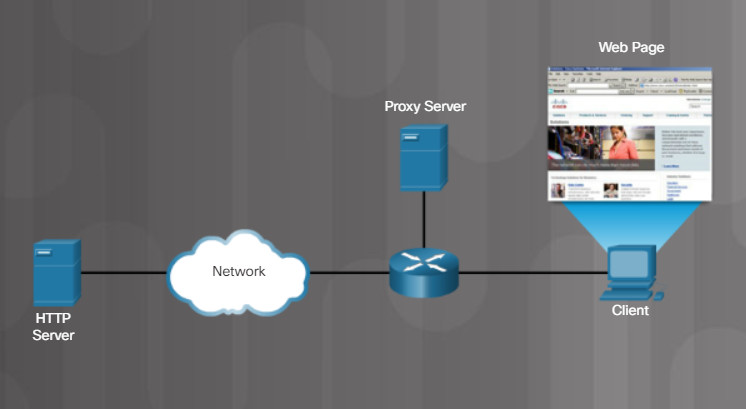
Proxy Server Caches Web Pages
Proxy servers have the authority to act as another computer. A popular use for proxy servers is to act as storage or cache for web pages that are frequently accessed by devices on the internal network. For example, the proxy server in the figure is storing the web pages for www.cisco.com. When any internal host sends an HTTP GET request to www.cisco.com, the proxy server completes the following steps:
1. It intercepts the requests.
2. It checks to see if the website content has changed.
3. If not, the proxy server responds to host with the web page.
In addition, a proxy server can effectively hide the IP addresses of internal hosts because all requests going out to the internet are sourced from the proxy server’s IP address.
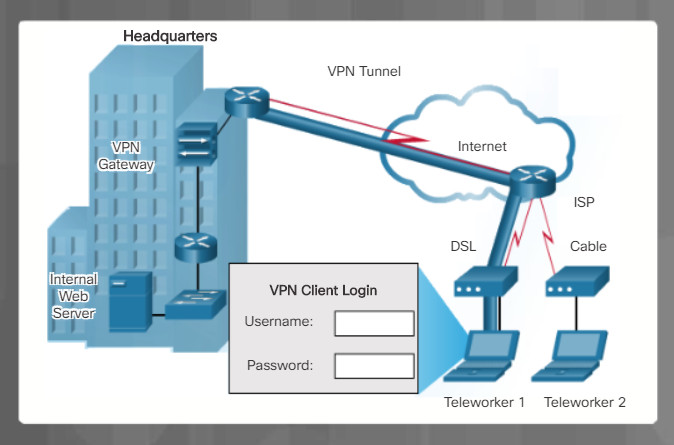
5.2.4.10 – Authentication Server
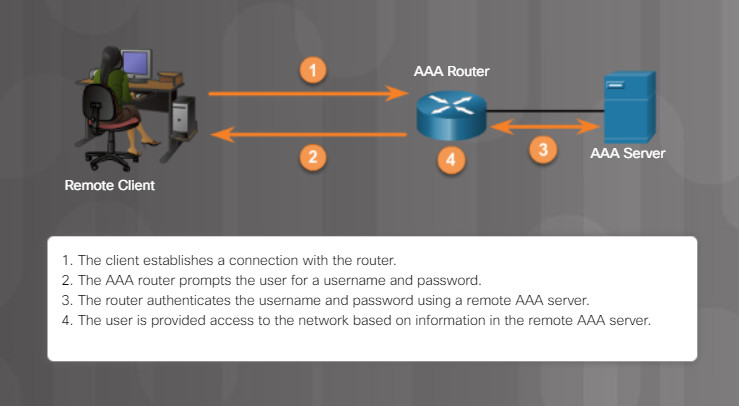
AAA Authentication
Access to network devices is typically controlled through authentication, authorization, and accounting services. Referred to as AAA or “triple A”, these services provide the primary framework to set up access control on a network device. AAA is a way to control who is permitted to access a network (authenticate), what they can do while they are there (authorize), and track what actions they perform while accessing the network (accounting).
In the figure, the remote client goes through a four-step process to authenticate with a AAA server and gain access to the network.
5.2.4.11 – Syslog Server
Many networking devices support syslog, including routers, switches, application servers, firewalls, and other network appliances. The syslog protocol allows networking devices to send their system messages across the network to syslog servers.
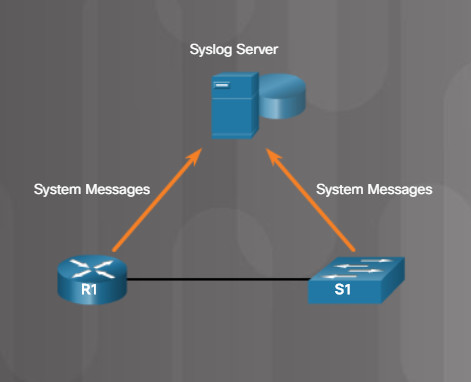
5.2.4.11 Syslog Server
The syslog logging service provides three primary functions:
- The ability to gather logging information for monitoring and troubleshooting
- The ability to select the type of logging information that is captured
- The ability to specify the destinations of captured syslog messages
5.2.4.12 – Check Your Understanding – Network Services
5.3.1 – Basic Network Devices
5.3.1.1 – Video Explanation – Basic Network Devices
Click Play in the figure to view a video about basic network devices.
Click here to read the transcript of this video.
5.3.1.2 – Network Interface Card
A network interface card (NIC) provides the physical connection to the network at the PC or other end device. As shown in the figure, there are different types of NICs. Ethernet NICs are used to connect to Ethernet networks and wireless NICs are used to connect to 802.11 wireless networks. Most NICs in desktop computers are integrated into the motherboard or connected to an expansion slot. NICs are also available in a USB form factor.

Types of NICs
A NIC also performs the important function of addressing data with the NIC’s media access control (MAC) address and sending the data out as bits on the network. NICs found on most computers today are gigabit Ethernet (1000 Mbps) capable.
Note: Today’s computers and motherboards typically have NICs built in including wireless capability. Refer to the manufacturer’s specifications for more information.
5.3.1.3 – Repeaters, Bridges, and Hubs
In the early days of networking, solutions like using repeaters, hubs, and bridges were created to add more devices to the network.
- Repeater
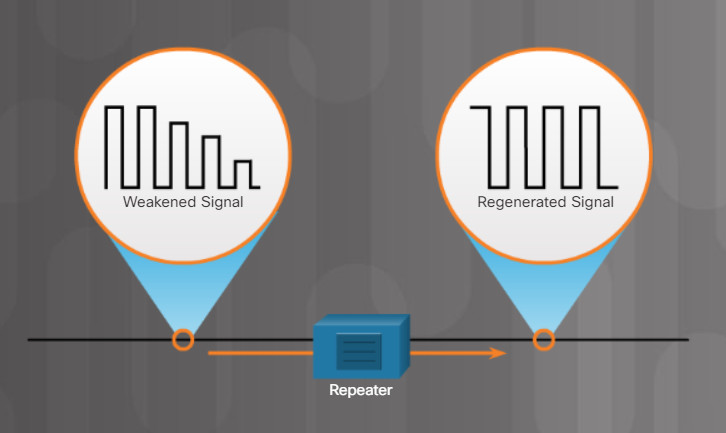
Repeater
Regenerating weak signals is the primary purpose of a repeater, as shown in Figure 1. Repeaters are also called extenders because they extend the distance a signal can travel. In today’s networks, repeaters are most often used to regenerate signals in fiber-optic cables. Also, every networking device that receives and sends data regenerates the signal.
- Hub
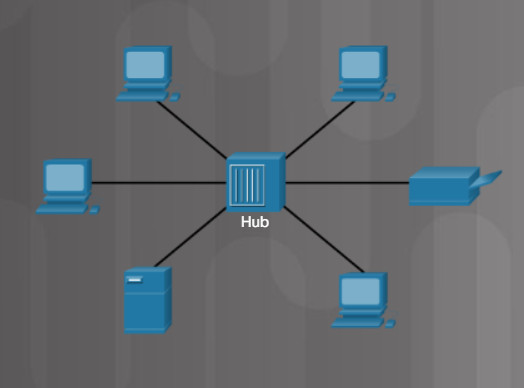
Hubs Connect Devices in a LAN
Hubs, shown in Figure 2, receive data on one port and then send it out to all other ports. A hub extends the reach of a network because it regenerates the electrical signal. Hubs can also connect to another networking device, such as a switch or router, which connects to other sections of the network.
Hubs are legacy devices and should not be used in today’s networks. Hubs do not segment network traffic. When one device sends traffic, the hub floods that traffic to all other devices connected to the hub. The devices are sharing the bandwidth.
- Bridge
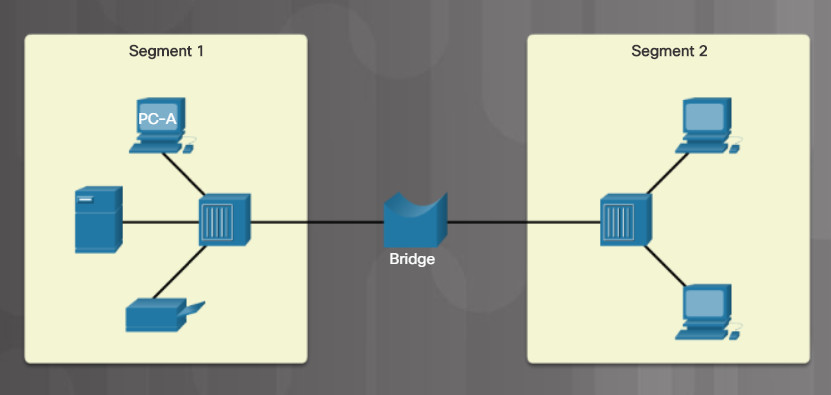
Bridges Segment a LAN
Bridges were introduced to divide LANs into segments. Bridges keep a record of all the devices on each segment. A bridge can then filter network traffic between LAN segments. This helps reduce the amount of traffic between devices. For example, in Figure 3, if PC-A needs to send a job to the printer, the traffic will not be forward to Segment 2. However, the server will also receive this print job traffic.
5.3.1.4 – Switches
Bridges and hubs are now considered legacy devices because of the benefits and low cost of switches. As shown in the figure, a switch microsegments a LAN. Microsegmenting means that switches filter and segment network traffic by sending data only to the device to which it is sent. This provides higher dedicated bandwidth to each device on the network. When PC-A sends a job to the printer, only the printer receives the traffic. Both switches and legacy bridges perform microsegmentation, however, switches perform this filtering and forwarding operation in hardware, and also include additional features.
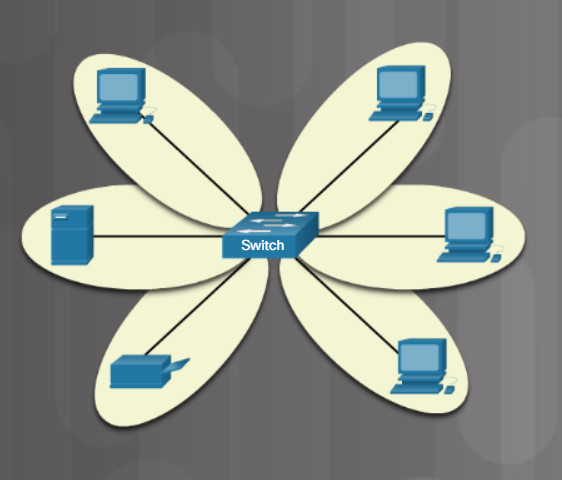
Switches Microsegment a LAN
Switch Operation
Every device on a network has a unique media access control (MAC) address. This address is hardcoded by the manufacturer of the NIC. As devices send data, switches enter the device’s MAC address into a switching table that records the MAC address for each device connected to the switch, and records which switch port can be used to reach a device with a given MAC address. When traffic arrives that is destined for a particular MAC address, the switch uses the switching table to determine which port to use to reach the MAC address. The traffic is forwarded out the port to the destination. By sending traffic out of only one port to the destination, other ports are not affected.
Managed and Unmanaged Switches
In larger networks, network administrators typically install managed switches. Managed switches come with additional features that the network administrator can configure to improve the functionality and security of the network. For example, a managed switch can be configured with VLANs and port security.
In a home or small business network, you probably do not need the added complexity and expense of a managed switch. Instead, you might consider installing an unmanaged switch. These switches typically have no management interface. You simply plug them into the network and attach network devices to benefit from a switch microsegmentation features.
5.3.1.5 – Wireless Access Points
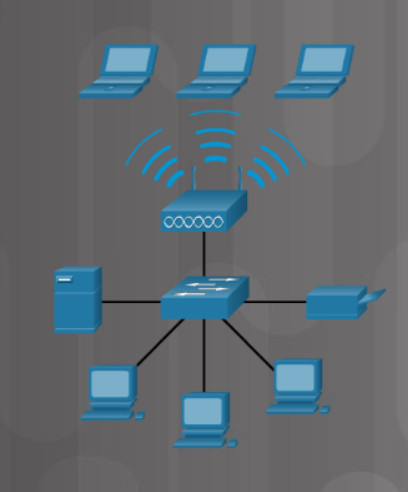
5.3.1.5 Wireless Access Points
Wireless access points (APs), shown in the figure, provide network access to wireless devices, such as laptops and tablets. The wireless AP uses radio waves to communicate with the wireless NIC in the devices and other wireless access points. An access point has a limited range of coverage. Large networks require several access points to provide adequate wireless coverage. A wireless access point provides connectivity only to the network, while a wireless router provides additional features.
5.3.1.6 – Routers
Switches and wireless APs forward data within a network segment. Routers can have all the functionality of a switch or a wireless AP. However, routers connect networks, as shown in the figure. Switches use MAC addresses to forward traffic within a single network. Routers use IP addresses to forward traffic to other networks. In larger networks, routers connect to switches, which then connect to LANs, like the router on the right in the figure. The router serves as the gateway to outside networks.
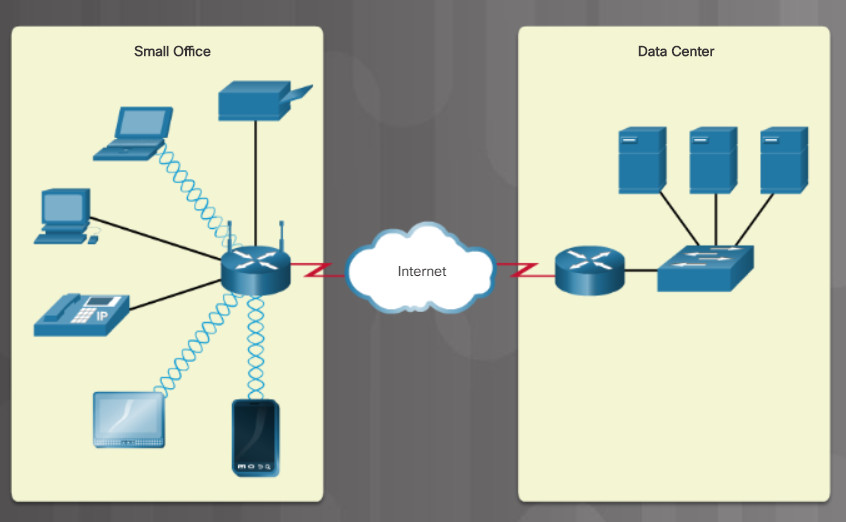
The router on the left in the figure is also known as a multipurpose device or integrated router. It includes a switch and a wireless access point. For some networks, it is more convenient to purchase and configure one device that serves all your needs than to purchase a separate device for each function. This is especially true for the home or small office. Multipurpose devices may also include a modem for connecting to the internet.
5.3.1.7 – Check Your Understanding – Basic Network Devices
5.3.2 – Security Devices
5.3.2.1 – Video Explanation – Security Devices
Click Play in the figure to view a video about security devices.
Click here to read the transcript of this video.
5.3.2.2 – Firewalls
An integrated router typically contains a switch, a router, and a firewall, as shown in the figure. Firewalls protect data and equipment on a network from unauthorized access. A firewall resides between two or more networks. It does not use the resources of the computers it is protecting, so there is no impact on processing performance.
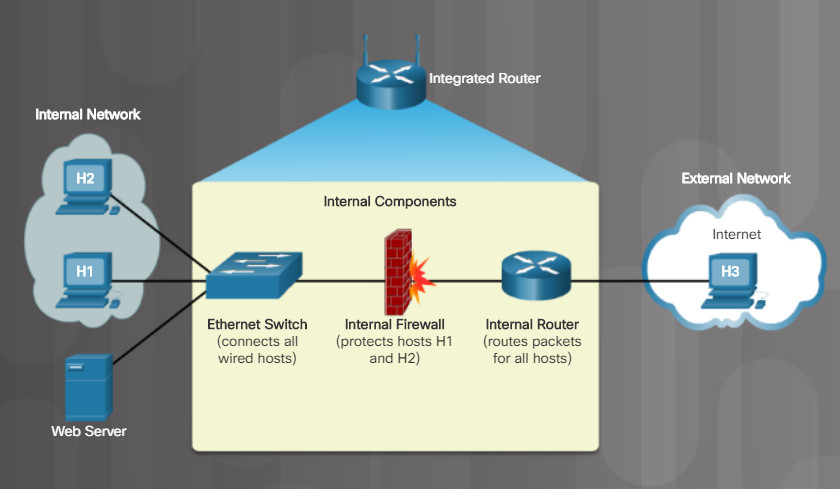
5.3.2.2 Firewalls
Firewalls use various techniques for determining what is permitted or denied access to a network segment, such as an Access Control List (ACL). This list is a file that the router uses which contains rules about data traffic between networks.
Note: On a secure network, if computer performance is not an issue, enable the internal operating system firewall for additional security. For example, in Windows 10 the firewall is called Windows Defender Firewall. Some applications might not operate properly unless the firewall is configured correctly for them.
5.3.2.3 – IDS and IPS
Intrusion Detection Systems (IDSs) passively monitor traffic on the network. Stand-alone IDS systems have largely disappeared in favor of Intrusion Prevention Systems (IPSs). But the detection feature of an IDS is still part of any IPS implementation. Figure 1 shows that an IDS-enabled device copies the traffic stream and analyzes the copied traffic rather than the actual forwarded packets. Working offline, it compares the captured traffic stream with known malicious signatures, similar to software that checks for viruses.
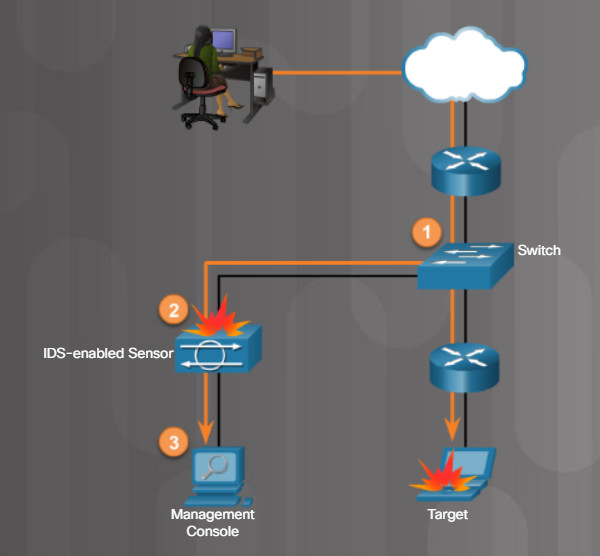
IDS Operation
An IPS builds upon IDS technology. However, an IPS device is implemented in inline mode. This means that all inbound and outbound traffic must flow through it for processing. As shown in Figure 2, an IPS does not allow packets to enter the target system without first being analyzed.
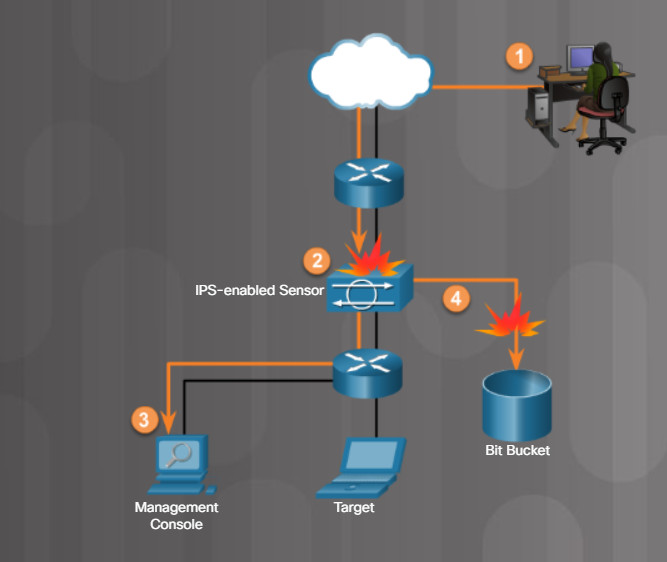
IPS Operation
The biggest difference between IDS and IPS is that an IPS responds immediately and does not allow any malicious traffic to pass, whereas an IDS allows malicious traffic to pass before it is addressed. However, a poorly configured IPS can negatively affect the flow of traffic in the network.
5.3.2.4 – UTMs
Unified Threat Management (UTM) is a generic name for an all-in-one security appliance. UTMs include all the functionality of an IDS/IPS as well as stateful firewall services. Stateful firewalls provide stateful packet filtering by using connection information maintained in a state table. A stateful firewall tracks each connection by logging the source and destination addresses, as well as source and destination port numbers.

Cisco ASA 5506-X with FirePOWER Services
In addition to IDS/IPS and stateful firewall services, UTMs also typically provide additional security services such as:
-
-
- Zero Day protection
- Denial of Service (DoS) and Distributed Denial of Service (DDoS) protection
- Proxy filtering of applications
- Email filtering for spam and phishing attacks
- Antispyware
- Network access control
- VPN services
-
These features can vary significantly, depending on the UTM vendor.
In the firewall market today, UTMs are now typically called next-generation firewalls. For example, the Cisco Adaptive Security Appliance in the figure offers the latest in next-generation firewall features.
5.3.2.5 – Endpoint Management Server
An endpoint management server is typically responsible for monitoring all the end devices in your network including desktops, laptops, servers, tablets, and any device connected to your network. An endpoint management server can restrict an end device’s connection to the network if the device does not meet certain predetermined requirements. For example, it can verify the devices has the latest operating system and anti-virus updates.
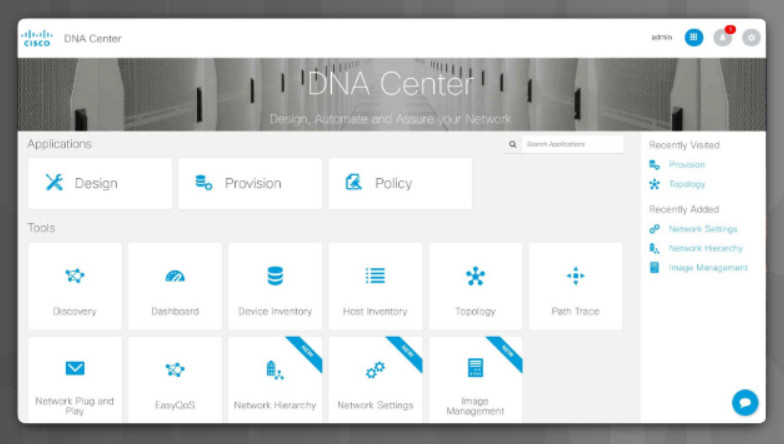
5.3.2.5 Endpoint Management Server
Cisco’s Digital Network Architecture (DNA) Center is an example of a solution that provides endpoint management. However, Cisco DNA is much more. It is a comprehensive management solution for managing all devices connected to the network so that the network administrator can optimize network performance to deliver the best possible user and application experience. The tools for managing the network are available for the Cisco DNA Center interface, as shown in the figure.
5.3.2.6 – Check Your Understanding – Security Devices
5.3.3 – Other Network Devices
5.3.3.1 – Legacy and Embedded Systems
Legacy systems are those computer and networking systems that are no longer supported but are still in operation in today’s networks. Legacy systems range from industrial control systems (ICSs) to computer mainframe systems, and a wide variety of networking devices such as hubs and bridges. Legacy systems are inherently vulnerable to security breaches because they cannot be upgraded or patched. One solution to alleviate some of the security risk is to air gap these systems. Air gapping is the process of physically isolating legacy systems from other networks and particularly the internet.

Programming an Embedded Microchip
Embedded systems are related to legacy systems in that many legacy systems have embedded microchips. These embedded microchips are typically programmed to provide dedicated input and output instructions to a specialized device. Examples of embedded systems in the home are things such as a thermostat, refrigerator, cooking range, dishwasher, washing machine, video game consoles, and smart TVs. Embedded systems are increasingly becoming connected to the internet. Security should be top of mind when the technician recommends and installs embedded systems.
5.3.3.2 – Patch Panel
A patch panel is commonly used as a place to collect incoming cable runs from the various networking devices throughout a facility, as shown in the figure. It provides a connection point between PCs and the switches or routers. A patch panel can be unpowered or powered. A powered patch panel can regenerate weak signals before sending them on to the next device.

5.3.3.2 Patch Panel
For safety, ensure that all cables are secured using cable ties or cable management products and are not crossing walkways or running under desks where they can be kicked.
5.3.3.3 – Power over Ethernet and Ethernet over Power

Cisco SG300-52P 52-port Gigabit PoE Managed Switch
Power over Ethernet (PoE) is a method for powering devices that do not have a battery or access to a power outlet. For example, a PoE switch (Figure 1) transfers small amounts of DC current over an Ethernet cable, along with the data, to power PoE devices. Low voltage devices that support PoE, such as wireless access points, surveillance video devices, and IP phones, can be powered from remote locations. Devices that support PoE can receive power over an Ethernet connection at distances up to 330 ft (100 m) away. Power can also be inserted in the middle of a cable run using a PoE injector, as shown in Figure 2.

PoE Injector
Ethernet over Power, or more commonly called powerline networking, uses existing electrical wiring to connect devices, as shown in Figure 3. The concept of “no new wires” means the ability to connect a device to the network wherever there is an electrical outlet. This saves the cost of installing data cables and without any additional cost to the electrical bill. Using the same wiring that delivers electricity, powerline networking sends information by sending data on certain frequencies. Figure 3 is of a powerline networking adapter plugged into an electrical outlet.

5.3.3.4 – Cloud-based Network Controller
A cloud-based network controller is a device in the cloud that allows network administrators to manage network devices. For example, a medium sized company with multiple locations might have hundreds of wireless APs. Managing these devices can be cumbersome without using some type of controller.
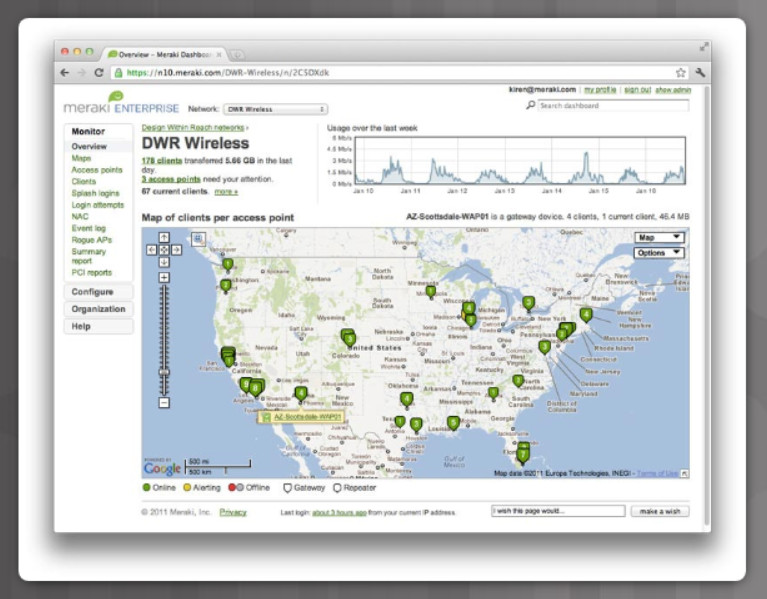
5.3.3.4 – Cloud-based Network Controller
For example, Cisco Meraki provides cloud-based networking that centralizes the management, visibility, and control of all Meraki devices into one dashboard interface, as shown in the figure. The network administrator is able to manage the wireless devices in multiple locations with the click of a mouse button.
5.3.3.5 – Check Your Understanding – Other Network Devices
5.4 – Network Cables
5.4.1 – Network Tools
5.4.1.1 – Video Explanation – Network Cable Tools
Click Play in the figure to view a video about network tools.
Click here to read the transcript of this video.
5.4.1.2 – Network Tools and Descriptions
Wire cutters are used to cut wires. Also known as side-cutters, these wire cutters are specifically designed to snip aluminum and copper wire.

Wire strippers are used to remove the insulation from wire so that it can be twisted to other wires or crimped to connectors to make a cable. Wire strippers typically come with a variety of notches for different wire gauges.
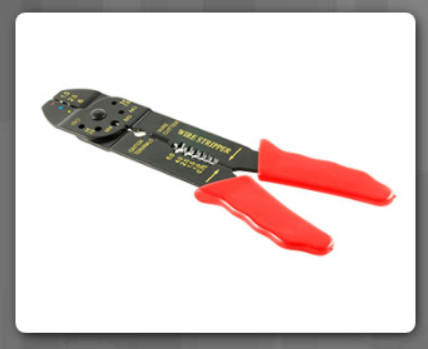
A crimper is used to attach connectors to wires. The crimper tool shown here can attach RJ-45 connectors to networking cables used for Ethernet and RJ-11 connectors to telephone cables used for land lines.
A punch down tool is used to terminate wire into termination blocks.

A multimeter is a device that can take many types of measurements. It measures AC/DC voltage, electric current, and other electrical characteristics to test the integrity of circuits and the quality of electricity in computer components.

A cable tester is used to check for wiring shorts, faults, or wires connected to the wrong pins.

A loopback adapter, also called a loopback plug, tests the basic functionality of computer ports. The adapter is specific to the port that you want to test. In networking, a loopback plug can be inserted in a computer NIC to test the send and receive functionality of the port.
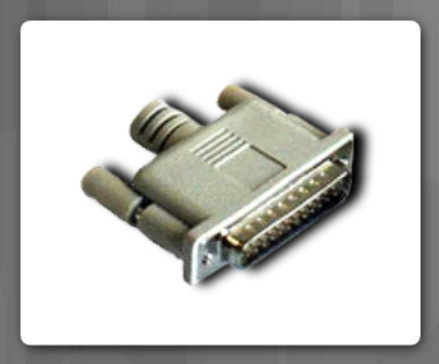
The tone generator and probe is a two-part tool used to trace the remote end of a cable for testing and troubleshooting. The tone generator applies a tone to the wire to be tested. On the remote end, the probe is used to identify the test wire. When the probe is in near proximity to the cable to which the toner is attached, the tone can be heard through a speaker in the probe.

Wi-Fi analyzers are mobile tools for auditing and troubleshooting wireless networks. Many Wi-Fi analyzers, like the Cisco Spectrum Expert Wi-Fi application, are robust tools designed for enterprise network planning, security, compliance, and maintenance. But Wi-Fi analyzers can also be used for smaller, wireless LANs. Technicians can see all available wireless networks in a given area, determine signal strengths, and position access points to adjust wireless coverage.

5.4.1.3 – Check Your Understanding – Network Tools
5.4.2 – Copper Cables and Connectors
5.4.2.1 – Cable Types
5.4.2.1 – Cable Types
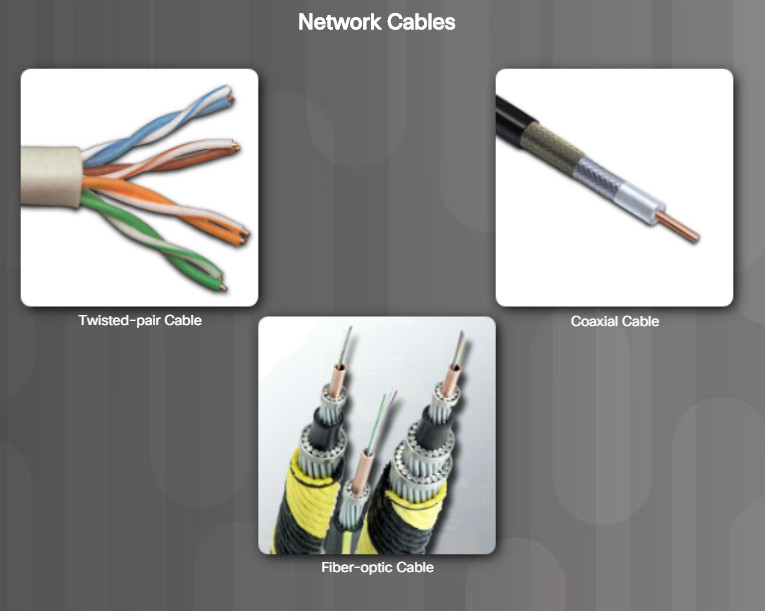
A wide variety of networking cables are available, as shown in the figure. Coaxial and twisted-pair cables use electrical signals over copper to transmit data. Fiber-optic cables use light signals to transmit data. These cables differ in bandwidth, size, and cost.
5.4.2.2 – Coaxial Cables
5.4.2.2 – Coaxial Cables
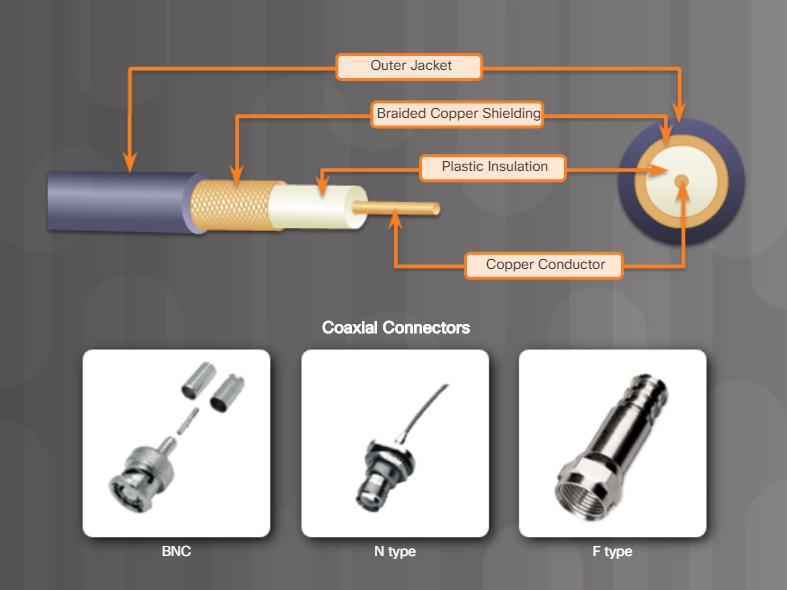
Coaxial cable is usually constructed of either copper or aluminum. It is used by both cable television companies and satellite communication systems. Coaxial cable is enclosed in a sheath or jacket and can be terminated with a variety of connectors, as shown in the figure.
Coaxial cable (or coax) carries data in the form of electrical signals. It provides improved shielding compared to unshielded twisted-pair (UTP), so it has a higher signal-to-noise ratio allowing it to carry more data. However, twisted-pair cabling has replaced coax in LANs because, when compared to UTP, coax is physically harder to install, more expensive, and harder to troubleshoot.
5.4.2.3 – Twisted-Pair Cables
Twisted-pair is a type of copper cabling used for telephone communications and most Ethernet networks. The pair is twisted to provide protection against crosstalk, which is the noise generated by adjacent pairs of wires in the cable. Unshielded twisted-pair (UTP) cabling is the most common variety of twisted-pair cabling.
As shown in Figure 1, UTP cable consists of four pairs of color-coded wires that have been twisted together and then encased in a flexible plastic sheath that protects from minor physical damage. UTP does not protect against electromagnetic interference (EMI) or radio frequency interference (RFI). EMI and RFI can be caused by a variety of sources including electric motors and fluorescent lights.
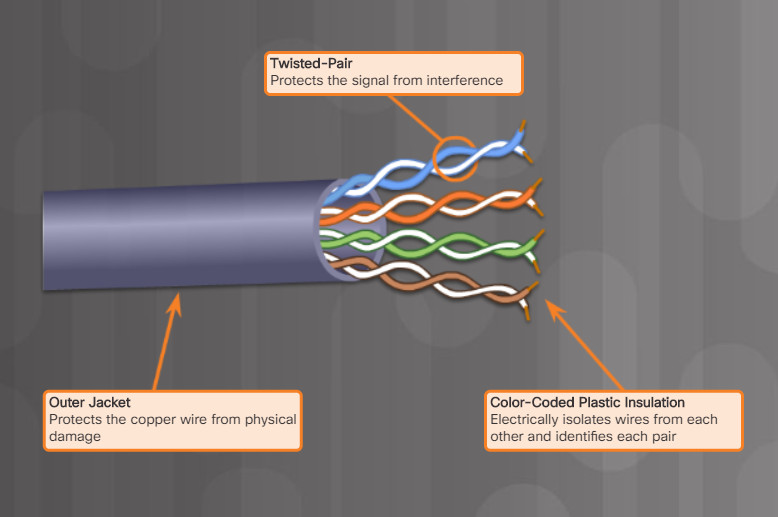
5.4.2.3: Twisted-Pair Cables – Figures 1
Shielded twisted-pair (STP) was designed to provide better protection against EMI and RFI. As shown in Figure 2, each twisted-pair is wrapped in a foil shield. The four pairs are then wrapped together in a metallic braid or foil.
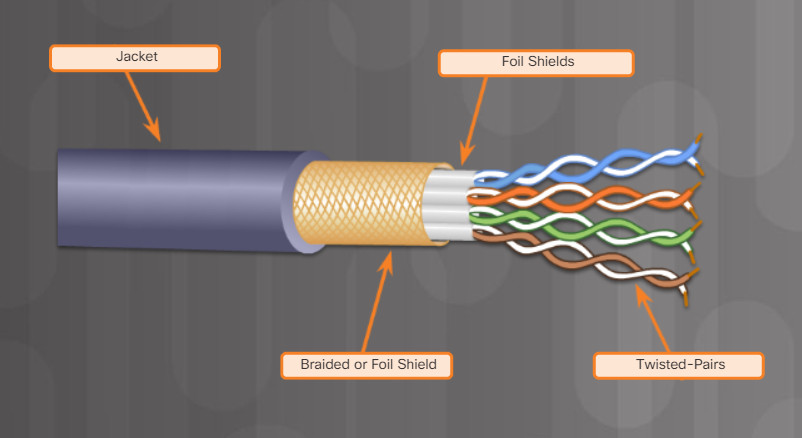
5.4.2.3: Twisted-Pair Cables – Figures 2
Both UTP and STP cables are terminated with an RJ-45 connector and plug into RJ-45 sockets, as shown in Figure 3. Compared to UTP cable, STP cable is significantly more expensive and difficult to install. To gain the full benefit of the shielding, STP cables are terminated with special shielded STP RJ-45 data connectors (not shown). If the cable is improperly grounded, the shield may act as an antenna and pick up unwanted signals.

5.4.2.3: Twisted-Pair Cables – Figures 3
5.4.2.4 – Twisted-Pair Category Ratings
Twisted-Pair Category Ratings
New or renovated office buildings often have some type of UTP cabling that connects every office. The distance limitation of UTP cabling used for data is 100 meters (330 feet). Click each UTP category for its speed rating and features.
Each category also comes in plenum rated versions, which are installed inside plenum areas of buildings. A plenum is any area that is used for ventilation, such as the area between the ceiling and a dropped ceiling. Plenum-rated cables are made from a special plastic that retards fire and produces less smoke than other cable types.
Click the buttons on the left to learn more about each type.
Cat 5 UTP
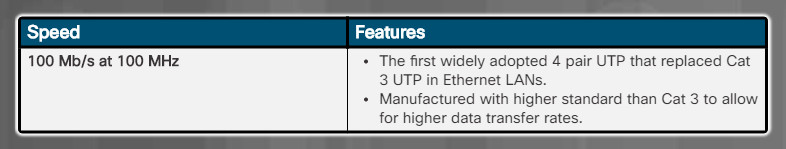
Cat 5 UTP
Cat 5e UTP
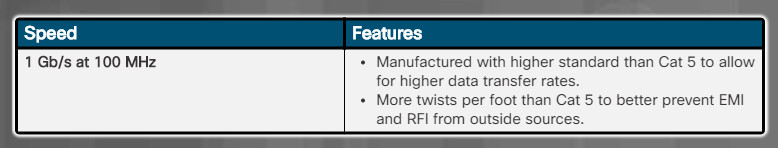
Cat 5e UTP
Cat 6 UTP
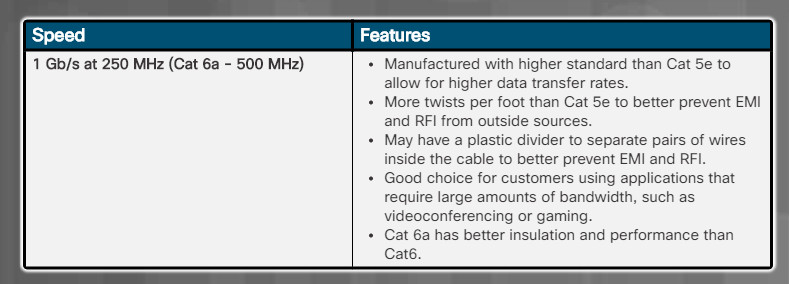
Cat 6 UTP
5.4.2.5-Twisted-Pair Wire Schemes
Instructions
There are two different patterns, or wiring schemes, called T568A and T568B. Each wiring scheme defines the pinout, or order of wire connections, on the end of the cable. Only the orange pair and green pair are reversed between T568A and T568B. Click each wiring scheme to compare the pinouts for the green and orange pairs.
On a network installation, one of the two wiring schemes (T568A or T568B) should be chosen and followed. It is important that the same wiring scheme is used for every termination in that project. If working on an existing network, use the wiring scheme that already exists.
T568A
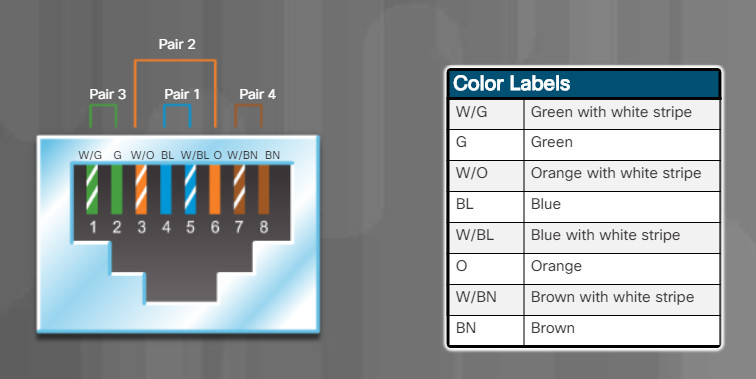
5.4.2.5 – Twisted-Pair Wire Schemes T568A
T568B
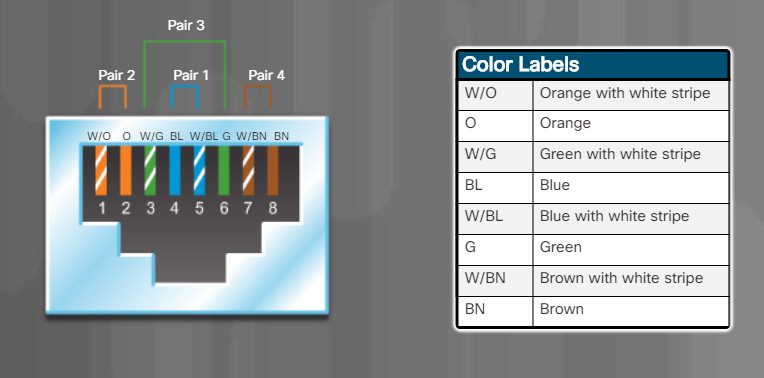
5.4.2.5-Twisted-Pair Wire Schemes T568A
5.4.2.6 – Activity – Cable Pinouts
Instructions
Correctly align the wire colors to build a T568A cable pinout. Drag each wire color to its correct placement on the RJ-45 image in the graphic.
Check Your Understanding – T568A Cable Pinouts
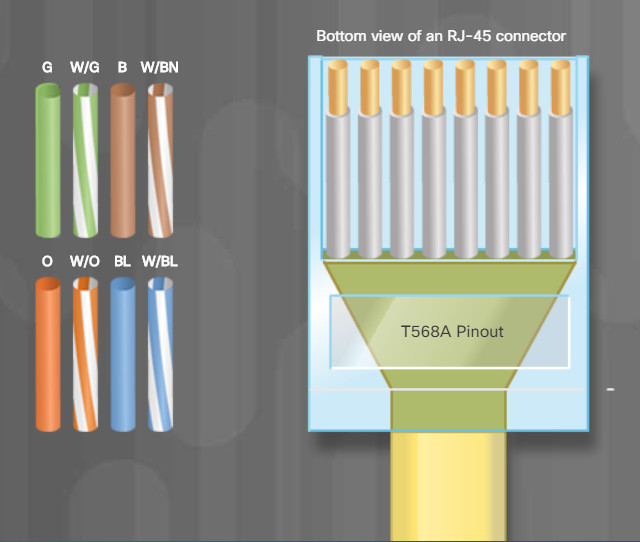
Check Your Understanding – T568A Cable Pinouts
Check Your Understanding – T568B Cable Pinouts
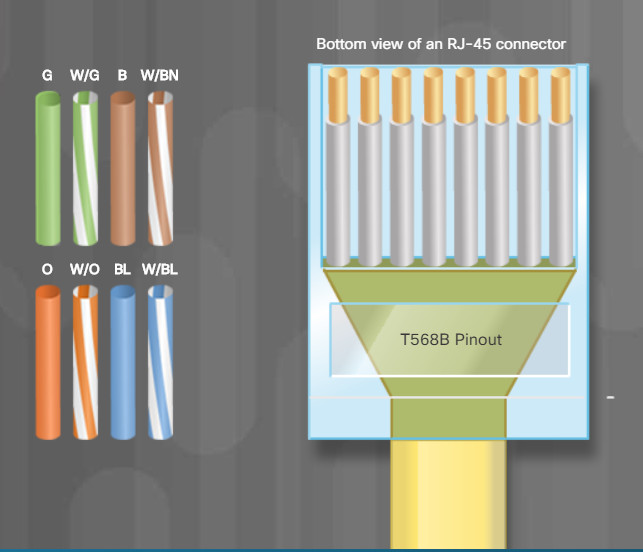
Check Your Understanding – T568B Cable Pinouts
5.4.2.7 – Video Demonstration – Build and Test a Network Cable
Click Play in the figure to view a demonstration of how to build a straight-through Ethernet cable.
Click here to read the transcript of this video.
5.4.2.8 – Lab – Build and Test a Network Cable
In this lab, you will build and test a straight-through UTP Ethernet network cable.
5.4.2.8 Lab – Build and Test a Network Cable
5.4.3 – Fiber Cables and Connectors
5.4.3.1 – Fiber-Optic Cables
Optical fiber is composed of two kinds of glass (core and cladding) and a protective outer shield (jacket). Click each component in the figure to learn more information.
Because it uses light to transmit signals, fiber-optic cable is not affected by EMI or RFI. All signals are converted to light pulses as they enter the cable, and converted back into electrical signals when they leave it. This means that fiber-optic cable can deliver signals that are clearer, can go farther, and have greater bandwidth than cable made of copper or other metals. Although the optical fiber is very thin and susceptible to sharp bends, the properties of the core and cladding make it very strong. Optical fiber is durable and is deployed in harsh environmental conditions in networks all around the world.
Typically a PVC jacket that protects the fiber against abrasion, moisture, and other contaminants. This outer jacket composition can vary depending on the cable usage.
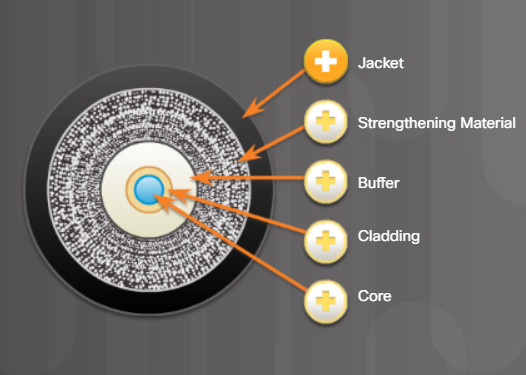
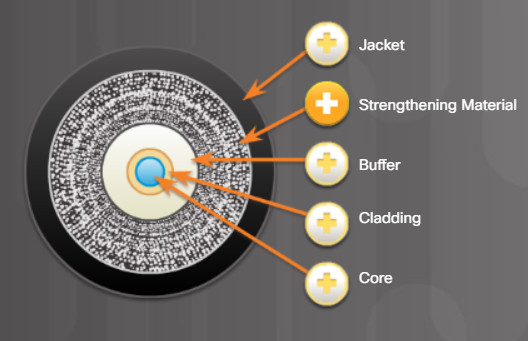
Surrounds the buffer, prevents the fiber cable from being stretched when it is being pulled. The material used is often the same material used to produce bulletproof vests.
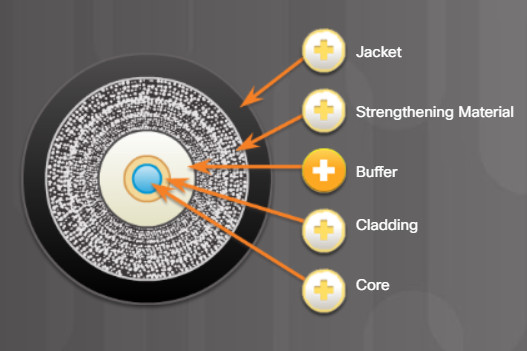
Used to help shield the core and cladding from damage.
Made from slightly different chemicals than those used to create the core. It tends to act like a mirror by reflecting light back into the core of the fiber. This keeps light in the core as it travels down the fiber.
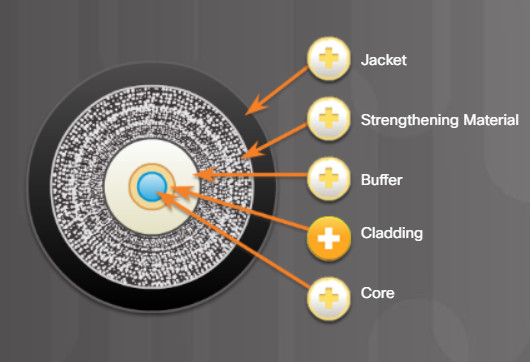
The core is actually the light transmission element at the center of the optical fiber. This core is typically silica or glass. Light pulses travel through the fiber core.
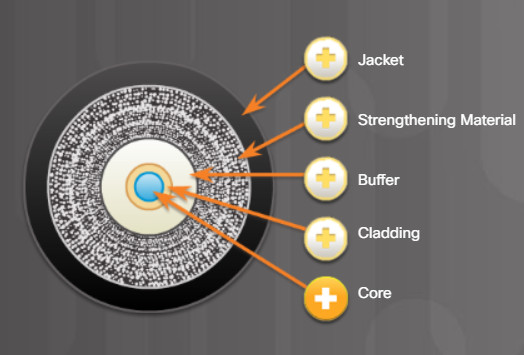

5.4.3.1 Fiber-Optic Cables
5.4.3.2 – Types of Fiber Media
Fiber-optic cables are broadly classified into two types:
Single-mode fiber (SMF) – Consists of a very small core and uses laser technology to send a single ray of light, as shown in Figure 1. Popular in long-distance situations spanning hundreds of kilometers, such as those required in long haul telephony and cable TV applications.
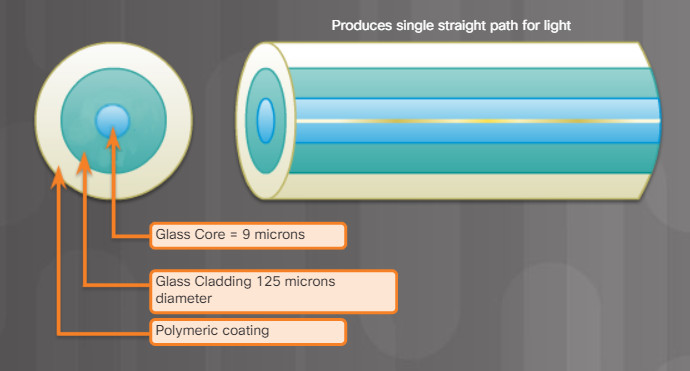
5.4.3.2 – Types of Fiber Media Single Mode
- Small core
- Less dispersion
- Suited for long distance applications
- Uses lasers as the light source
- Commonly used with campus backbones for distances of several thousand meters
Multimode fiber (MMF) – Consists of a larger core and uses LED emitters to send light pulses. Specifically, light from an LED enters the multimode fiber at different angles, as shown in Figure 2. Popular in LANs because they can be powered by low-cost LEDs. It provides bandwidth up to 10 Gb/s over link lengths of up to 550 meters.
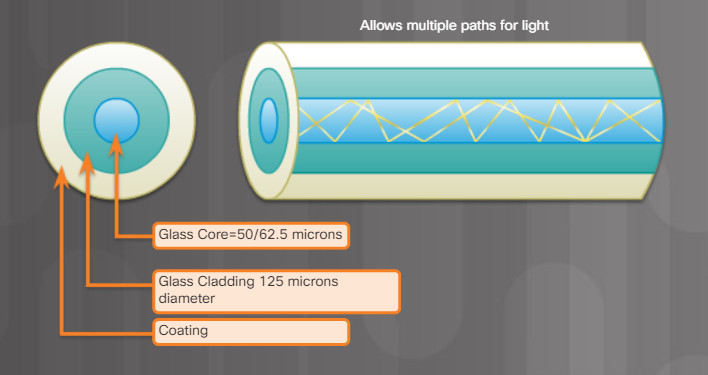
5.4.3.2 – Types of Fiber Media Multimode
- Larger core than single mode cable
- Allows greater dispersion and therefore, loss of signal
- Suited for long distance applications, but shorter than single mode
- Uses LEDs as the light source
- Commonly used with LANs or distances of a couple hundred meters within a campus network
5.4.3.3 – Fiber-Optic Connectors
An optical fiber connector terminates the end of an optical fiber. A variety of optical fiber connectors are available. The main differences among the types of connectors are dimensions and methods of coupling. Businesses decide on the types of connectors that will be used, based on their equipment.
Click each connector in the figure to learn about the most popular types of fiber-optic connectors.
For fiber standards with FX and SX in the name, light travels in one direction over optical fiber. Therefore, two fibers are required to support the full duplex operation. Fiber-optic patch cables bundle together two optical fiber cables and terminate them with a pair of standard single fiber connectors. Some fiber connectors accept both the transmitting and receiving fibers in a single connector known as a duplex connector, as shown in the Duplex Multimode LC Connector in the figure.
For fiber standards with BX in the name, light travels in both directions on a single strand of fiber. It does this through a process called Wave Division Multiplexing (WDM). WDM is a technology that separates the transmit and receive signals inside the fiber.
For more information on fiber standards, search for “gigabit ethernet fiber-optic standards”.
One of the first connector types used. The connector locks securely with a “twist-on/twist-off” bayonet style mechanism.

Sometimes referred to as square connector or standard connector. It is a widely adopted LAN and WAN connector that uses a push-pull mechanism to ensure positive insertion. This connector type is used with multimode and single-mode fiber.

A smaller version of the fiber-optic SC connector. It is sometimes called a little or local connector and is quickly growing in popularity due to its smaller size.

Similar to a LC simplex connector, but using a duplex connector.

5.4.3.4 – Check Your Understanding – Fiber Cables and Connectors
5.4.3.4 – Check Your Understanding – Fiber Cables and Connectors
5.5 – Summary
5.5.1 – Conclusion
5.5.1.1 – Chapter 5: Network Concepts
In this chapter, you learned about the different types of components, devices, services, and protocols that comprise a network. How all of these elements are arranged forms different network topologies such as PANs, LANs, VLANS, WLANs, and VPNs. There are also different ways in which computers and networks are connected to the Internet. For example, there are wired connections like DSL, cable, and fiber optics, and wireless connections such as satellite and cellular services. It is even possible to connect network devices to the Internet through a cell phone using tethering.
You learned about the four layers of the TCP/IP model; network access, internet, transport, and application. Each layer performs the functions necessary for data transmission over a network. Each layer also has specific protocols that are used to communicate between peers.
The chapter covered different wireless technologies and standards beginning with a comparison of the WLAN protocols and IEEE 802.11 standards. These standards use two radio frequency bands of 5 GHz (802.11a and 802.11ac) and 2.4GHz ( 802.11b, 802.11g, and 802.11n). Other wireless protocols for close proximity connectivity like Bluetooth, and NFC were discussed as well as standards for smart home applications, such as Zigbee, which is an open standard based on IEEE 802.15.4 and Z-Wave, which is a proprietary standard. You also learned about the evolution of the cellular generations from 1G, which supported only analog voice, through 5G which has enough bandwidth to support AR and VR.
Many types of network hardware devices were discussed. NICs provide physical connectivity for end devices, can be wired or wireless, and install inside the computer in an expansion slot or outside connected via USB. You learned that repeaters and hubs operate at layer 1and repeat network signals, and that switches and routers operate at Layers 2 and 3 respectively with switches forwarding frames based on MAC address and routers forwarding packets based on IP address.
Networks also include security devices such as firewalls, IDS, IPS, and UTM systems. Firewalls protect data and equipment on a network from unauthorized access. IDSs passively monitor traffic on the network while IPSs actively monitor traffic and respond immediately, not allowing any malicious traffic to pass. UTMs are all-in-one security appliances and include all the functionality of an IDS/IPS as well as stateful firewall services.
Finally in this chapter, you learned about network cables and connectors and the tools used by network technicians to test and repair them. Cables come in different sizes and costs and differ in the maximum bandwidth and distances that they support. Coax and twisted pair cables carry data in the form of electrical signals while fiber optic cables use light. Twisted pair cables use two different wiring schemes, T568A and T568B, which defines the order of the individual wire connections at the end of the cable. You built and tested a straight-through UTP Ethernet network cable using either the T568A or T568B standards.

Great work, thanks for this material explaining this chapter. I did enjoy my STUDY.
Pls. On an important note, l suggest that video explainations be pasted along side to aid efficacy in studies.
Once again THANKS.